andreyu
Posts: 14 +0
Hello,
Like many others here I too have the caught the Sirefef virus (at least that's what MSE says it is before the computer abruptly restarts).
I have Windows Vista Professional 32.
I ran farbar, I'm pasting the logs below.
Thank you for your help, it's greatly appreciated.
--------------------------------------------------------------------------------
FRST.TXT
Scan result of Farbar Recovery Scan Tool (FRST written by Farbar) Version: 08-08-2012
Ran by SYSTEM at 08-08-2012 09:24:24
Running from G:\
Windows Vista (TM) Business (X86) OS Language: English(US)
The current controlset is ControlSet001
========================== Registry (Whitelisted) =============
HKLM\...\Run: [PTHOSTTR] C:\Program Files\Hewlett-Packard\HP ProtectTools Security Manager\PTHOSTTR.EXE /Start [145184 2007-01-09] (Hewlett-Packard Development Company, L.P.)
HKLM\...\Run: [SynTPEnh] C:\Program Files\Synaptics\SynTP\SynTPEnh.exe [827392 2007-01-12] (Synaptics, Inc.)
HKLM\...\Run: [SunJavaUpdateSched] "C:\Program Files\Common Files\Java\Java Update\jusched.exe" [254696 2012-01-18] (Sun Microsystems, Inc.)
HKLM\...\Run: [QlbCtrl] %ProgramFiles%\Hewlett-Packard\HP Quick Launch Buttons\QlbCtrl.exe /Start [163840 2007-05-02] ( Hewlett-Packard Development Company, L.P.)
HKLM\...\Run: [HP Software Update] c:\Program Files\Hp\HP Software Update\HPWuSchd2.exe [49152 2005-02-16] (Hewlett-Packard Co.)
HKLM\...\Run: [HP Health Check Scheduler] c:\Program Files\Hewlett-Packard\HP Health Check\HPHC_Scheduler.exe [75008 2008-10-08] (Hewlett-Packard)
HKLM\...\Run: [atchk] "C:\Program Files\Intel\AMT\atchk.exe" [408088 2007-11-09] (Intel Corporation)
HKLM\...\Run: [NeroFilterCheck] C:\Windows\system32\NeroCheck.exe [155648 2001-07-09] (Ahead Software Gmbh)
HKLM\...\Run: [PAC7302_Monitor] C:\Windows\PixArt\PAC7302\Monitor.exe [319488 2006-11-03] (PixArt Imaging Incorporation)
HKLM\...\Run: [hpWirelessAssistant] C:\Program Files\Hewlett-Packard\HP Wireless Assistant\HPWAMain.exe [480560 2007-10-03] (Hewlett-Packard Development Company, L.P.)
HKLM\...\Run: [StartCCC] "C:\Program Files\ATI Technologies\ATI.ACE\Core-Static\CLIStart.exe" MSRun [98304 2009-08-13] (Advanced Micro Devices, Inc.)
HKLM\...\Run: [IDProtect Monitor] "C:\Program Files\Athena\IDProtect Client\Utils\IDProtect Monitor.exe" [323664 2010-12-01] (Athena Smartcard Solutions)
HKLM\...\Run: [SoundMAXPnP] C:\Program Files\Analog Devices\Core\smax4pnp.exe [1183744 2007-02-21] (Analog Devices, Inc.)
HKLM\...\Run: [Adobe ARM] "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" [843712 2012-01-02] (Adobe Systems Incorporated)
HKLM\...\Run: [AdobeAAMUpdater-1.0] "C:\Program Files\Common Files\Adobe\OOBE\PDApp\UWA\UpdaterStartupUtility.exe" [500208 2010-03-05] (Adobe Systems Incorporated)
HKLM\...\Run: [AdobeCS5ServiceManager] "C:\Program Files\Common Files\Adobe\CS5ServiceManager\CS5ServiceManager.exe" -launchedbylogin [406992 2010-02-21] (Adobe Systems Incorporated)
HKLM\...\Run: [SwitchBoard] C:\Program Files\Common Files\Adobe\SwitchBoard\SwitchBoard.exe [517096 2010-02-19] (Adobe Systems Incorporated)
HKLM\...\Run: [MSC] "c:\Program Files\Microsoft Security Client\msseces.exe" -hide -runkey [931200 2012-03-26] (Microsoft Corporation)
HKU\Irina\...\Run: [Messenger (Yahoo!)] "C:\PROGRA~1\Yahoo!\MESSEN~1\YahooMessenger.exe" -quiet [6497592 2012-01-03] (Yahoo! Inc.)
HKU\Irina\...\Run: [YSearchProtection] C:\Program Files\Yahoo!\Search Protection\YspService.exe [296248 2010-06-13] (Yahoo! Inc.)
HKU\Irina\...\Run: [swg] "C:\Program Files\Google\GoogleToolbarNotifier\GoogleToolbarNotifier.exe" [39408 2009-04-23] (Google Inc.)
Winlogon\Notify\DeviceNP: DeviceNP.dll (Hewlett-Packard Limited)
Winlogon\Notify\ScCertProp: wlnotify.dll [X]
Tcpip\Parameters: [DhcpNameServer] 192.168.1.1
AppInit_DLLs: APSHook.dll
Lsa: [Notification Packages] SbHpNp
scecli
ASWLNPkg
================================ Services (Whitelisted) ==================
2 ASBroker; C:\Program Files\Hewlett-Packard\IAM\Bin\ASWLNPkg.dll [74240 2007-02-06] (Cognizance Corporation)
2 ASChannel; C:\Program Files\Hewlett-Packard\IAM\Bin\ASChnl.dll [131584 2006-06-21] (Cognizance Corporation)
2 atchksrv; C:\Program Files\Intel\AMT\atchksrv.exe [182808 2007-11-09] (Intel Corporation)
3 Com4Qlb; "C:\Program Files\Hewlett-Packard\HP Quick Launch Buttons\Com4Qlb.exe" [110592 2007-03-05] (Hewlett-Packard Development Company, L.P.)
2 Eventlog; C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted [21504 2008-01-18] (Microsoft Corporation)
3 FLCDLOCK; C:\Windows\system32\flcdlock.exe [172131 2007-04-30] (Hewlett-Packard Ltd)
2 hpqwmiex; C:\Program Files\Hewlett-Packard\Shared\hpqwmiex.exe [135168 2006-05-02] (Hewlett-Packard Development Company, L.P.)
2 hpsrv; C:\Windows\System32\Hpservice.exe [18944 2007-01-04] ()
2 MDM; "C:\Program Files\Common Files\Microsoft Shared\VS7DEBUG\MDM.EXE" [322120 2003-06-19] (Microsoft Corporation)
4 msvsmon90; "C:\Program Files\Microsoft Visual Studio 9.0\Common7\IDE\Remote Debugger\x86\msvsmon.exe" /service msvsmon90 [3004416 2007-11-06] (Microsoft Corporation)
2 pdfcDispatcher; C:\Program Files\PDF Complete\pdfsvc.exe /startedbyscm:66B66708-40E2BE4D-pdfcService [540448 2007-05-08] (PDF Complete Inc)
3 Samsung UPD Service; "C:\Windows\System32\SUPDSvc.exe" [131888 2010-08-08] (Samsung Electronics CO., LTD.)
2 SkypeUpdate; "C:\Program Files\Skype\Updater\Updater.exe" [158856 2012-02-28] (Skype Technologies)
2 SWIHPWMI; C:\Program Files\HPQ\Shared\Sierra Wireless\Win32\Unicode\SWIHPWMI.exe [292384 2006-12-04] (Sierra Wireless Inc.)
2 UNS; C:\Program Files\Intel\AMT\UNS.exe [1464856 2007-11-09] (Intel Corporation)
2 VMCService; "C:\Program Files\Vodafone\Vodafone Mobile Connect\Bin\VMCService.exe" [9216 2010-01-19] (Vodafone)
2 HP Health Check Service; "c:\Program Files\Hewlett-Packard\HP Health Check\hphc_service.exe" [x]
2 HpFkCryptService; "c:\Program Files\Hewlett-Packard\Drive Encryption\HpFkCrypt.exe" [x]
2 MsMpSvc; "c:\Program Files\Microsoft Security Client\MsMpEng.exe" [x]
2 MSSQL$SQLEXPRESS; "c:\Program Files\Microsoft SQL Server\MSSQL.1\MSSQL\Binn\sqlservr.exe" -sSQLEXPRESS [x]
4 MSSQLServerADHelper; "c:\Program Files\Microsoft SQL Server\90\Shared\sqladhlp90.exe" [x]
3 NisSrv; "c:\Program Files\Microsoft Security Client\NisSrv.exe" [x]
3 RoxMediaDB9; "c:\Program Files\Common Files\Roxio Shared\9.0\SharedCOM\RoxMediaDB9.exe" [x]
2 SQLBrowser; "c:\Program Files\Microsoft SQL Server\90\Shared\sqlbrowser.exe" [x]
2 SQLWriter; "c:\Program Files\Microsoft SQL Server\90\Shared\sqlwriter.exe" [x]
3 stllssvr; "c:\Program Files\Common Files\SureThing Shared\stllssvr.exe" [x]
========================== Drivers (Whitelisted) =============
2 altio; \??\C:\Program Files\Altium Designer S09 Viewer\System\Drivers\altio.sys [3200 2008-06-02] (Altium Limited)
3 ASEDRV3; C:\Windows\System32\drivers\ASEDRV3.sys [51200 2011-04-11] (Athena Smartcard Solutions)
3 AtiHdmiService; C:\Windows\System32\drivers\AtiHdmi.sys [101904 2009-07-23] (ATI Technologies, Inc.)
3 ATSWPDRV; C:\Windows\System32\DRIVERS\ATSwpDrv.sys [140808 2007-04-10] (AuthenTec, Inc.)
3 DAMDrv; C:\Windows\System32\DRIVERS\DAMDrv.sys [30008 2007-04-23] (Hewlett-Packard Development Company L.P.)
1 eabfiltr; C:\Windows\System32\DRIVERS\eabfiltr.sys [8192 2006-11-30] (Hewlett-Packard Development Company, L.P.)
3 ewusbnet; C:\Windows\System32\DRIVERS\ewusbnet.sys [112640 2009-11-04] (Huawei Technologies Co., Ltd.)
3 FPABOOT32; C:\Windows\System32\Drivers\usbFPAB2.sys [10752 2009-11-28] (anchor chips)
3 FTDIBUS; C:\Windows\System32\drivers\ftdibus.sys [57672 2009-02-17] (FTDI Ltd.)
3 FTSER2K; C:\Windows\System32\drivers\ftser2k.sys [72520 2009-02-17] (FTDI Ltd.)
0 giveio; C:\Windows\System32\giveio.sys [5248 1996-04-03] ()
3 HBtnKey; C:\Windows\System32\DRIVERS\cpqbttn.sys [9472 2006-06-28] (Hewlett-Packard Development Company, L.P.)
3 hwusbfake; C:\Windows\System32\DRIVERS\ewusbfake.sys [101120 2009-11-04] (Huawei Technologies Co., Ltd.)
0 MpFilter; C:\Windows\System32\DRIVERS\MpFilter.sys [171064 2012-03-20] (Microsoft Corporation)
1 MpKsl4e444637; \??\c:\ProgramData\Microsoft\Microsoft Antimalware\Definition Updates\{684901F6-8A08-4E5E-80A5-19EA9FB7BB8A}\MpKsl4e444637.sys [29904 2012-08-07] (Microsoft Corporation)
3 PAC7302; C:\Windows\System32\DRIVERS\PAC7302.SYS [457856 2007-06-14] (PixArt Imaging Inc.)
3 rismc32; C:\Windows\System32\DRIVERS\rismc32.sys [47616 2006-12-19] (RICOH Company, Ltd.)
1 RsvLock; C:\Windows\System32\Drivers\RsvLock.sys [5808 2007-04-26] (SafeBoot International)
0 SafeBoot; C:\Windows\System32\Drivers\SafeBoot.sys [100095 2007-04-26] (SafeBoot International)
0 SbAlg; C:\Windows\System32\Drivers\SbAlg.sys [44720 2006-10-09] (SafeBoot N.V.)
0 SbFsLock; C:\Windows\System32\Drivers\SbFsLock.sys [13696 2007-03-29] (SafeBoot International)
2 Sentinel; C:\Windows\System32\Drivers\SENTINEL.SYS [64512 1998-07-21] ()
0 sptd; C:\Windows\System32\Drivers\sptd.sys [691696 2010-09-02] (Duplex Secure Ltd.)
3 Trufos; C:\Windows\System32\DRIVERS\Trufos.sys [309320 2011-07-09] (BitDefender S.R.L.)
3 USBFPA32; C:\Windows\System32\Drivers\usbFPAA2.sys [34304 2006-05-15] (Cypress Semiconductor)
3 ZTEusbnet; C:\Windows\System32\DRIVERS\ZTEusbnet.sys [110080 2008-11-12] (ZTE Corporation)
3 ZTEusbvoice; C:\Windows\System32\DRIVERS\ZTEusbvoice.sys [104960 2008-11-12] (ZTE Incorporated)
4 blbdrive; C:\Windows\system32\drivers\blbdrive.sys [x]
3 IpInIp; C:\Windows\System32\DRIVERS\ipinip.sys [x]
3 NwlnkFlt; C:\Windows\System32\DRIVERS\nwlnkflt.sys [x]
3 NwlnkFwd; C:\Windows\System32\DRIVERS\nwlnkfwd.sys [x]
========================== NetSvcs (Whitelisted) ===========
============ One Month Created Files and Folders ==============
2012-08-07 21:34 - 2012-08-07 21:34 - 00000726 ____A C:\Users\Irina\Desktop\stop.lnk
2012-08-07 12:42 - 2012-08-07 12:43 - 00000000 ____D C:\Program Files\Microsoft Security Client
2012-08-07 12:41 - 2012-08-07 12:41 - 10288512 ____A (Microsoft Corporation) C:\Users\Irina\Desktop\mseinstall(1).exe
2012-08-07 09:52 - 2012-08-07 09:52 - 00000000 ____D C:\Users\Irina\AppData\Roaming\Malwarebytes
2012-08-07 09:52 - 2012-08-07 09:52 - 00000000 ____D C:\Users\All Users\Malwarebytes
2012-08-07 09:51 - 2012-08-07 09:51 - 10652120 ____A (Malwarebytes Corporation ) C:\Users\Irina\Desktop\mbam-setup-1.62.0.1300.exe
2012-08-07 09:07 - 2012-08-07 09:09 - 00000000 ____D C:\Users\All Users\036DFF86004E811B005149102F3B6FDA
2012-08-07 03:16 - 2012-08-07 03:16 - 00035840 ____A C:\Users\Irina\Desktop\a12_3620872_1.xls
2012-07-30 07:04 - 2012-08-07 05:32 - 00000322 ____A C:\Windows\Tasks\HPCeeScheduleForIrina.job
2012-07-23 10:14 - 2012-08-02 06:37 - 00000132 ____A C:\Users\Irina\AppData\Roaming\Adobe BMP Format CS5 Prefs
2012-07-18 00:05 - 2012-07-18 00:05 - 01098385 ____A C:\Users\Irina\Desktop\asesoft_17.07.2012.xlsx
============ 3 Months Modified Files ========================
2012-08-07 22:11 - 2011-05-14 23:36 - 00279552 ____A (Microsoft Corporation) C:\Windows\System32\services.exe
2012-08-07 22:11 - 2010-02-08 01:01 - 00001092 ____A C:\Windows\Tasks\GoogleUpdateTaskMachineCore.job
2012-08-07 22:10 - 2006-11-02 05:01 - 00000006 ___AH C:\Windows\Tasks\SA.DAT
2012-08-07 22:10 - 2006-11-02 04:47 - 00003296 ___AH C:\Windows\System32\7B296FB0-376B-497e-B012-9C450E1B7327-2P-1.C7483456-A289-439d-8115-601632D005A0
2012-08-07 22:10 - 2006-11-02 04:47 - 00003296 ___AH C:\Windows\System32\7B296FB0-376B-497e-B012-9C450E1B7327-2P-0.C7483456-A289-439d-8115-601632D005A0
2012-08-07 21:57 - 2006-11-02 04:52 - 00147586 ____A C:\Windows\setupact.log
2012-08-07 21:34 - 2012-08-07 21:34 - 00000726 ____A C:\Users\Irina\Desktop\stop.lnk
2012-08-07 12:43 - 2011-03-15 03:16 - 00001945 ____A C:\Windows\epplauncher.mif
2012-08-07 12:43 - 2008-02-08 16:20 - 01689360 ____A C:\Windows\WindowsUpdate.log
2012-08-07 12:42 - 2006-11-02 02:33 - 00795960 ____A C:\Windows\System32\PerfStringBackup.INI
2012-08-07 12:41 - 2012-08-07 12:41 - 10288512 ____A (Microsoft Corporation) C:\Users\Irina\Desktop\mseinstall(1).exe
2012-08-07 12:26 - 2006-11-02 05:00 - 00162122 ____A C:\Windows\PFRO.log
2012-08-07 09:51 - 2012-08-07 09:51 - 10652120 ____A (Malwarebytes Corporation ) C:\Users\Irina\Desktop\mbam-setup-1.62.0.1300.exe
2012-08-07 09:45 - 2006-11-09 13:07 - 00002140 ____A C:\Windows\bthservsdp.dat
2012-08-07 09:45 - 2006-11-02 05:01 - 00032644 ____A C:\Windows\Tasks\SCHEDLGU.TXT
2012-08-07 08:54 - 2010-02-08 01:01 - 00001096 ____A C:\Windows\Tasks\GoogleUpdateTaskMachineUA.job
2012-08-07 05:32 - 2012-07-30 07:04 - 00000322 ____A C:\Windows\Tasks\HPCeeScheduleForIrina.job
2012-08-07 03:16 - 2012-08-07 03:16 - 00035840 ____A C:\Users\Irina\Desktop\a12_3620872_1.xls
2012-08-06 07:32 - 2011-05-30 07:09 - 00000052 ____A C:\Windows\System32\DOErrors.log
2012-08-05 07:51 - 2006-11-02 02:23 - 00000407 ____A C:\Windows\win.ini
2012-08-05 03:34 - 2011-12-23 06:59 - 00002687 ____A C:\Users\Public\Desktop\Vodafone Mobile Connect.lnk
2012-08-03 03:50 - 2011-09-08 02:01 - 00001971 ____A C:\Users\Public\Desktop\Google Chrome.lnk
2012-08-02 06:37 - 2012-07-23 10:14 - 00000132 ____A C:\Users\Irina\AppData\Roaming\Adobe BMP Format CS5 Prefs
2012-08-01 22:20 - 2012-05-11 07:33 - 00000049 ____A C:\Windows\wpd99.drv
2012-07-30 06:32 - 2010-09-19 09:14 - 00001356 ____A C:\Users\Irina\AppData\Local\d3d9caps.dat
2012-07-23 08:50 - 2012-03-26 07:43 - 00003121 ____A C:\Windows\System32\responseBody.xml
2012-07-23 08:50 - 2012-03-26 07:43 - 00002092 ____A C:\Windows\System32\requestBody.xml
2012-07-23 08:50 - 2012-03-26 07:43 - 00000847 ____A C:\Windows\System32\request.gzip
2012-07-18 02:43 - 2012-03-27 23:43 - 00002377 ____A C:\Users\Public\Desktop\Skype.lnk
2012-07-18 00:05 - 2012-07-18 00:05 - 01098385 ____A C:\Users\Irina\Desktop\asesoft_17.07.2012.xlsx
2012-07-16 22:00 - 2012-03-06 08:30 - 00000289 ____A C:\Windows\WINCMD.INI
2012-06-27 01:40 - 2012-06-27 01:01 - 286285600 ____A C:\Users\Irina\Desktop\filmulete.zip
2012-06-02 23:47 - 2012-06-02 23:47 - 00000146 ____A C:\Windows\capture.INI
2012-06-02 14:19 - 2012-06-20 20:06 - 01933848 ____A (Microsoft Corporation) C:\Windows\System32\wuaueng.dll
2012-06-02 14:19 - 2012-06-20 20:06 - 00577048 ____A (Microsoft Corporation) C:\Windows\System32\wuapi.dll
2012-06-02 14:19 - 2012-06-20 20:06 - 00053784 ____A (Microsoft Corporation) C:\Windows\System32\wuauclt.exe
2012-06-02 14:19 - 2012-06-20 20:06 - 00045080 ____A (Microsoft Corporation) C:\Windows\System32\wups2.dll
2012-06-02 14:19 - 2012-06-20 20:06 - 00035864 ____A (Microsoft Corporation) C:\Windows\System32\wups.dll
2012-06-02 14:12 - 2012-06-20 20:06 - 02422272 ____A (Microsoft Corporation) C:\Windows\System32\wucltux.dll
2012-06-02 14:12 - 2012-06-20 20:06 - 00088576 ____A (Microsoft Corporation) C:\Windows\System32\wudriver.dll
2012-06-02 04:19 - 2012-06-20 20:06 - 00171904 ____A (Microsoft Corporation) C:\Windows\System32\wuwebv.dll
2012-06-02 04:12 - 2012-06-20 20:06 - 00033792 ____A (Microsoft Corporation) C:\Windows\System32\wuapp.exe
2012-06-01 23:37 - 2008-02-18 06:03 - 00011264 ____A C:\Users\Irina\AppData\Local\DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.ini
2012-05-31 11:52 - 2010-12-21 07:54 - 00000000 ____A C:\Users\Irina\AppData\Local\FnF4.txt
2012-05-24 10:09 - 2012-05-24 10:09 - 00028160 ____A C:\Users\Irina\Documents\buget proiect assist1.xls
2012-05-11 07:32 - 2012-05-11 07:32 - 00000028 ____A C:\Windows\pdf995.ini
ZeroAccess:
C:\Windows\Installer\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}
C:\Windows\Installer\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}\@
C:\Windows\Installer\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}\L
C:\Windows\Installer\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}\n
C:\Windows\Installer\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}\U
C:\Windows\Installer\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}\U\00000001.@
ZeroAccess:
C:\Users\Irina\AppData\Local\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}
C:\Users\Irina\AppData\Local\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}\@
C:\Users\Irina\AppData\Local\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}\L
C:\Users\Irina\AppData\Local\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}\n
C:\Users\Irina\AppData\Local\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}\U
========================= Known DLLs (Whitelisted) ============
========================= Bamital & volsnap Check ============
C:\Windows\explorer.exe => MD5 is legit
C:\Windows\System32\winlogon.exe => MD5 is legit
C:\Windows\System32\wininit.exe => MD5 is legit
C:\Windows\System32\svchost.exe => MD5 is legit
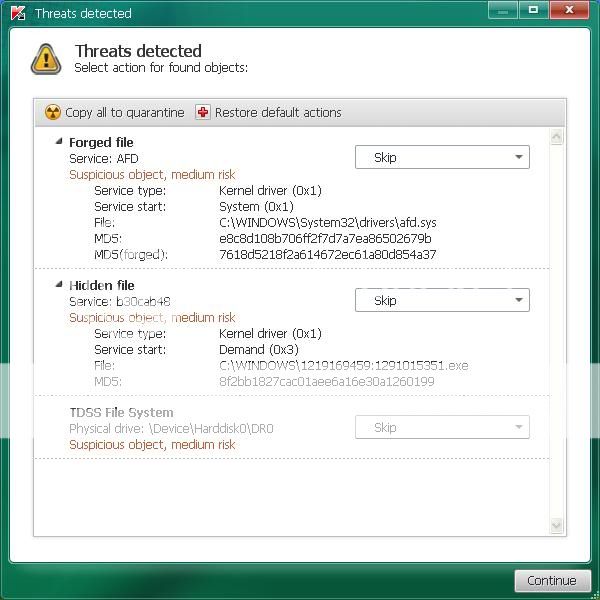
C:\Windows\System32\services.exe 8737764F4FD36D6808EE80578409C843 ZeroAccess <==== ATTENTION!.
C:\Windows\System32\User32.dll => MD5 is legit
C:\Windows\System32\userinit.exe => MD5 is legit
C:\Windows\System32\Drivers\volsnap.sys => MD5 is legit
==================== EXE ASSOCIATION =====================
HKLM\...\.exe: exefile => OK
HKLM\...\exefile\DefaultIcon: %1 => OK
HKLM\...\exefile\open\command: "%1" %* => OK
========================= Memory info ======================
Percentage of memory in use: 27%
Total physical RAM: 2014.69 MB
Available physical RAM: 1467.41 MB
Total Pagefile: 1748.77 MB
Available Pagefile: 1579.07 MB
Total Virtual: 2047.88 MB
Available Virtual: 1990.33 MB
======================= Partitions =========================
1 Drive c: () (Fixed) (Total:102.39 GB) (Free:25.32 GB) NTFS ==>[Drive with boot components (obtained from BCD)]
2 Drive d: (HP_RECOVERY) (Fixed) (Total:7.84 GB) (Free:0.72 GB) NTFS ==>[System with boot components (obtained from reading drive)]
3 Drive e: (D) (Fixed) (Total:1.55 GB) (Free:1.21 GB) NTFS
5 Drive g: () (Removable) (Total:1.86 GB) (Free:0.36 GB) FAT
6 Drive x: (Boot) (Fixed) (Total:0.03 GB) (Free:0.03 GB) NTFS
Disk ### Status Size Free Dyn Gpt
-------- ---------- ------- ------- --- ---
Disk 0 Online 112 GB 4568 KB
Disk 1 Online 1908 MB 0 B
Partitions of Disk 0:
===============
Partition ### Type Size Offset
------------- ---------------- ------- -------
Partition 1 Primary 102 GB 32 KB
Partition 2 Primary 8028 MB 102 GB
Partition 3 Primary 1589 MB 110 GB
==================================================================================
Disk: 0
Partition 1
Type : 07
Hidden: No
Active: Yes
Volume ### Ltr Label Fs Type Size Status Info
---------- --- ----------- ----- ---------- ------- --------- --------
* Volume 0 C NTFS Partition 102 GB Healthy
==================================================================================
Disk: 0
Partition 2
Type : 07
Hidden: No
Active: No
Volume ### Ltr Label Fs Type Size Status Info
---------- --- ----------- ----- ---------- ------- --------- --------
* Volume 1 D HP_RECOVERY NTFS Partition 8028 MB Healthy
==================================================================================
Disk: 0
Partition 3
Type : 07
Hidden: No
Active: No
Volume ### Ltr Label Fs Type Size Status Info
---------- --- ----------- ----- ---------- ------- --------- --------
* Volume 2 E D NTFS Partition 1589 MB Healthy
==================================================================================
Partitions of Disk 1:
===============
Partition ### Type Size Offset
------------- ---------------- ------- -------
* Partition 1 Primary 1908 MB 0 B
==================================================================================
Disk: 1
There is no partition selected.
There is no partition selected.
Please select a partition and try again.
==================================================================================
==========================================================
Last Boot: 2012-08-07 12:33
======================= End Of Log ==========================
SEARCH.TXT
Farbar Recovery Scan Tool Version: 08-08-2012
Ran by SYSTEM at 2012-08-08 09:26:44
Running from G:\
================== Search: "services.exe" ===================
C:\Windows\winsxs\x86_microsoft-windows-s..s-servicecontroller_31bf3856ad364e35_6.0.6002.18005_none_d14b3973ca6acc56\services.exe
[2011-05-14 23:36] - [2009-04-10 22:27] - 0279552 ____A (Microsoft Corporation) D4E6D91C1349B7BFB3599A6ADA56851B
C:\Windows\winsxs\x86_microsoft-windows-s..s-servicecontroller_31bf3856ad364e35_6.0.6001.18000_none_cf5fc067cd49010a\services.exe
[2009-03-04 10:36] - [2008-01-18 23:33] - 0279040 ____A (Microsoft Corporation) 2B336AB6286D6C81FA02CBAB914E3C6C
C:\Windows\winsxs\x86_microsoft-windows-s..s-servicecontroller_31bf3856ad364e35_6.0.6000.16386_none_cd28fe6bd05df036\services.exe
[2006-11-02 00:35] - [2006-11-02 01:45] - 0279552 ____A (Microsoft Corporation) 329CF3C97CE4C19375C8ABCABAE258B0
C:\Windows\System32\services.exe
[2011-05-14 23:36] - [2012-08-07 22:11] - 0279552 ____A (Microsoft Corporation) 8737764F4FD36D6808EE80578409C843
=== End Of Search ===
Like many others here I too have the caught the Sirefef virus (at least that's what MSE says it is before the computer abruptly restarts).
I have Windows Vista Professional 32.
I ran farbar, I'm pasting the logs below.
Thank you for your help, it's greatly appreciated.
--------------------------------------------------------------------------------
FRST.TXT
Scan result of Farbar Recovery Scan Tool (FRST written by Farbar) Version: 08-08-2012
Ran by SYSTEM at 08-08-2012 09:24:24
Running from G:\
Windows Vista (TM) Business (X86) OS Language: English(US)
The current controlset is ControlSet001
========================== Registry (Whitelisted) =============
HKLM\...\Run: [PTHOSTTR] C:\Program Files\Hewlett-Packard\HP ProtectTools Security Manager\PTHOSTTR.EXE /Start [145184 2007-01-09] (Hewlett-Packard Development Company, L.P.)
HKLM\...\Run: [SynTPEnh] C:\Program Files\Synaptics\SynTP\SynTPEnh.exe [827392 2007-01-12] (Synaptics, Inc.)
HKLM\...\Run: [SunJavaUpdateSched] "C:\Program Files\Common Files\Java\Java Update\jusched.exe" [254696 2012-01-18] (Sun Microsystems, Inc.)
HKLM\...\Run: [QlbCtrl] %ProgramFiles%\Hewlett-Packard\HP Quick Launch Buttons\QlbCtrl.exe /Start [163840 2007-05-02] ( Hewlett-Packard Development Company, L.P.)
HKLM\...\Run: [HP Software Update] c:\Program Files\Hp\HP Software Update\HPWuSchd2.exe [49152 2005-02-16] (Hewlett-Packard Co.)
HKLM\...\Run: [HP Health Check Scheduler] c:\Program Files\Hewlett-Packard\HP Health Check\HPHC_Scheduler.exe [75008 2008-10-08] (Hewlett-Packard)
HKLM\...\Run: [atchk] "C:\Program Files\Intel\AMT\atchk.exe" [408088 2007-11-09] (Intel Corporation)
HKLM\...\Run: [NeroFilterCheck] C:\Windows\system32\NeroCheck.exe [155648 2001-07-09] (Ahead Software Gmbh)
HKLM\...\Run: [PAC7302_Monitor] C:\Windows\PixArt\PAC7302\Monitor.exe [319488 2006-11-03] (PixArt Imaging Incorporation)
HKLM\...\Run: [hpWirelessAssistant] C:\Program Files\Hewlett-Packard\HP Wireless Assistant\HPWAMain.exe [480560 2007-10-03] (Hewlett-Packard Development Company, L.P.)
HKLM\...\Run: [StartCCC] "C:\Program Files\ATI Technologies\ATI.ACE\Core-Static\CLIStart.exe" MSRun [98304 2009-08-13] (Advanced Micro Devices, Inc.)
HKLM\...\Run: [IDProtect Monitor] "C:\Program Files\Athena\IDProtect Client\Utils\IDProtect Monitor.exe" [323664 2010-12-01] (Athena Smartcard Solutions)
HKLM\...\Run: [SoundMAXPnP] C:\Program Files\Analog Devices\Core\smax4pnp.exe [1183744 2007-02-21] (Analog Devices, Inc.)
HKLM\...\Run: [Adobe ARM] "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" [843712 2012-01-02] (Adobe Systems Incorporated)
HKLM\...\Run: [AdobeAAMUpdater-1.0] "C:\Program Files\Common Files\Adobe\OOBE\PDApp\UWA\UpdaterStartupUtility.exe" [500208 2010-03-05] (Adobe Systems Incorporated)
HKLM\...\Run: [AdobeCS5ServiceManager] "C:\Program Files\Common Files\Adobe\CS5ServiceManager\CS5ServiceManager.exe" -launchedbylogin [406992 2010-02-21] (Adobe Systems Incorporated)
HKLM\...\Run: [SwitchBoard] C:\Program Files\Common Files\Adobe\SwitchBoard\SwitchBoard.exe [517096 2010-02-19] (Adobe Systems Incorporated)
HKLM\...\Run: [MSC] "c:\Program Files\Microsoft Security Client\msseces.exe" -hide -runkey [931200 2012-03-26] (Microsoft Corporation)
HKU\Irina\...\Run: [Messenger (Yahoo!)] "C:\PROGRA~1\Yahoo!\MESSEN~1\YahooMessenger.exe" -quiet [6497592 2012-01-03] (Yahoo! Inc.)
HKU\Irina\...\Run: [YSearchProtection] C:\Program Files\Yahoo!\Search Protection\YspService.exe [296248 2010-06-13] (Yahoo! Inc.)
HKU\Irina\...\Run: [swg] "C:\Program Files\Google\GoogleToolbarNotifier\GoogleToolbarNotifier.exe" [39408 2009-04-23] (Google Inc.)
Winlogon\Notify\DeviceNP: DeviceNP.dll (Hewlett-Packard Limited)
Winlogon\Notify\ScCertProp: wlnotify.dll [X]
Tcpip\Parameters: [DhcpNameServer] 192.168.1.1
AppInit_DLLs: APSHook.dll
Lsa: [Notification Packages] SbHpNp
scecli
ASWLNPkg
================================ Services (Whitelisted) ==================
2 ASBroker; C:\Program Files\Hewlett-Packard\IAM\Bin\ASWLNPkg.dll [74240 2007-02-06] (Cognizance Corporation)
2 ASChannel; C:\Program Files\Hewlett-Packard\IAM\Bin\ASChnl.dll [131584 2006-06-21] (Cognizance Corporation)
2 atchksrv; C:\Program Files\Intel\AMT\atchksrv.exe [182808 2007-11-09] (Intel Corporation)
3 Com4Qlb; "C:\Program Files\Hewlett-Packard\HP Quick Launch Buttons\Com4Qlb.exe" [110592 2007-03-05] (Hewlett-Packard Development Company, L.P.)
2 Eventlog; C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted [21504 2008-01-18] (Microsoft Corporation)
3 FLCDLOCK; C:\Windows\system32\flcdlock.exe [172131 2007-04-30] (Hewlett-Packard Ltd)
2 hpqwmiex; C:\Program Files\Hewlett-Packard\Shared\hpqwmiex.exe [135168 2006-05-02] (Hewlett-Packard Development Company, L.P.)
2 hpsrv; C:\Windows\System32\Hpservice.exe [18944 2007-01-04] ()
2 MDM; "C:\Program Files\Common Files\Microsoft Shared\VS7DEBUG\MDM.EXE" [322120 2003-06-19] (Microsoft Corporation)
4 msvsmon90; "C:\Program Files\Microsoft Visual Studio 9.0\Common7\IDE\Remote Debugger\x86\msvsmon.exe" /service msvsmon90 [3004416 2007-11-06] (Microsoft Corporation)
2 pdfcDispatcher; C:\Program Files\PDF Complete\pdfsvc.exe /startedbyscm:66B66708-40E2BE4D-pdfcService [540448 2007-05-08] (PDF Complete Inc)
3 Samsung UPD Service; "C:\Windows\System32\SUPDSvc.exe" [131888 2010-08-08] (Samsung Electronics CO., LTD.)
2 SkypeUpdate; "C:\Program Files\Skype\Updater\Updater.exe" [158856 2012-02-28] (Skype Technologies)
2 SWIHPWMI; C:\Program Files\HPQ\Shared\Sierra Wireless\Win32\Unicode\SWIHPWMI.exe [292384 2006-12-04] (Sierra Wireless Inc.)
2 UNS; C:\Program Files\Intel\AMT\UNS.exe [1464856 2007-11-09] (Intel Corporation)
2 VMCService; "C:\Program Files\Vodafone\Vodafone Mobile Connect\Bin\VMCService.exe" [9216 2010-01-19] (Vodafone)
2 HP Health Check Service; "c:\Program Files\Hewlett-Packard\HP Health Check\hphc_service.exe" [x]
2 HpFkCryptService; "c:\Program Files\Hewlett-Packard\Drive Encryption\HpFkCrypt.exe" [x]
2 MsMpSvc; "c:\Program Files\Microsoft Security Client\MsMpEng.exe" [x]
2 MSSQL$SQLEXPRESS; "c:\Program Files\Microsoft SQL Server\MSSQL.1\MSSQL\Binn\sqlservr.exe" -sSQLEXPRESS [x]
4 MSSQLServerADHelper; "c:\Program Files\Microsoft SQL Server\90\Shared\sqladhlp90.exe" [x]
3 NisSrv; "c:\Program Files\Microsoft Security Client\NisSrv.exe" [x]
3 RoxMediaDB9; "c:\Program Files\Common Files\Roxio Shared\9.0\SharedCOM\RoxMediaDB9.exe" [x]
2 SQLBrowser; "c:\Program Files\Microsoft SQL Server\90\Shared\sqlbrowser.exe" [x]
2 SQLWriter; "c:\Program Files\Microsoft SQL Server\90\Shared\sqlwriter.exe" [x]
3 stllssvr; "c:\Program Files\Common Files\SureThing Shared\stllssvr.exe" [x]
========================== Drivers (Whitelisted) =============
2 altio; \??\C:\Program Files\Altium Designer S09 Viewer\System\Drivers\altio.sys [3200 2008-06-02] (Altium Limited)
3 ASEDRV3; C:\Windows\System32\drivers\ASEDRV3.sys [51200 2011-04-11] (Athena Smartcard Solutions)
3 AtiHdmiService; C:\Windows\System32\drivers\AtiHdmi.sys [101904 2009-07-23] (ATI Technologies, Inc.)
3 ATSWPDRV; C:\Windows\System32\DRIVERS\ATSwpDrv.sys [140808 2007-04-10] (AuthenTec, Inc.)
3 DAMDrv; C:\Windows\System32\DRIVERS\DAMDrv.sys [30008 2007-04-23] (Hewlett-Packard Development Company L.P.)
1 eabfiltr; C:\Windows\System32\DRIVERS\eabfiltr.sys [8192 2006-11-30] (Hewlett-Packard Development Company, L.P.)
3 ewusbnet; C:\Windows\System32\DRIVERS\ewusbnet.sys [112640 2009-11-04] (Huawei Technologies Co., Ltd.)
3 FPABOOT32; C:\Windows\System32\Drivers\usbFPAB2.sys [10752 2009-11-28] (anchor chips)
3 FTDIBUS; C:\Windows\System32\drivers\ftdibus.sys [57672 2009-02-17] (FTDI Ltd.)
3 FTSER2K; C:\Windows\System32\drivers\ftser2k.sys [72520 2009-02-17] (FTDI Ltd.)
0 giveio; C:\Windows\System32\giveio.sys [5248 1996-04-03] ()
3 HBtnKey; C:\Windows\System32\DRIVERS\cpqbttn.sys [9472 2006-06-28] (Hewlett-Packard Development Company, L.P.)
3 hwusbfake; C:\Windows\System32\DRIVERS\ewusbfake.sys [101120 2009-11-04] (Huawei Technologies Co., Ltd.)
0 MpFilter; C:\Windows\System32\DRIVERS\MpFilter.sys [171064 2012-03-20] (Microsoft Corporation)
1 MpKsl4e444637; \??\c:\ProgramData\Microsoft\Microsoft Antimalware\Definition Updates\{684901F6-8A08-4E5E-80A5-19EA9FB7BB8A}\MpKsl4e444637.sys [29904 2012-08-07] (Microsoft Corporation)
3 PAC7302; C:\Windows\System32\DRIVERS\PAC7302.SYS [457856 2007-06-14] (PixArt Imaging Inc.)
3 rismc32; C:\Windows\System32\DRIVERS\rismc32.sys [47616 2006-12-19] (RICOH Company, Ltd.)
1 RsvLock; C:\Windows\System32\Drivers\RsvLock.sys [5808 2007-04-26] (SafeBoot International)
0 SafeBoot; C:\Windows\System32\Drivers\SafeBoot.sys [100095 2007-04-26] (SafeBoot International)
0 SbAlg; C:\Windows\System32\Drivers\SbAlg.sys [44720 2006-10-09] (SafeBoot N.V.)
0 SbFsLock; C:\Windows\System32\Drivers\SbFsLock.sys [13696 2007-03-29] (SafeBoot International)
2 Sentinel; C:\Windows\System32\Drivers\SENTINEL.SYS [64512 1998-07-21] ()
0 sptd; C:\Windows\System32\Drivers\sptd.sys [691696 2010-09-02] (Duplex Secure Ltd.)
3 Trufos; C:\Windows\System32\DRIVERS\Trufos.sys [309320 2011-07-09] (BitDefender S.R.L.)
3 USBFPA32; C:\Windows\System32\Drivers\usbFPAA2.sys [34304 2006-05-15] (Cypress Semiconductor)
3 ZTEusbnet; C:\Windows\System32\DRIVERS\ZTEusbnet.sys [110080 2008-11-12] (ZTE Corporation)
3 ZTEusbvoice; C:\Windows\System32\DRIVERS\ZTEusbvoice.sys [104960 2008-11-12] (ZTE Incorporated)
4 blbdrive; C:\Windows\system32\drivers\blbdrive.sys [x]
3 IpInIp; C:\Windows\System32\DRIVERS\ipinip.sys [x]
3 NwlnkFlt; C:\Windows\System32\DRIVERS\nwlnkflt.sys [x]
3 NwlnkFwd; C:\Windows\System32\DRIVERS\nwlnkfwd.sys [x]
========================== NetSvcs (Whitelisted) ===========
============ One Month Created Files and Folders ==============
2012-08-07 21:34 - 2012-08-07 21:34 - 00000726 ____A C:\Users\Irina\Desktop\stop.lnk
2012-08-07 12:42 - 2012-08-07 12:43 - 00000000 ____D C:\Program Files\Microsoft Security Client
2012-08-07 12:41 - 2012-08-07 12:41 - 10288512 ____A (Microsoft Corporation) C:\Users\Irina\Desktop\mseinstall(1).exe
2012-08-07 09:52 - 2012-08-07 09:52 - 00000000 ____D C:\Users\Irina\AppData\Roaming\Malwarebytes
2012-08-07 09:52 - 2012-08-07 09:52 - 00000000 ____D C:\Users\All Users\Malwarebytes
2012-08-07 09:51 - 2012-08-07 09:51 - 10652120 ____A (Malwarebytes Corporation ) C:\Users\Irina\Desktop\mbam-setup-1.62.0.1300.exe
2012-08-07 09:07 - 2012-08-07 09:09 - 00000000 ____D C:\Users\All Users\036DFF86004E811B005149102F3B6FDA
2012-08-07 03:16 - 2012-08-07 03:16 - 00035840 ____A C:\Users\Irina\Desktop\a12_3620872_1.xls
2012-07-30 07:04 - 2012-08-07 05:32 - 00000322 ____A C:\Windows\Tasks\HPCeeScheduleForIrina.job
2012-07-23 10:14 - 2012-08-02 06:37 - 00000132 ____A C:\Users\Irina\AppData\Roaming\Adobe BMP Format CS5 Prefs
2012-07-18 00:05 - 2012-07-18 00:05 - 01098385 ____A C:\Users\Irina\Desktop\asesoft_17.07.2012.xlsx
============ 3 Months Modified Files ========================
2012-08-07 22:11 - 2011-05-14 23:36 - 00279552 ____A (Microsoft Corporation) C:\Windows\System32\services.exe
2012-08-07 22:11 - 2010-02-08 01:01 - 00001092 ____A C:\Windows\Tasks\GoogleUpdateTaskMachineCore.job
2012-08-07 22:10 - 2006-11-02 05:01 - 00000006 ___AH C:\Windows\Tasks\SA.DAT
2012-08-07 22:10 - 2006-11-02 04:47 - 00003296 ___AH C:\Windows\System32\7B296FB0-376B-497e-B012-9C450E1B7327-2P-1.C7483456-A289-439d-8115-601632D005A0
2012-08-07 22:10 - 2006-11-02 04:47 - 00003296 ___AH C:\Windows\System32\7B296FB0-376B-497e-B012-9C450E1B7327-2P-0.C7483456-A289-439d-8115-601632D005A0
2012-08-07 21:57 - 2006-11-02 04:52 - 00147586 ____A C:\Windows\setupact.log
2012-08-07 21:34 - 2012-08-07 21:34 - 00000726 ____A C:\Users\Irina\Desktop\stop.lnk
2012-08-07 12:43 - 2011-03-15 03:16 - 00001945 ____A C:\Windows\epplauncher.mif
2012-08-07 12:43 - 2008-02-08 16:20 - 01689360 ____A C:\Windows\WindowsUpdate.log
2012-08-07 12:42 - 2006-11-02 02:33 - 00795960 ____A C:\Windows\System32\PerfStringBackup.INI
2012-08-07 12:41 - 2012-08-07 12:41 - 10288512 ____A (Microsoft Corporation) C:\Users\Irina\Desktop\mseinstall(1).exe
2012-08-07 12:26 - 2006-11-02 05:00 - 00162122 ____A C:\Windows\PFRO.log
2012-08-07 09:51 - 2012-08-07 09:51 - 10652120 ____A (Malwarebytes Corporation ) C:\Users\Irina\Desktop\mbam-setup-1.62.0.1300.exe
2012-08-07 09:45 - 2006-11-09 13:07 - 00002140 ____A C:\Windows\bthservsdp.dat
2012-08-07 09:45 - 2006-11-02 05:01 - 00032644 ____A C:\Windows\Tasks\SCHEDLGU.TXT
2012-08-07 08:54 - 2010-02-08 01:01 - 00001096 ____A C:\Windows\Tasks\GoogleUpdateTaskMachineUA.job
2012-08-07 05:32 - 2012-07-30 07:04 - 00000322 ____A C:\Windows\Tasks\HPCeeScheduleForIrina.job
2012-08-07 03:16 - 2012-08-07 03:16 - 00035840 ____A C:\Users\Irina\Desktop\a12_3620872_1.xls
2012-08-06 07:32 - 2011-05-30 07:09 - 00000052 ____A C:\Windows\System32\DOErrors.log
2012-08-05 07:51 - 2006-11-02 02:23 - 00000407 ____A C:\Windows\win.ini
2012-08-05 03:34 - 2011-12-23 06:59 - 00002687 ____A C:\Users\Public\Desktop\Vodafone Mobile Connect.lnk
2012-08-03 03:50 - 2011-09-08 02:01 - 00001971 ____A C:\Users\Public\Desktop\Google Chrome.lnk
2012-08-02 06:37 - 2012-07-23 10:14 - 00000132 ____A C:\Users\Irina\AppData\Roaming\Adobe BMP Format CS5 Prefs
2012-08-01 22:20 - 2012-05-11 07:33 - 00000049 ____A C:\Windows\wpd99.drv
2012-07-30 06:32 - 2010-09-19 09:14 - 00001356 ____A C:\Users\Irina\AppData\Local\d3d9caps.dat
2012-07-23 08:50 - 2012-03-26 07:43 - 00003121 ____A C:\Windows\System32\responseBody.xml
2012-07-23 08:50 - 2012-03-26 07:43 - 00002092 ____A C:\Windows\System32\requestBody.xml
2012-07-23 08:50 - 2012-03-26 07:43 - 00000847 ____A C:\Windows\System32\request.gzip
2012-07-18 02:43 - 2012-03-27 23:43 - 00002377 ____A C:\Users\Public\Desktop\Skype.lnk
2012-07-18 00:05 - 2012-07-18 00:05 - 01098385 ____A C:\Users\Irina\Desktop\asesoft_17.07.2012.xlsx
2012-07-16 22:00 - 2012-03-06 08:30 - 00000289 ____A C:\Windows\WINCMD.INI
2012-06-27 01:40 - 2012-06-27 01:01 - 286285600 ____A C:\Users\Irina\Desktop\filmulete.zip
2012-06-02 23:47 - 2012-06-02 23:47 - 00000146 ____A C:\Windows\capture.INI
2012-06-02 14:19 - 2012-06-20 20:06 - 01933848 ____A (Microsoft Corporation) C:\Windows\System32\wuaueng.dll
2012-06-02 14:19 - 2012-06-20 20:06 - 00577048 ____A (Microsoft Corporation) C:\Windows\System32\wuapi.dll
2012-06-02 14:19 - 2012-06-20 20:06 - 00053784 ____A (Microsoft Corporation) C:\Windows\System32\wuauclt.exe
2012-06-02 14:19 - 2012-06-20 20:06 - 00045080 ____A (Microsoft Corporation) C:\Windows\System32\wups2.dll
2012-06-02 14:19 - 2012-06-20 20:06 - 00035864 ____A (Microsoft Corporation) C:\Windows\System32\wups.dll
2012-06-02 14:12 - 2012-06-20 20:06 - 02422272 ____A (Microsoft Corporation) C:\Windows\System32\wucltux.dll
2012-06-02 14:12 - 2012-06-20 20:06 - 00088576 ____A (Microsoft Corporation) C:\Windows\System32\wudriver.dll
2012-06-02 04:19 - 2012-06-20 20:06 - 00171904 ____A (Microsoft Corporation) C:\Windows\System32\wuwebv.dll
2012-06-02 04:12 - 2012-06-20 20:06 - 00033792 ____A (Microsoft Corporation) C:\Windows\System32\wuapp.exe
2012-06-01 23:37 - 2008-02-18 06:03 - 00011264 ____A C:\Users\Irina\AppData\Local\DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.ini
2012-05-31 11:52 - 2010-12-21 07:54 - 00000000 ____A C:\Users\Irina\AppData\Local\FnF4.txt
2012-05-24 10:09 - 2012-05-24 10:09 - 00028160 ____A C:\Users\Irina\Documents\buget proiect assist1.xls
2012-05-11 07:32 - 2012-05-11 07:32 - 00000028 ____A C:\Windows\pdf995.ini
ZeroAccess:
C:\Windows\Installer\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}
C:\Windows\Installer\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}\@
C:\Windows\Installer\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}\L
C:\Windows\Installer\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}\n
C:\Windows\Installer\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}\U
C:\Windows\Installer\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}\U\00000001.@
ZeroAccess:
C:\Users\Irina\AppData\Local\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}
C:\Users\Irina\AppData\Local\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}\@
C:\Users\Irina\AppData\Local\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}\L
C:\Users\Irina\AppData\Local\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}\n
C:\Users\Irina\AppData\Local\{ff24043d-55f8-5ce9-a20a-8337d9b4b888}\U
========================= Known DLLs (Whitelisted) ============
========================= Bamital & volsnap Check ============
C:\Windows\explorer.exe => MD5 is legit
C:\Windows\System32\winlogon.exe => MD5 is legit
C:\Windows\System32\wininit.exe => MD5 is legit
C:\Windows\System32\svchost.exe => MD5 is legit
C:\Windows\System32\services.exe 8737764F4FD36D6808EE80578409C843 ZeroAccess <==== ATTENTION!.
C:\Windows\System32\User32.dll => MD5 is legit
C:\Windows\System32\userinit.exe => MD5 is legit
C:\Windows\System32\Drivers\volsnap.sys => MD5 is legit
==================== EXE ASSOCIATION =====================
HKLM\...\.exe: exefile => OK
HKLM\...\exefile\DefaultIcon: %1 => OK
HKLM\...\exefile\open\command: "%1" %* => OK
========================= Memory info ======================
Percentage of memory in use: 27%
Total physical RAM: 2014.69 MB
Available physical RAM: 1467.41 MB
Total Pagefile: 1748.77 MB
Available Pagefile: 1579.07 MB
Total Virtual: 2047.88 MB
Available Virtual: 1990.33 MB
======================= Partitions =========================
1 Drive c: () (Fixed) (Total:102.39 GB) (Free:25.32 GB) NTFS ==>[Drive with boot components (obtained from BCD)]
2 Drive d: (HP_RECOVERY) (Fixed) (Total:7.84 GB) (Free:0.72 GB) NTFS ==>[System with boot components (obtained from reading drive)]
3 Drive e: (D) (Fixed) (Total:1.55 GB) (Free:1.21 GB) NTFS
5 Drive g: () (Removable) (Total:1.86 GB) (Free:0.36 GB) FAT
6 Drive x: (Boot) (Fixed) (Total:0.03 GB) (Free:0.03 GB) NTFS
Disk ### Status Size Free Dyn Gpt
-------- ---------- ------- ------- --- ---
Disk 0 Online 112 GB 4568 KB
Disk 1 Online 1908 MB 0 B
Partitions of Disk 0:
===============
Partition ### Type Size Offset
------------- ---------------- ------- -------
Partition 1 Primary 102 GB 32 KB
Partition 2 Primary 8028 MB 102 GB
Partition 3 Primary 1589 MB 110 GB
==================================================================================
Disk: 0
Partition 1
Type : 07
Hidden: No
Active: Yes
Volume ### Ltr Label Fs Type Size Status Info
---------- --- ----------- ----- ---------- ------- --------- --------
* Volume 0 C NTFS Partition 102 GB Healthy
==================================================================================
Disk: 0
Partition 2
Type : 07
Hidden: No
Active: No
Volume ### Ltr Label Fs Type Size Status Info
---------- --- ----------- ----- ---------- ------- --------- --------
* Volume 1 D HP_RECOVERY NTFS Partition 8028 MB Healthy
==================================================================================
Disk: 0
Partition 3
Type : 07
Hidden: No
Active: No
Volume ### Ltr Label Fs Type Size Status Info
---------- --- ----------- ----- ---------- ------- --------- --------
* Volume 2 E D NTFS Partition 1589 MB Healthy
==================================================================================
Partitions of Disk 1:
===============
Partition ### Type Size Offset
------------- ---------------- ------- -------
* Partition 1 Primary 1908 MB 0 B
==================================================================================
Disk: 1
There is no partition selected.
There is no partition selected.
Please select a partition and try again.
==================================================================================
==========================================================
Last Boot: 2012-08-07 12:33
======================= End Of Log ==========================
SEARCH.TXT
Farbar Recovery Scan Tool Version: 08-08-2012
Ran by SYSTEM at 2012-08-08 09:26:44
Running from G:\
================== Search: "services.exe" ===================
C:\Windows\winsxs\x86_microsoft-windows-s..s-servicecontroller_31bf3856ad364e35_6.0.6002.18005_none_d14b3973ca6acc56\services.exe
[2011-05-14 23:36] - [2009-04-10 22:27] - 0279552 ____A (Microsoft Corporation) D4E6D91C1349B7BFB3599A6ADA56851B
C:\Windows\winsxs\x86_microsoft-windows-s..s-servicecontroller_31bf3856ad364e35_6.0.6001.18000_none_cf5fc067cd49010a\services.exe
[2009-03-04 10:36] - [2008-01-18 23:33] - 0279040 ____A (Microsoft Corporation) 2B336AB6286D6C81FA02CBAB914E3C6C
C:\Windows\winsxs\x86_microsoft-windows-s..s-servicecontroller_31bf3856ad364e35_6.0.6000.16386_none_cd28fe6bd05df036\services.exe
[2006-11-02 00:35] - [2006-11-02 01:45] - 0279552 ____A (Microsoft Corporation) 329CF3C97CE4C19375C8ABCABAE258B0
C:\Windows\System32\services.exe
[2011-05-14 23:36] - [2012-08-07 22:11] - 0279552 ____A (Microsoft Corporation) 8737764F4FD36D6808EE80578409C843
=== End Of Search ===