What just happened? Meta recently released vulnerability information regarding several hundred malicious Android and iOS applications. All of the apps were listed in Apple and Google app stores and disguised as legitimate software. But despite their descriptions and reviews, they were designed with the end goal of stealing user information.
Both Apple and Google were alerted to the issue after Meta researchers found more than 400 malicious apps across their respective app platforms. The apps in question provided users the option to log into or access an app's additional features via their Facebook account. Once entered, the user's credentials were stolen and used to provide unauthorized access to the victim's data.
The design, implementation, and user experience guides for including Facebook login functionality in a new app is openly available for developers in Facebook's developer documentation. The login function is well known and used by legitimate apps such as Pinterest and Instagram. The illegitimate apps named in Meta's report relied on this function recognition as one of many ways to lure users into a false sense of security and legitimacy when logging in.

Meta's statement described how malicious developers exploited the popular login functionality. Once created, fake reviews would be posted to build initial credibility or bury unwanted negative reviews. Unsuspecting users would then install the applications and enter their Facebook credentials to access the app's content or connect it to their Facebook account. At this point, the app's malware would obtain the user's submitted login credentials, making all of the user's account information, photos, etc. accessible by unauthorized third parties.
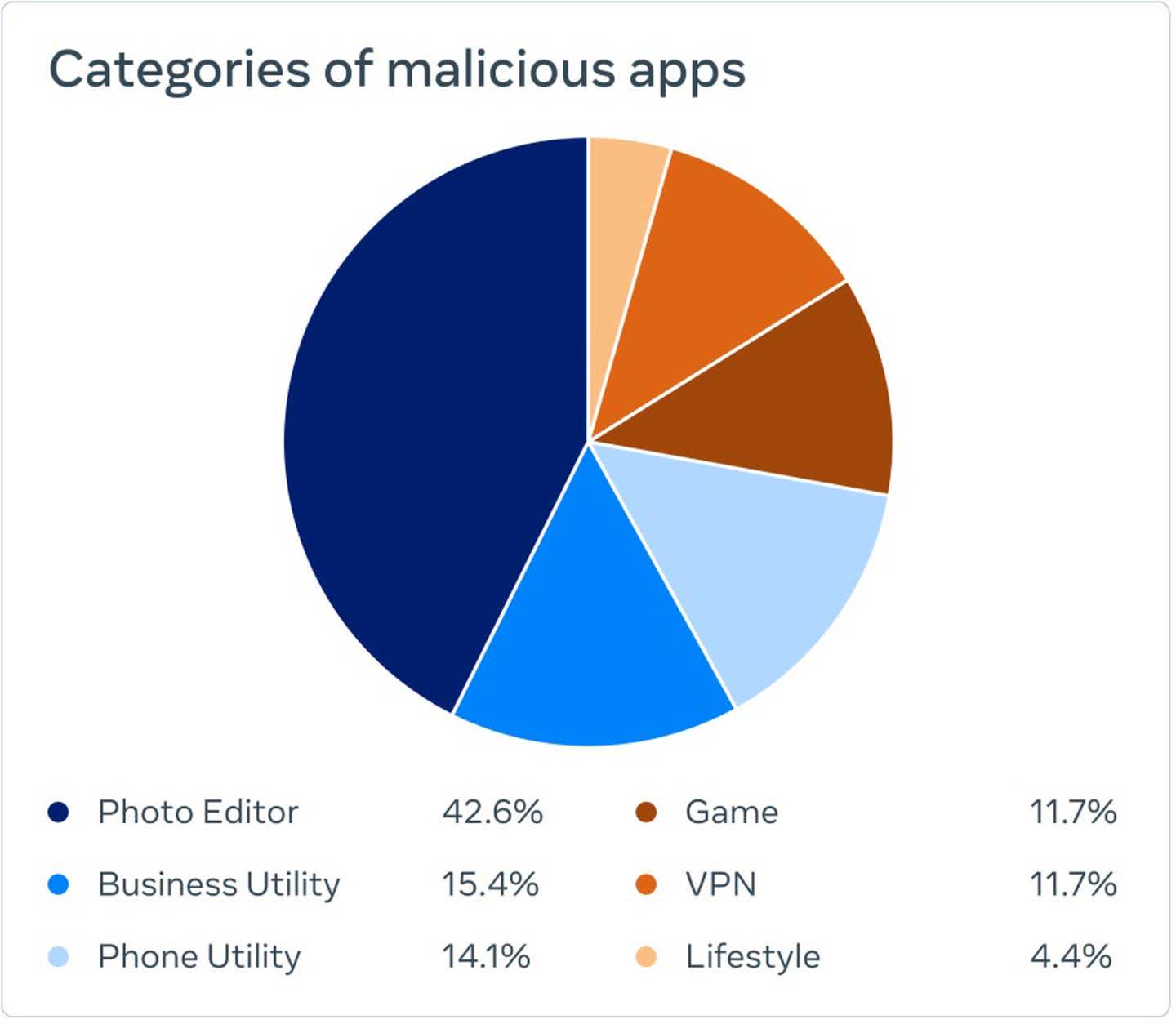
The apps did what they advertised, helping to further establish their credibility as a valid app. According to Meta's findings, photo filter apps made up more than 40 percent of all identified malicious apps. The other 60 percent spanned various phone, business, gaming, VPN, and lifestyle categories.
The announcement provides readers with several questions and telltale signs that can help to identify fraudulent applications. It also provides a GitHub link where developers and security engineers can review potential threat indicators. Any affected users are advised to reset their passwords, enable two factor authentication, and turn on logging to monitor unwanted login attempts.
