In brief: Security researchers discovered a particularly alarming form of malware that tricks users into downloading an infected app to propagate. While the attack vector is common, the insidious nature of the malicious code makes it unique. It targets and steals crypto wallet security codes using OCR to scan images for mnemonic passphrases.

A sophisticated new strain of Android malware has emerged from Korea. It targets cryptocurrency wallets by exploiting users' mnemonic keys. McAfee Labs researcher SangRyol Ryu came across the malware after tracing data stolen by malicious apps to rogue servers and gaining access.
The malicious software, dubbed SpyAgent, uses cunning tactics to infiltrate devices and exfiltrate sensitive information, including photos that may contain wallet recovery phrases. SpyAgent disguises itself as legitimate apps, ranging from banking and government services to streaming platforms and utility software. So far, McAfee has identified over 280 of these fake applications.
Once the victim downloads a SpyAgent-infected app, the malware springs into action, establishing a connection with a command and control (C2) server that allows attackers to issue instructions remotely. It then harvests text messages, contact lists, and stored images from the infected device.
What sets this malware apart is its use of optical character recognition (OCR) technology to scan images for mnemonic keys – the 12-word phrases used to recover cryptocurrency wallets. Using mnemonic phrases is rising in crypto-wallet security, as they are easier to remember than a long string of random characters.
SpyAgent has also proved to be wily with its efforts to avoid detection. It diverts the victim's attention from a possible problem with the phone using endless loading screens or brief blank displays.
The malware's creators have proven adept at expanding SpyAgent's reach. It initially targeted users in Korea. However, the malware recently spread to the United Kingdom. It has also transitioned from simple HTTP requests to WebSocket connections, enabling real-time, two-way communication with the C2 server. It has clever techniques to avoid detection from security researchers, including string encoding and function renaming.
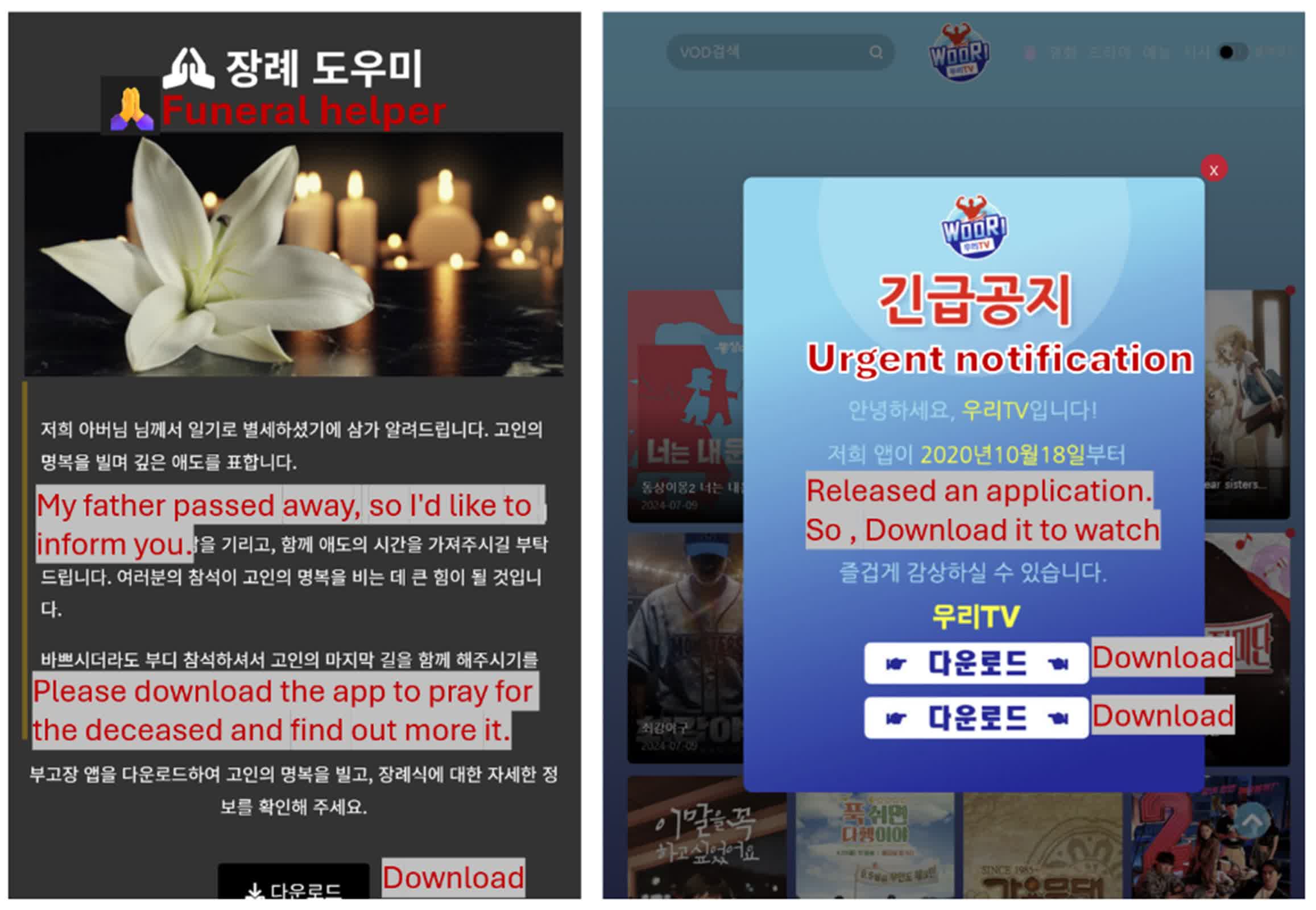
SpyAgent makes its way onto victims' devices largely through phishing campaigns. Attackers use social engineering tactics to lure victims into clicking malicious links. These links direct users to convincing fake websites that prompt downloading the malware-laden APK file. The campaigns are proving particularly successful when combined with stolen contact data.
"These phishing messages, seemingly sent by a familiar contact, are more likely to be trusted and acted upon by recipients," Ryu wrote. "For instance, an obituary notice appearing to come from a friend's number could be perceived as authentic, greatly raising the likelihood of the recipient engaging with the scam, especially compared to phishing attempts from unknown sources."
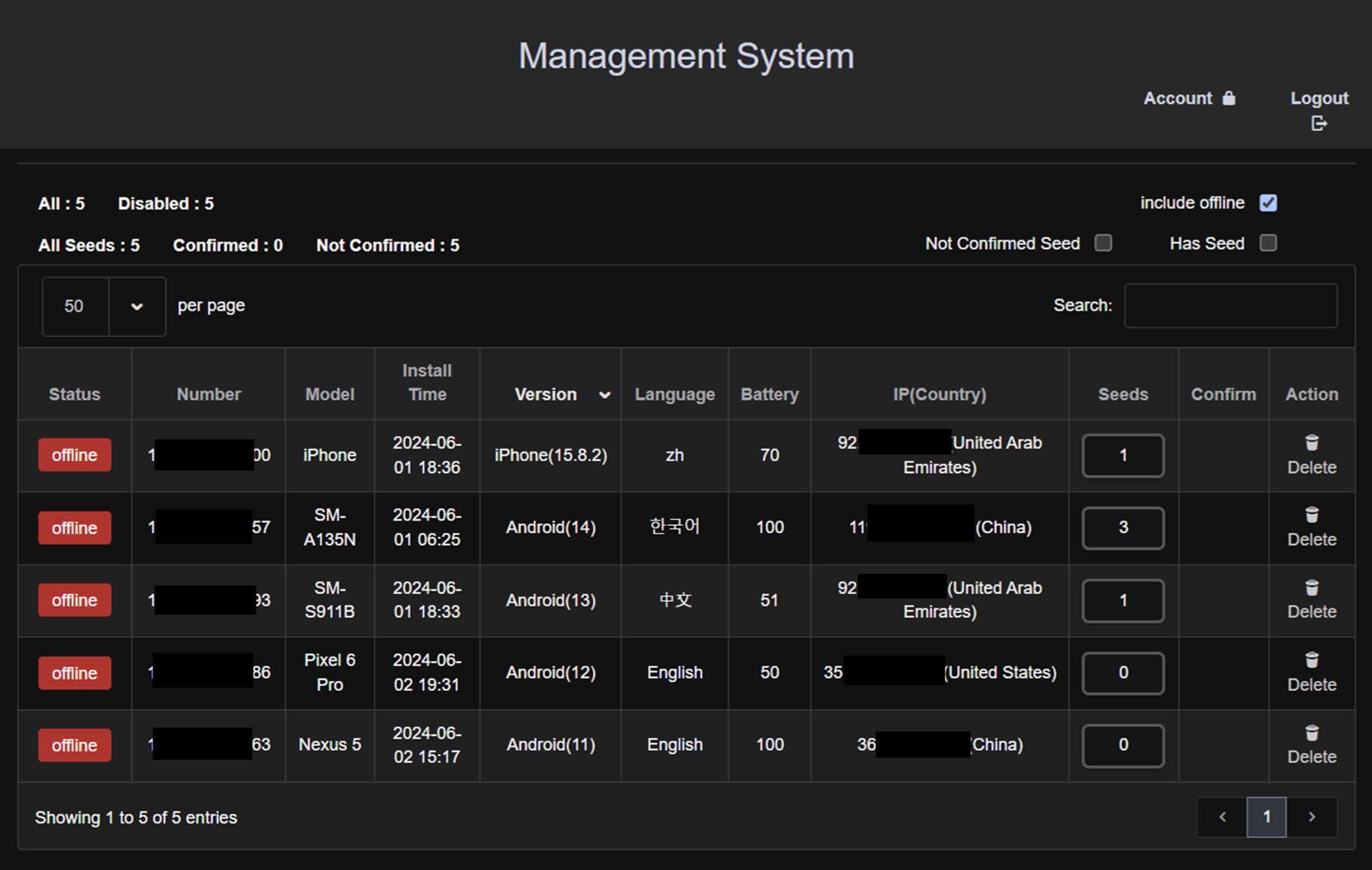
SpyAgent's backend operations are very sophisticated, as the malware's scale indicates. For instance, researchers discovered admin pages designed for managing compromised devices. It also uses Python and Javascript on the server side to process the stolen data, which is then organized and managed through an administrative panel.
Another indication of its sophistication is how quickly it developed legs. The first sighting of SpyAgent was only earlier this year and only in Korea. It has already spread to UK users.
Security researchers hope to stamp out SpyAgent, or at least contain it, now that they know how it works. However, its creators continue refining their techniques, and McAfee believes they are currently developing an iOS version.
New Android malware uses OCR to steal crypto wallet keys from images