A hot potato: The Google Play Store is notorious for harboring apps that contain malware, adware, or some flavor of spyware or fleeceware. A lesser-known fact is that hackers are increasingly targeting pre-installed apps for their misdeeds, and researchers are trying to raise awareness about this growing trend. Millions of affordable Android phones come with numerous pre-installed apps, and hackers only need to subvert one. However, addressing this issue is significantly more challenging than dealing with rogue apps that find their way into the Play Store.

Last month, we learned that malware had been discovered in 60 Android apps with over 100 million downloads – another black eye for the mobile operating system that has an estimated three billion active users worldwide. Malicious developers regularly exploit various loopholes in Google's app vetting process to create apps that steal login credentials or fleeceware that squeeze as much as $400 million per year from users by tricking them into signing up for expensive in-app subscriptions.
However, researchers at Trend Micro are sounding the alarm about the growing trend of Android devices that come with malicious software pre-installed. While you can easily remove an app you've downloaded from the Play Store, addressing malware embedded in system apps or device firmware is a significantly more challenging task.

Android's open nature allows manufacturers to create a wide range of phone models and target price-conscious consumers with more affordable options. However, it also opens the door for hackers to sneak in malicious code before those devices even leave the factory floor. This risk also applies to other Android devices, including smartwatches, tablets, set-top boxes, and smart TVs.
Senior Trend Micro researcher Fyodor Yarochkin says pre-installed malware has become much more common in recent years, partly due to a race to the bottom among mobile firmware developers. Once selling firmware became unprofitable, many developers began offering it for free.
As expected, there's a catch to this new business model – many of the firmware images analyzed by Trend Micro contained bits of code described as "silent plugins." The researchers have discovered over 80 flavors so far, but only a few have seen widespread distribution. The more popular ones are being sold underground and promoted on Facebook, YouTube, and various blogs.
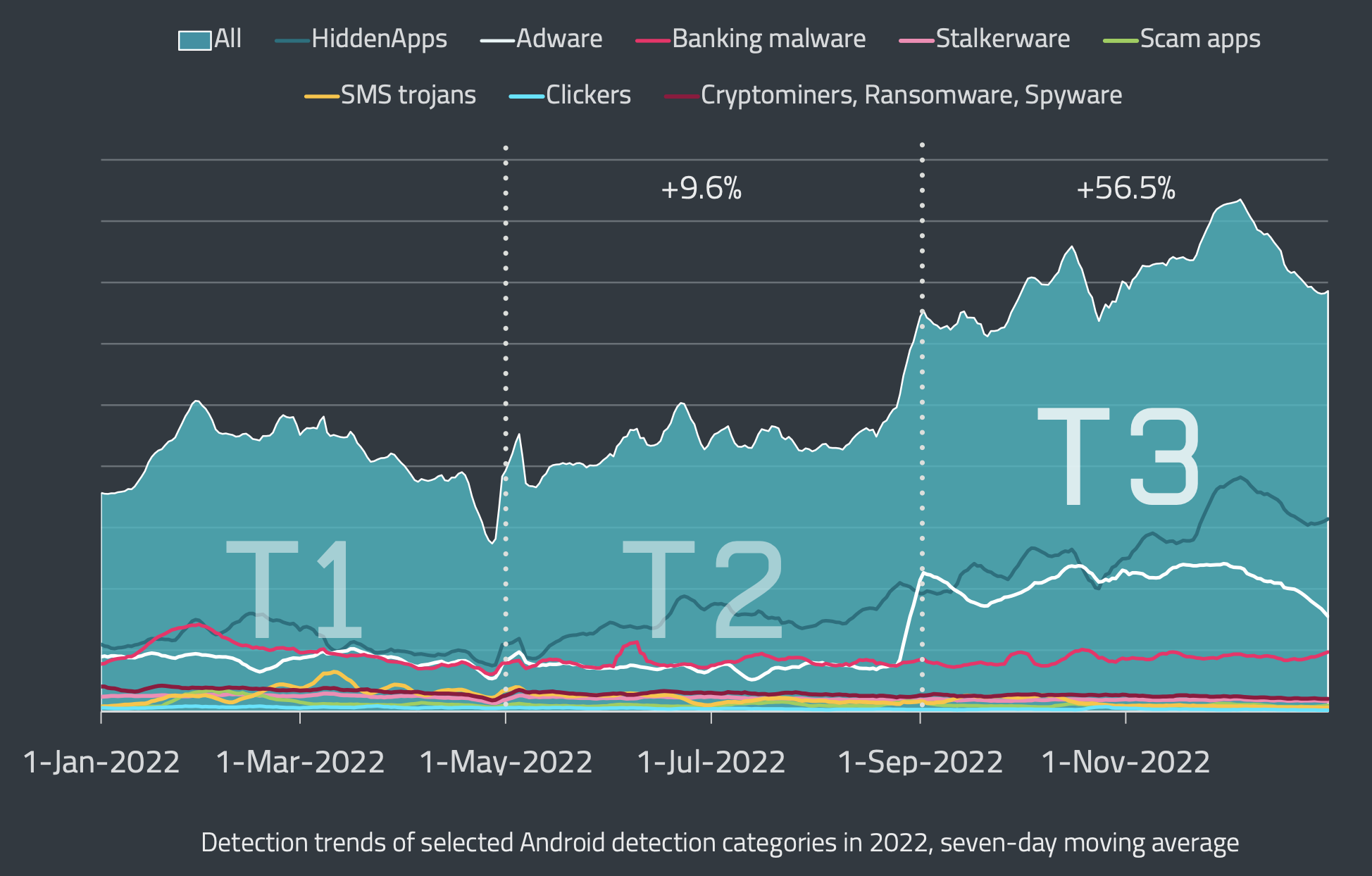
Data: ESET Threat Intelligence
Some of these plugins allow cyber criminals to "rent out" Android devices for up to five minutes at a time and use them to steal login credentials or other sensitive user information. Others are capable of downloading additional malware onto the infected device.
Researchers estimate that millions of infected devices are in use worldwide, with a large portion concentrated in Eastern Europe and Southeast Asia. Interestingly, the criminals themselves claim that 8.9 million Android devices are loaded with their silent plugins.
Trend Micro confirmed the presence of malware in phones from at least 10 vendors, most of them Chinese. The firm suspects an additional 40 vendors are affected, but researchers are more interested in determining where along the supply chain the infection is most likely to occur.
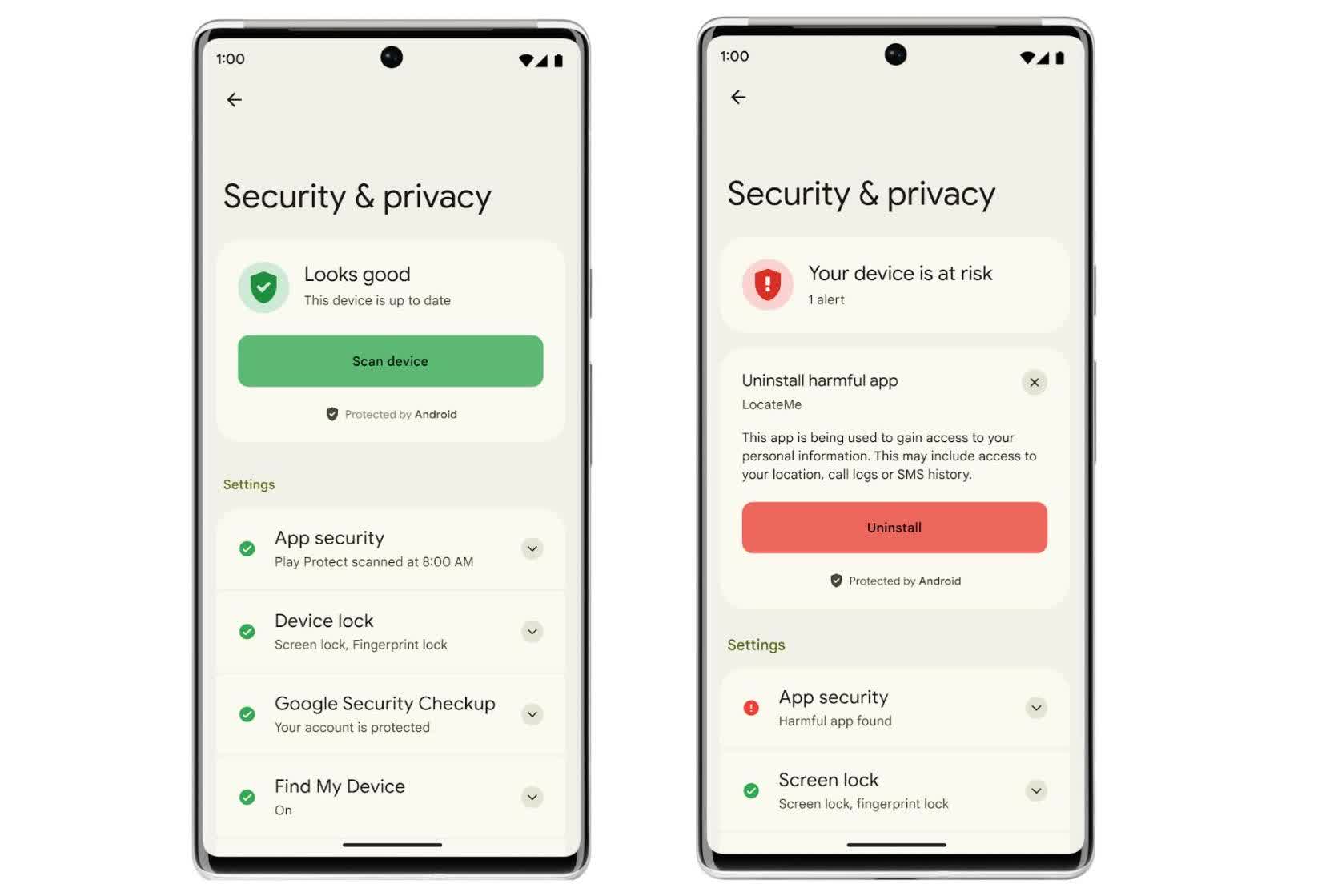
Play Protect can usually spot rogue apps from the Play Store, but what about silent plugins?
Google has been aware of pre-installed Android malware for years, but it cannot easily solve the problem due to its limited control over the complex OEM Android supply chain. Cheaper phones tend to use the Android Open Source Platform (AOSP) and come with anywhere between 100 and 400 pre-installed apps – all it takes is infecting one of them.
It also doesn't help that as many as 225 device manufacturers regularly leave diagnostic software on Android phones, which essentially enables backdoor remote access for spyware and censorship tools. This behavior has been observed in numerous Chinese brands as well as big names like Oppo, OnePlus, Realme, and Xiaomi. Some, like Chinese-owned Gigaset, which sells phones in the EU, were found to have buried a malware auto-installer in a system update app.
Back in 2019, Google Project Zero researcher Maddie Stone revealed the existence of an SMS and ad fraud botnet called Chamois that had affected at least 21 million Android devices in previous years through pre-installed malware. The company discovered that vendors would often unknowingly incorporate Chamois code into their Android distributions because they were easily fooled into believing it was a legitimate ad service.
Also read: Does Android need saving? If yes, here's how to do it.
Since then, Google has invested significant effort in refining Google Play Protect and expanding its capabilities to monitor pre-installed apps on Android devices for malicious behavior. That said, hackers continue to find ways to bypass these protections, and they're even developing lucrative business models around it on the dark web. A recent Kaspersky analysis found that accessing these malicious services costs anywhere between $2,000 and $20,000.
As for protecting yourself, Yarochkin recommends opting for higher-end devices and sticking to brands like Samsung and Google, which supposedly have better supply chain security. Most mobile antivirus apps are ineffective against real security threats, so it's best not to rely on them, unless you want to end up like thousands of users who downloaded password-stealing malware disguised as antivirus tools.
Image credit: Luis Andrés Villalón
https://www.techspot.com/news/98667-millions-android-phones-come-pre-installed-malware-there.html