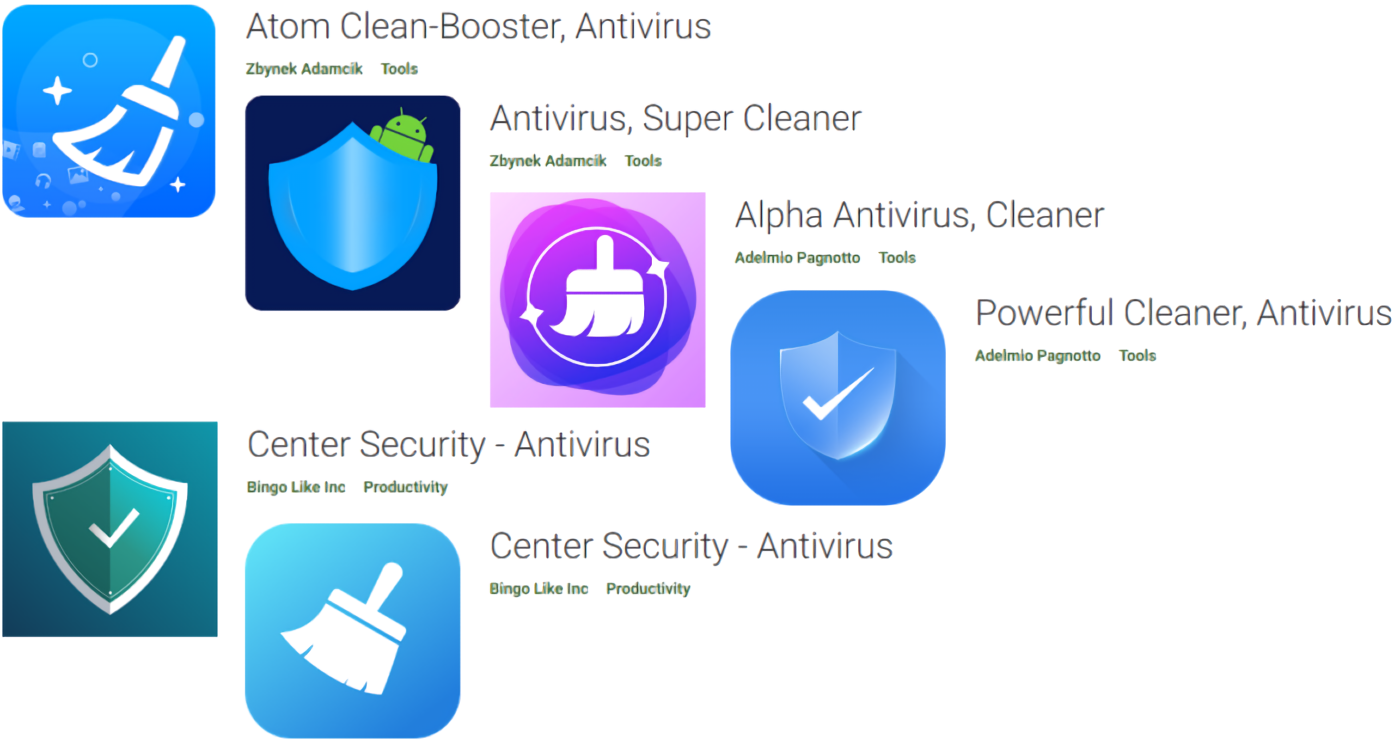
Facepalm: It's starting to feel like Google is wasting its breath when warning people about the dangers of sideloading apps, given how many malware-infested programs slip onto the Play Store. Six more were discovered and removed after they were found to be stealing login credentials while masquerading as antivirus applications.
Check Point security researchers said the six apps had been downloaded over 15,000 times before Google removed them from its store following the cybersecurity firm's disclosure. While users thought they were downloading mobile antivirus apps, they were actually installing the Sharkbot Android stealer, ironically.
Sharkbot works by convincing victims to enter their credentials in windows that mimic input forms, often when it detects banking apps are opened. It can also steal information by keylogging, intercepting SMS messages, and gaining full remote access.
Once a person enters their username and password, the details are sent to a malicious server and used to access accounts such as banks, social media, emails, and more.
Most of the victims came from the UK and Italy. Interestingly, the malware used geofencing to identify and ignore users in China, India, Romania, Russia, Ukraine, or Belarus.
The apps were able to slip past the Play Store safeguards because their malicious behavior wasn't activated until after someone downloaded one and it communicated with the server, writes ZDNet.
The Sharkbot-infested applications were removed from the Google Play Store in March, though they will likely still be available on other storefronts.
It was only two weeks ago when researchers at French mobile security company Pradeo revealed that an app named Craftsart Cartoon Photo Tools contained a version of an Android trojan malware called Facestealer. It was able to steal mobile users' Facebook login credentials and had been downloaded over 100,000 times before Google removed it.