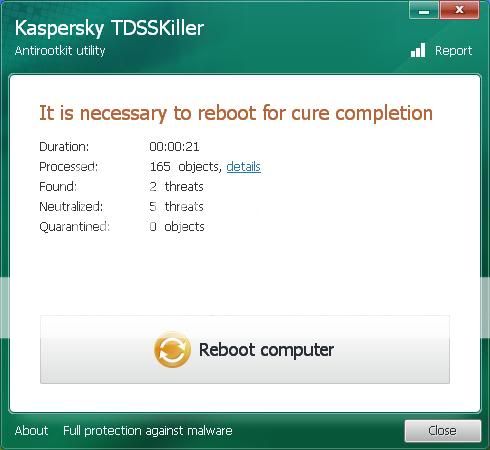
Hi,
Thank you in advance for any help given! The problem is that I have a virus which shows up as svchost.exe*32 in my task manager, when I see its properties, it originates from my appdata/temp folder. This definitely cant be right. I also had the same thing but with a 'win32*32' on my C:/. Malwarebytes got rid of that one and hasnt come back. Malwarebytes also detects the svchost.exe and deletes on reboot. But when I reboot, it's still there. Even when I browse to the file, find the offending svchost file, delete it. once rebooted it returns...
ComboFix 12-12-07.01 - Jonathan 10/12/2012 10:58:22.2.4 - x64
Microsoft Windows 7 Ultimate 6.1.7601.1.1252.44.1033.18.32715.30302 [GMT 0:00]
Running from: c:\users\Jonathan\Downloads\ComboFix.exe
AV: Kaspersky Anti-Virus *Disabled/Outdated* {2EAA32A5-1EE1-1B22-95DA-337730C6E984}
FW: Kaspersky Anti-Virus *Disabled* {1691B380-548E-1A7A-BE85-9A42CE15AEFF}
SP: Kaspersky Anti-Virus *Disabled/Updated* {95CBD341-38DB-14AC-AF6A-08054B41A339}
SP: Windows Defender *Enabled/Updated* {D68DDC3A-831F-4fae-9E44-DA132C1ACF46}
.
.
((((((((((((((((((((((((( Files Created from 2012-11-10 to 2012-12-10 )))))))))))))))))))))))))))))))
.
.
2012-12-10 11:03 . 2012-12-10 11:03--------d-----w-c:\users\UpdatusUser\AppData\Local\temp
2012-12-10 11:03 . 2012-12-10 11:03--------d-----w-c:\users\Default\AppData\Local\temp
2012-12-10 02:07 . 2012-12-10 02:07--------d-----w-c:\users\Jonathan\AppData\Roaming\Malwarebytes
2012-12-10 02:07 . 2012-12-10 02:07--------d-----w-c:\programdata\Malwarebytes
2012-12-10 02:07 . 2012-12-10 02:07--------d-----w-c:\program files (x86)\Malwarebytes' Anti-Malware
2012-12-10 02:07 . 2012-09-29 19:5425928----a-w-c:\windows\system32\drivers\mbam.sys
2012-12-10 00:04 . 2012-12-10 02:01--------d-----w-c:\program files (x86)\stinger
2012-12-09 22:30 . 2012-12-10 10:57--------d-----w-c:\programdata\Kaspersky Lab
2012-12-09 22:30 . 2012-12-09 22:30--------d-----w-c:\program files (x86)\Kaspersky Lab
2012-12-09 22:30 . 2012-12-09 22:30556120----a-w-c:\windows\system32\drivers\klif.sys
2012-12-09 22:25 . 2012-11-08 17:249125352----a-w-c:\programdata\Microsoft\Windows Defender\Definition Updates\{7B1A16B6-D7FD-45E1-95D8-250D2A46F7CE}\mpengine.dll
2012-12-09 22:25 . 2012-12-09 22:25--------d-----w-c:\users\Jonathan\AppData\Local\Avg2013
2012-12-09 22:20 . 2012-12-09 22:20--------d-----w-c:\windows\system32\SPReview
2012-12-09 22:20 . 2012-12-09 22:20--------d-----w-c:\windows\system32\EventProviders
2012-12-09 22:19 . 2012-10-29 21:0466395536----a-w-c:\windows\system32\MRT.exe
2012-12-09 22:18 . 2012-10-18 18:253149824----a-w-c:\windows\system32\win32k.sys
2012-12-09 22:18 . 2012-09-25 22:4778336----a-w-c:\windows\SysWow64\synceng.dll
2012-12-09 22:18 . 2012-09-25 22:4695744----a-w-c:\windows\system32\synceng.dll
2012-12-09 20:39 . 2012-12-09 20:39--------d-----w-c:\users\Jonathan\AppData\Roaming\TuneUp Software
2012-12-09 20:32 . 2012-12-09 22:25--------d-----w-c:\programdata\MFAData
2012-12-09 20:32 . 2012-12-09 20:32--------d--h--w-c:\programdata\Common Files
2012-12-09 20:32 . 2012-12-09 20:32--------d-----w-c:\users\Jonathan\AppData\Local\MFAData
2012-12-07 23:23 . 2012-12-07 23:23--------d-----w-C:\Games
2012-12-07 23:23 . 2012-12-07 23:23--------d-----w-c:\users\Jonathan\AppData\Local\Black_Tree_Gaming
2012-12-07 23:23 . 2012-12-07 23:23--------d-----w-c:\program files\Nexus Mod Manager
2012-12-07 14:29 . 2012-12-07 14:29--------d-----w-c:\users\Jonathan\AppData\Local\Chromium
2012-12-07 13:48 . 2012-12-09 23:10--------d-----w-c:\program files (x86)\SEGA
2012-12-06 15:05 . 2012-12-06 15:05--------d-----r-C:\Kernels
2012-12-05 12:45 . 2012-12-07 14:25--------d-----w-c:\users\Jonathan\AppData\Roaming\Sports Interactive
2012-12-05 12:45 . 2012-12-05 12:45--------d-----w-c:\users\Jonathan\AppData\Local\Sports Interactive
2012-12-05 12:42 . 2012-12-06 15:04--------d-----w-C:\Temp
2012-12-04 22:27 . 2012-12-06 15:35281688----a-w-c:\windows\SysWow64\PnkBstrB.xtr
2012-12-04 22:27 . 2012-12-04 22:27--------d-----w-c:\users\Jonathan\AppData\Local\PunkBuster
2012-11-28 00:22 . 2012-12-04 22:27--------d-----w-c:\programdata\Orbit
2012-11-27 16:48 . 2012-11-27 16:50--------d-----w-c:\windows\SysWow64\_CIConfig
2012-11-27 16:48 . 2012-11-27 16:48--------d-----w-c:\users\Jonathan\AppData\Local\SCRiN
2012-11-26 18:12 . 2012-11-26 20:01--------d-----w-c:\program files (x86)\StarCraft II
2012-11-26 16:40 . 2012-11-27 13:02--------d-----w-c:\program files (x86)\Common Files\Blizzard Entertainment
2012-11-26 16:40 . 2012-11-26 18:20--------d-----w-c:\programdata\Blizzard Entertainment
2012-11-26 16:40 . 2012-11-26 16:40--------d-----w-c:\programdata\Battle.net
2012-11-25 11:36 . 2012-11-25 21:37--------d-----w-c:\program files (x86)\Dragon Age 2
2012-11-25 11:36 . 2012-11-25 11:39--------d-----w-c:\program files (x86)\Common Files\BioWare
2012-11-24 15:30 . 2012-11-24 15:30--------d-----w-c:\program files (x86)\SQUARE ENIX
2012-11-24 01:03 . 2012-11-24 01:03--------d-----w-c:\programdata\REVOLT
2012-11-21 13:10 . 2012-11-21 13:103123272----a-r-c:\windows\SysWow64\pbsvc.exe
.
.
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2012-12-09 22:24 . 2009-07-14 02:36175616----a-w-c:\windows\system32\msclmd.dll
2012-12-09 22:24 . 2009-07-14 02:36152576----a-w-c:\windows\SysWow64\msclmd.dll
2012-12-06 15:35 . 2012-11-09 16:02281688----a-w-c:\windows\SysWow64\PnkBstrB.exe
2012-12-05 13:25 . 2012-11-09 16:02281688----a-w-c:\windows\SysWow64\PnkBstrB.ex0
2012-12-03 22:30 . 2012-11-09 16:0276888----a-w-c:\windows\SysWow64\PnkBstrA.exe
2012-11-04 19:25 . 2012-11-04 19:2595208----a-w-c:\windows\SysWow64\WindowsAccessBridge-32.dll
2012-11-04 19:25 . 2012-11-04 19:25821736----a-w-c:\windows\SysWow64\npDeployJava1.dll
2012-11-04 19:25 . 2012-11-04 19:25746984----a-w-c:\windows\SysWow64\deployJava1.dll
2012-10-31 12:47 . 2012-10-31 12:4791648----a-w-c:\windows\system32\SetIEInstalledDate.exe
2012-10-31 12:47 . 2012-10-31 12:4789088----a-w-c:\windows\system32\RegisterIEPKEYs.exe
2012-10-31 12:47 . 2012-10-31 12:4789088----a-w-c:\windows\system32\ie4uinit.exe
2012-10-31 12:47 . 2012-10-31 12:4786528----a-w-c:\windows\SysWow64\iesysprep.dll
2012-10-31 12:47 . 2012-10-31 12:4785504----a-w-c:\windows\system32\iesetup.dll
2012-10-31 12:47 . 2012-10-31 12:4782432----a-w-c:\windows\system32\icardie.dll
2012-10-31 12:47 . 2012-10-31 12:4776800----a-w-c:\windows\SysWow64\SetIEInstalledDate.exe
2012-10-31 12:47 . 2012-10-31 12:4776800----a-w-c:\windows\system32\tdc.ocx
2012-10-31 12:47 . 2012-10-31 12:4774752----a-w-c:\windows\SysWow64\RegisterIEPKEYs.exe
2012-10-31 12:47 . 2012-10-31 12:4774752----a-w-c:\windows\SysWow64\iesetup.dll
2012-10-31 12:47 . 2012-10-31 12:4765024----a-w-c:\windows\system32\pngfilt.dll
2012-10-31 12:47 . 2012-10-31 12:4763488----a-w-c:\windows\SysWow64\tdc.ocx
2012-10-31 12:47 . 2012-10-31 12:4755296----a-w-c:\windows\system32\msfeedsbs.dll
2012-10-31 12:47 . 2012-10-31 12:47534528----a-w-c:\windows\system32\ieapfltr.dll
2012-10-31 12:47 . 2012-10-31 12:4749664----a-w-c:\windows\system32\imgutil.dll
2012-10-31 12:47 . 2012-10-31 12:4748640----a-w-c:\windows\SysWow64\mshtmler.dll
2012-10-31 12:47 . 2012-10-31 12:4748640----a-w-c:\windows\system32\mshtmler.dll
2012-10-31 12:47 . 2012-10-31 12:47452608----a-w-c:\windows\system32\dxtmsft.dll
2012-10-31 12:47 . 2012-10-31 12:47448512----a-w-c:\windows\system32\html.iec
2012-10-31 12:47 . 2012-10-31 12:47403248----a-w-c:\windows\system32\iedkcs32.dll
2012-10-31 12:47 . 2012-10-31 12:4739936----a-w-c:\windows\system32\iernonce.dll
2012-10-31 12:47 . 2012-10-31 12:473695416----a-w-c:\windows\system32\ieapfltr.dat
2012-10-31 12:47 . 2012-10-31 12:47367104----a-w-c:\windows\SysWow64\html.iec
2012-10-31 12:47 . 2012-10-31 12:4735840----a-w-c:\windows\SysWow64\imgutil.dll
2012-10-31 12:47 . 2012-10-31 12:4730720----a-w-c:\windows\system32\licmgr10.dll
2012-10-31 12:47 . 2012-10-31 12:47282112----a-w-c:\windows\system32\dxtrans.dll
2012-10-31 12:47 . 2012-10-31 12:47267776----a-w-c:\windows\system32\ieaksie.dll
2012-10-31 12:47 . 2012-10-31 12:47249344----a-w-c:\windows\system32\webcheck.dll
2012-10-31 12:47 . 2012-10-31 12:4723552----a-w-c:\windows\SysWow64\licmgr10.dll
2012-10-31 12:47 . 2012-10-31 12:47222208----a-w-c:\windows\system32\msls31.dll
2012-10-31 12:47 . 2012-10-31 12:47197120----a-w-c:\windows\system32\msrating.dll
2012-10-31 12:47 . 2012-10-31 12:47165888----a-w-c:\windows\system32\iexpress.exe
2012-10-31 12:47 . 2012-10-31 12:47163840----a-w-c:\windows\system32\ieakui.dll
2012-10-31 12:47 . 2012-10-31 12:47161792----a-w-c:\windows\SysWow64\msls31.dll
2012-10-31 12:47 . 2012-10-31 12:47160256----a-w-c:\windows\system32\wextract.exe
2012-10-31 12:47 . 2012-10-31 12:47160256----a-w-c:\windows\system32\ieakeng.dll
2012-10-31 12:47 . 2012-10-31 12:47152064----a-w-c:\windows\SysWow64\wextract.exe
2012-10-31 12:47 . 2012-10-31 12:47150528----a-w-c:\windows\SysWow64\iexpress.exe
2012-10-31 12:47 . 2012-10-31 12:47149504----a-w-c:\windows\system32\occache.dll
2012-10-31 12:47 . 2012-10-31 12:47145920----a-w-c:\windows\system32\iepeers.dll
2012-10-31 12:47 . 2012-10-31 12:47135168----a-w-c:\windows\system32\IEAdvpack.dll
2012-10-31 12:47 . 2012-10-31 12:4712288----a-w-c:\windows\system32\mshta.exe
2012-10-31 12:47 . 2012-10-31 12:4711776----a-w-c:\windows\SysWow64\mshta.exe
2012-10-31 12:47 . 2012-10-31 12:47114176----a-w-c:\windows\system32\admparse.dll
2012-10-31 12:47 . 2012-10-31 12:47111616----a-w-c:\windows\system32\iesysprep.dll
2012-10-31 12:47 . 2012-10-31 12:47110592----a-w-c:\windows\SysWow64\IEAdvpack.dll
2012-10-31 12:47 . 2012-10-31 12:4710752----a-w-c:\windows\system32\msfeedssync.exe
2012-10-31 12:47 . 2012-10-31 12:47103936----a-w-c:\windows\system32\inseng.dll
2012-10-31 12:47 . 2012-10-31 12:47101888----a-w-c:\windows\SysWow64\admparse.dll
2012-10-30 15:38 . 2012-10-30 15:38254528----a-w-c:\windows\system32\drivers\dtsoftbus01.sys
2012-10-30 14:53 . 2012-10-30 14:5316896----a-w-c:\windows\AsTaskSched.dll
2012-10-29 09:05 . 2012-10-30 14:5753248----a-w-c:\windows\SysWow64\CSVer.dll
2012-10-02 22:21 . 2012-10-30 15:1860776----a-w-c:\windows\system32\OpenCL.dll
2012-10-02 22:21 . 2012-10-30 15:1852584----a-w-c:\windows\SysWow64\OpenCL.dll
2012-10-02 22:21 . 2012-10-30 15:18973672----a-w-c:\windows\system32\nvumdshimx.dll
2012-10-02 22:21 . 2012-10-30 15:189146728----a-w-c:\windows\system32\nvcuda.dll
2012-10-02 22:21 . 2012-10-30 15:18831848----a-w-c:\windows\SysWow64\nvumdshim.dll
2012-10-02 22:21 . 2012-10-30 15:187697768----a-w-c:\windows\SysWow64\nvcuda.dll
2012-10-02 22:21 . 2012-10-30 15:187414632----a-w-c:\windows\system32\nvopencl.dll
2012-10-02 22:21 . 2012-10-30 15:186127464----a-w-c:\windows\SysWow64\nvopencl.dll
2012-10-02 22:21 . 2012-10-30 15:18364904----a-w-c:\windows\system32\nvEncodeAPI64.dll
2012-10-02 22:21 . 2012-10-30 15:18313704----a-w-c:\windows\SysWow64\nvEncodeAPI.dll
2012-10-02 22:21 . 2012-10-30 15:182747240----a-w-c:\windows\system32\nvcuvid.dll
2012-10-02 22:21 . 2012-10-30 15:182731880----a-w-c:\windows\system32\nvapi64.dll
2012-10-02 22:21 . 2012-10-30 15:1826331496----a-w-c:\windows\system32\nvoglv64.dll
2012-10-02 22:21 . 2012-10-30 15:182574696----a-w-c:\windows\SysWow64\nvcuvid.dll
2012-10-02 22:21 . 2012-10-30 15:1825256296----a-w-c:\windows\system32\nvcompiler.dll
2012-10-02 22:21 . 2012-10-30 15:18247144----a-w-c:\windows\system32\nvinitx.dll
2012-10-02 22:21 . 2012-10-30 15:182428776----a-w-c:\windows\SysWow64\nvapi.dll
2012-10-02 22:21 . 2012-10-30 15:182218344----a-w-c:\windows\system32\nvcuvenc.dll
2012-10-02 22:21 . 2012-10-30 15:18202600----a-w-c:\windows\SysWow64\nvinit.dll
2012-10-02 22:21 . 2012-10-30 15:1819906920----a-w-c:\windows\SysWow64\nvoglv32.dll
2012-10-02 22:21 . 2012-10-30 15:181867112----a-w-c:\windows\SysWow64\nvcuvenc.dll
2012-10-02 22:21 . 2012-10-30 15:1818252136----a-w-c:\windows\system32\nvd3dumx.dll
2012-10-02 22:21 . 2012-10-30 15:181760104----a-w-c:\windows\system32\nvdispco64.dll
2012-10-02 22:21 . 2012-10-30 15:1817559912----a-w-c:\windows\SysWow64\nvcompiler.dll
2012-10-02 22:21 . 2012-10-30 15:1815309160----a-w-c:\windows\SysWow64\nvd3dum.dll
2012-10-02 22:21 . 2012-10-30 15:1814922600----a-w-c:\windows\system32\nvwgf2umx.dll
2012-10-02 22:21 . 2012-10-30 15:181482600----a-w-c:\windows\system32\nvdispgenco64.dll
2012-10-02 22:21 . 2012-10-30 15:1813443944----a-w-c:\windows\system32\drivers\nvlddmkm.sys
2012-10-02 22:21 . 2012-10-30 15:1812501352----a-w-c:\windows\SysWow64\nvwgf2um.dll
2012-10-02 19:51 . 2012-10-31 15:283536817----a-w-c:\windows\system32\nvcoproc.bin
2012-10-02 19:51 . 2012-10-31 15:283293544----a-w-c:\windows\system32\nvsvc64.dll
2012-10-02 19:51 . 2012-10-31 15:286200680----a-w-c:\windows\system32\nvcpl.dll
2012-10-02 19:50 . 2012-10-31 15:28891240----a-w-c:\windows\system32\nvvsvc.exe
2012-10-02 19:50 . 2012-10-31 15:2863336----a-w-c:\windows\system32\nvshext.dll
2012-10-02 19:50 . 2012-10-31 15:282557800----a-w-c:\windows\system32\nvsvcr.dll
2012-10-02 19:50 . 2012-10-31 15:28118120----a-w-c:\windows\system32\nvmctray.dll
2012-10-02 13:15 . 2012-10-02 13:15430952----a-w-c:\windows\SysWow64\nvStreaming.exe
2012-09-14 19:19 . 2012-10-31 11:202048----a-w-c:\windows\system32\tzres.dll
2012-09-14 18:28 . 2012-10-31 11:202048----a-w-c:\windows\SysWow64\tzres.dll
.
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
.
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"DAEMON Tools Pro Agent"="c:\program files (x86)\DAEMON Tools Pro\DTAgent.exe" [2011-03-18 839488]
"Sidebar"="c:\program files\Windows Sidebar\sidebar.exe" [2010-11-20 1475584]
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
"USB3MON"="c:\program files (x86)\Intel\Intel(R) USB 3.0 eXtensible Host Controller Driver\Application\iusb3mon.exe" [2012-03-26 291608]
"Adobe Reader Speed Launcher"="c:\program files (x86)\Adobe\Reader 10.0\Reader\Reader_sl.exe" [2012-07-27 35768]
"Adobe ARM"="c:\program files (x86)\Common Files\Adobe\ARM\1.0\AdobeARM.exe" [2012-07-27 919008]
"SunJavaUpdateSched"="c:\program files (x86)\Common Files\Java\Java Update\jusched.exe" [2012-07-03 252848]
"Adobe"="c:\programdata\Adobe\56CF60.vbe" [2012-10-02 7147]
"AVP"="c:\program files (x86)\Kaspersky Lab\Kaspersky Anti-Virus 2011\avp.exe" [2012-12-10 365336]
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\policies\system]
"ConsentPromptBehaviorAdmin"= 5 (0x5)
"ConsentPromptBehaviorUser"= 3 (0x3)
"EnableUIADesktopToggle"= 0 (0x0)
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\policies\explorer]
"HideSCAHealth"= 1 (0x1)
.
[HKEY_LOCAL_MACHINE\software\microsoft\security center\Monitoring\KasperskyAntiVirus]
"DisableMonitoring"=dword:00000001
.
R3 RdpVideoMiniport;Remote Desktop Video Miniport Driver;c:\windows\system32\drivers\rdpvideominiport.sys [2010-11-20 20992]
R3 Synth3dVsc;Synth3dVsc;c:\windows\system32\drivers\synth3dvsc.sys [x]
R3 TsUsbFlt;TsUsbFlt;c:\windows\system32\drivers\tsusbflt.sys [2010-11-20 59392]
R3 tsusbhub;tsusbhub;c:\windows\system32\drivers\tsusbhub.sys [x]
R3 VGPU;VGPU;c:\windows\system32\drivers\rdvgkmd.sys [x]
R3 WatAdminSvc;Windows Activation Technologies Service;c:\windows\system32\Wat\WatAdminSvc.exe [2012-10-31 1255736]
S0 iusb3hcs;Intel(R) USB 3.0 Host Controller Switch Driver;c:\windows\system32\DRIVERS\iusb3hcs.sys [2012-03-26 19224]
S1 dtsoftbus01;DAEMON Tools Virtual Bus Driver;c:\windows\system32\DRIVERS\dtsoftbus01.sys [2012-10-30 254528]
S1 kl2;kl2;c:\windows\system32\DRIVERS\kl2.sys [2010-06-09 11864]
S1 KLIM6;Kaspersky Anti-Virus NDIS 6 Filter;c:\windows\system32\DRIVERS\klim6.sys [2010-04-22 27736]
S2 cpuz135;cpuz135;c:\windows\system32\drivers\cpuz135_x64.sys [2012-03-09 23816]
S2 DTSAudioSvc;DTSAudioSvc;c:\program files\Realtek\Audio\HDA\DTSU2PAuSrv64.exe [2012-01-23 233328]
S2 Intel(R) PROSet Monitoring Service;Intel(R) PROSet Monitoring Service;c:\windows\system32\IProsetMonitor.exe [2011-11-09 189608]
S2 Stereo Service;NVIDIA Stereoscopic 3D Driver Service;c:\program files (x86)\NVIDIA Corporation\3D Vision\nvSCPAPISvr.exe [2012-10-02 382824]
S3 ALSysIO;ALSysIO;c:\users\Jonathan\AppData\Local\Temp\ALSysIO64.sys [x]
S3 iusb3hub;Intel(R) USB 3.0 Hub Driver;c:\windows\system32\DRIVERS\iusb3hub.sys [2012-03-26 356632]
S3 iusb3xhc;Intel(R) USB 3.0 eXtensible Host Controller Driver;c:\windows\system32\DRIVERS\iusb3xhc.sys [2012-03-26 789272]
S3 klmouflt;Kaspersky Lab KLMOUFLT;c:\windows\system32\DRIVERS\klmouflt.sys [2009-11-02 22544]
.
.
Contents of the 'Scheduled Tasks' folder
.
2012-12-10 c:\windows\Tasks\GoogleUpdateTaskMachineCore.job
- c:\program files (x86)\Google\Update\GoogleUpdate.exe [2012-10-30 15:01]
.
2012-12-09 c:\windows\Tasks\GoogleUpdateTaskMachineUA.job
- c:\program files (x86)\Google\Update\GoogleUpdate.exe [2012-10-30 15:01]
.
.
--------- X64 Entries -----------
.
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"RTHDVCPL"="c:\program files\Realtek\Audio\HDA\RtkNGUI64.exe" [2012-05-15 6470760]
"RtHDVBg_DTS"="c:\program files\Realtek\Audio\HDA\RAVBg64.exe" [2012-05-11 1175656]
.
------- Supplementary Scan -------
.
uLocal Page = c:\windows\system32\blank.htm
mLocal Page = c:\windows\SysWOW64\blank.htm
TCP: DhcpNameServer = 192.168.1.254 192.168.1.254
.
.
--------------------- LOCKED REGISTRY KEYS ---------------------
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{19114156-8E9A-4D4E-9EE9-17A0E48D3BBB}]
@Denied: (A 2) (Everyone)
@="FlashBroker"
"LocalizedString"="@c:\\Windows\\system32\\Macromed\\Flash\\FlashUtil10d.exe,-101"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{19114156-8E9A-4D4E-9EE9-17A0E48D3BBB}\Elevation]
"Enabled"=dword:00000001
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{19114156-8E9A-4D4E-9EE9-17A0E48D3BBB}\LocalServer32]
@="c:\\Windows\\SysWow64\\Macromed\\Flash\\FlashUtil10d.exe"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{19114156-8E9A-4D4E-9EE9-17A0E48D3BBB}\TypeLib]
@="{FAB3E735-69C7-453B-A446-B6823C6DF1C9}"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB6E-AE6D-11cf-96B8-444553540000}]
@Denied: (A 2) (Everyone)
@="Shockwave Flash Object"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB6E-AE6D-11cf-96B8-444553540000}\InprocServer32]
@="c:\\Windows\\SysWow64\\Macromed\\Flash\\Flash10d.ocx"
"ThreadingModel"="Apartment"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB6E-AE6D-11cf-96B8-444553540000}\MiscStatus]
@="0"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB6E-AE6D-11cf-96B8-444553540000}\ProgID]
@="ShockwaveFlash.ShockwaveFlash.10"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB6E-AE6D-11cf-96B8-444553540000}\ToolboxBitmap32]
@="c:\\Windows\\SysWow64\\Macromed\\Flash\\Flash10d.ocx, 1"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB6E-AE6D-11cf-96B8-444553540000}\TypeLib]
@="{D27CDB6B-AE6D-11cf-96B8-444553540000}"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB6E-AE6D-11cf-96B8-444553540000}\Version]
@="1.0"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB6E-AE6D-11cf-96B8-444553540000}\VersionIndependentProgID]
@="ShockwaveFlash.ShockwaveFlash"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB70-AE6D-11cf-96B8-444553540000}]
@Denied: (A 2) (Everyone)
@="Macromedia Flash Factory Object"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB70-AE6D-11cf-96B8-444553540000}\InprocServer32]
@="c:\\Windows\\SysWow64\\Macromed\\Flash\\Flash10d.ocx"
"ThreadingModel"="Apartment"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB70-AE6D-11cf-96B8-444553540000}\ProgID]
@="FlashFactory.FlashFactory.1"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB70-AE6D-11cf-96B8-444553540000}\ToolboxBitmap32]
@="c:\\Windows\\SysWow64\\Macromed\\Flash\\Flash10d.ocx, 1"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB70-AE6D-11cf-96B8-444553540000}\TypeLib]
@="{D27CDB6B-AE6D-11cf-96B8-444553540000}"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB70-AE6D-11cf-96B8-444553540000}\Version]
@="1.0"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB70-AE6D-11cf-96B8-444553540000}\VersionIndependentProgID]
@="FlashFactory.FlashFactory"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\Interface\{1D4C8A81-B7AC-460A-8C23-98713C41D6B3}]
@Denied: (A 2) (Everyone)
@="IFlashBroker3"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\Interface\{1D4C8A81-B7AC-460A-8C23-98713C41D6B3}\ProxyStubClsid32]
@="{00020424-0000-0000-C000-000000000046}"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\Interface\{1D4C8A81-B7AC-460A-8C23-98713C41D6B3}\TypeLib]
@="{FAB3E735-69C7-453B-A446-B6823C6DF1C9}"
"Version"="1.0"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\VideoLAN.VLCPlugin.*1*]
@="?????????????????? v1"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\VideoLAN.VLCPlugin.*1*\CLSID]
@="{E23FE9C6-778E-49D4-B537-38FCDE4887D8}"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\VideoLAN.VLCPlugin.*2*]
@="?????????????????? v2"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\VideoLAN.VLCPlugin.*2*\CLSID]
@="{9BE31822-FDAD-461B-AD51-BE1D1C159921}"
.
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\PCW\Security]
@Denied: (Full) (Everyone)
.
Completion time: 2012-12-10 11:03:53
ComboFix-quarantined-files.txt 2012-12-10 11:03
ComboFix2.txt 2012-12-10 10:53
.
Pre-Run: 227,437,318,144 bytes free
Post-Run: 227,354,509,312 bytes free
.
- - End Of File - - 023B152F55C8A6264C094CB2FF461C3B
Malwarebytes Anti-Malware 1.65.1.1000
www.malwarebytes.org
Database version: v2012.12.10.01
Windows 7 Service Pack 1 x64 NTFS
Internet Explorer 9.0.8112.16421
Jonathan :: JONATHAN-PC [administrator]
10/12/2012 02:08:13
mbam-log-2012-12-10 (02-08-13).txt
Scan type: Quick scan
Scan options enabled: Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken | PUP | PUM
Scan options disabled: P2P
Objects scanned: 221663
Time elapsed: 1 minute(s), 15 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 0
(No malicious items detected)
Registry Values Detected: 1
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run|win32 (Trojan.StartPage) -> Data: "C:\kernels\drivers.vbs" -> Quarantined and deleted successfully.
Registry Data Items Detected: 0
(No malicious items detected)
Folders Detected: 0
(No malicious items detected)
Files Detected: 3
C:\win32.exe (Trojan.Agent) -> Quarantined and deleted successfully.
C:\Users\Jonathan\AppData\Local\Temp\svchost.exe (Trojan.Agent.Gen) -> Quarantined and deleted successfully.
C:\Kernels\drivers.vbs (Trojan.StartPage) -> Quarantined and deleted successfully.
(end)
Thank you in advance for any help given! The problem is that I have a virus which shows up as svchost.exe*32 in my task manager, when I see its properties, it originates from my appdata/temp folder. This definitely cant be right. I also had the same thing but with a 'win32*32' on my C:/. Malwarebytes got rid of that one and hasnt come back. Malwarebytes also detects the svchost.exe and deletes on reboot. But when I reboot, it's still there. Even when I browse to the file, find the offending svchost file, delete it. once rebooted it returns...
ComboFix 12-12-07.01 - Jonathan 10/12/2012 10:58:22.2.4 - x64
Microsoft Windows 7 Ultimate 6.1.7601.1.1252.44.1033.18.32715.30302 [GMT 0:00]
Running from: c:\users\Jonathan\Downloads\ComboFix.exe
AV: Kaspersky Anti-Virus *Disabled/Outdated* {2EAA32A5-1EE1-1B22-95DA-337730C6E984}
FW: Kaspersky Anti-Virus *Disabled* {1691B380-548E-1A7A-BE85-9A42CE15AEFF}
SP: Kaspersky Anti-Virus *Disabled/Updated* {95CBD341-38DB-14AC-AF6A-08054B41A339}
SP: Windows Defender *Enabled/Updated* {D68DDC3A-831F-4fae-9E44-DA132C1ACF46}
.
.
((((((((((((((((((((((((( Files Created from 2012-11-10 to 2012-12-10 )))))))))))))))))))))))))))))))
.
.
2012-12-10 11:03 . 2012-12-10 11:03--------d-----w-c:\users\UpdatusUser\AppData\Local\temp
2012-12-10 11:03 . 2012-12-10 11:03--------d-----w-c:\users\Default\AppData\Local\temp
2012-12-10 02:07 . 2012-12-10 02:07--------d-----w-c:\users\Jonathan\AppData\Roaming\Malwarebytes
2012-12-10 02:07 . 2012-12-10 02:07--------d-----w-c:\programdata\Malwarebytes
2012-12-10 02:07 . 2012-12-10 02:07--------d-----w-c:\program files (x86)\Malwarebytes' Anti-Malware
2012-12-10 02:07 . 2012-09-29 19:5425928----a-w-c:\windows\system32\drivers\mbam.sys
2012-12-10 00:04 . 2012-12-10 02:01--------d-----w-c:\program files (x86)\stinger
2012-12-09 22:30 . 2012-12-10 10:57--------d-----w-c:\programdata\Kaspersky Lab
2012-12-09 22:30 . 2012-12-09 22:30--------d-----w-c:\program files (x86)\Kaspersky Lab
2012-12-09 22:30 . 2012-12-09 22:30556120----a-w-c:\windows\system32\drivers\klif.sys
2012-12-09 22:25 . 2012-11-08 17:249125352----a-w-c:\programdata\Microsoft\Windows Defender\Definition Updates\{7B1A16B6-D7FD-45E1-95D8-250D2A46F7CE}\mpengine.dll
2012-12-09 22:25 . 2012-12-09 22:25--------d-----w-c:\users\Jonathan\AppData\Local\Avg2013
2012-12-09 22:20 . 2012-12-09 22:20--------d-----w-c:\windows\system32\SPReview
2012-12-09 22:20 . 2012-12-09 22:20--------d-----w-c:\windows\system32\EventProviders
2012-12-09 22:19 . 2012-10-29 21:0466395536----a-w-c:\windows\system32\MRT.exe
2012-12-09 22:18 . 2012-10-18 18:253149824----a-w-c:\windows\system32\win32k.sys
2012-12-09 22:18 . 2012-09-25 22:4778336----a-w-c:\windows\SysWow64\synceng.dll
2012-12-09 22:18 . 2012-09-25 22:4695744----a-w-c:\windows\system32\synceng.dll
2012-12-09 20:39 . 2012-12-09 20:39--------d-----w-c:\users\Jonathan\AppData\Roaming\TuneUp Software
2012-12-09 20:32 . 2012-12-09 22:25--------d-----w-c:\programdata\MFAData
2012-12-09 20:32 . 2012-12-09 20:32--------d--h--w-c:\programdata\Common Files
2012-12-09 20:32 . 2012-12-09 20:32--------d-----w-c:\users\Jonathan\AppData\Local\MFAData
2012-12-07 23:23 . 2012-12-07 23:23--------d-----w-C:\Games
2012-12-07 23:23 . 2012-12-07 23:23--------d-----w-c:\users\Jonathan\AppData\Local\Black_Tree_Gaming
2012-12-07 23:23 . 2012-12-07 23:23--------d-----w-c:\program files\Nexus Mod Manager
2012-12-07 14:29 . 2012-12-07 14:29--------d-----w-c:\users\Jonathan\AppData\Local\Chromium
2012-12-07 13:48 . 2012-12-09 23:10--------d-----w-c:\program files (x86)\SEGA
2012-12-06 15:05 . 2012-12-06 15:05--------d-----r-C:\Kernels
2012-12-05 12:45 . 2012-12-07 14:25--------d-----w-c:\users\Jonathan\AppData\Roaming\Sports Interactive
2012-12-05 12:45 . 2012-12-05 12:45--------d-----w-c:\users\Jonathan\AppData\Local\Sports Interactive
2012-12-05 12:42 . 2012-12-06 15:04--------d-----w-C:\Temp
2012-12-04 22:27 . 2012-12-06 15:35281688----a-w-c:\windows\SysWow64\PnkBstrB.xtr
2012-12-04 22:27 . 2012-12-04 22:27--------d-----w-c:\users\Jonathan\AppData\Local\PunkBuster
2012-11-28 00:22 . 2012-12-04 22:27--------d-----w-c:\programdata\Orbit
2012-11-27 16:48 . 2012-11-27 16:50--------d-----w-c:\windows\SysWow64\_CIConfig
2012-11-27 16:48 . 2012-11-27 16:48--------d-----w-c:\users\Jonathan\AppData\Local\SCRiN
2012-11-26 18:12 . 2012-11-26 20:01--------d-----w-c:\program files (x86)\StarCraft II
2012-11-26 16:40 . 2012-11-27 13:02--------d-----w-c:\program files (x86)\Common Files\Blizzard Entertainment
2012-11-26 16:40 . 2012-11-26 18:20--------d-----w-c:\programdata\Blizzard Entertainment
2012-11-26 16:40 . 2012-11-26 16:40--------d-----w-c:\programdata\Battle.net
2012-11-25 11:36 . 2012-11-25 21:37--------d-----w-c:\program files (x86)\Dragon Age 2
2012-11-25 11:36 . 2012-11-25 11:39--------d-----w-c:\program files (x86)\Common Files\BioWare
2012-11-24 15:30 . 2012-11-24 15:30--------d-----w-c:\program files (x86)\SQUARE ENIX
2012-11-24 01:03 . 2012-11-24 01:03--------d-----w-c:\programdata\REVOLT
2012-11-21 13:10 . 2012-11-21 13:103123272----a-r-c:\windows\SysWow64\pbsvc.exe
.
.
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2012-12-09 22:24 . 2009-07-14 02:36175616----a-w-c:\windows\system32\msclmd.dll
2012-12-09 22:24 . 2009-07-14 02:36152576----a-w-c:\windows\SysWow64\msclmd.dll
2012-12-06 15:35 . 2012-11-09 16:02281688----a-w-c:\windows\SysWow64\PnkBstrB.exe
2012-12-05 13:25 . 2012-11-09 16:02281688----a-w-c:\windows\SysWow64\PnkBstrB.ex0
2012-12-03 22:30 . 2012-11-09 16:0276888----a-w-c:\windows\SysWow64\PnkBstrA.exe
2012-11-04 19:25 . 2012-11-04 19:2595208----a-w-c:\windows\SysWow64\WindowsAccessBridge-32.dll
2012-11-04 19:25 . 2012-11-04 19:25821736----a-w-c:\windows\SysWow64\npDeployJava1.dll
2012-11-04 19:25 . 2012-11-04 19:25746984----a-w-c:\windows\SysWow64\deployJava1.dll
2012-10-31 12:47 . 2012-10-31 12:4791648----a-w-c:\windows\system32\SetIEInstalledDate.exe
2012-10-31 12:47 . 2012-10-31 12:4789088----a-w-c:\windows\system32\RegisterIEPKEYs.exe
2012-10-31 12:47 . 2012-10-31 12:4789088----a-w-c:\windows\system32\ie4uinit.exe
2012-10-31 12:47 . 2012-10-31 12:4786528----a-w-c:\windows\SysWow64\iesysprep.dll
2012-10-31 12:47 . 2012-10-31 12:4785504----a-w-c:\windows\system32\iesetup.dll
2012-10-31 12:47 . 2012-10-31 12:4782432----a-w-c:\windows\system32\icardie.dll
2012-10-31 12:47 . 2012-10-31 12:4776800----a-w-c:\windows\SysWow64\SetIEInstalledDate.exe
2012-10-31 12:47 . 2012-10-31 12:4776800----a-w-c:\windows\system32\tdc.ocx
2012-10-31 12:47 . 2012-10-31 12:4774752----a-w-c:\windows\SysWow64\RegisterIEPKEYs.exe
2012-10-31 12:47 . 2012-10-31 12:4774752----a-w-c:\windows\SysWow64\iesetup.dll
2012-10-31 12:47 . 2012-10-31 12:4765024----a-w-c:\windows\system32\pngfilt.dll
2012-10-31 12:47 . 2012-10-31 12:4763488----a-w-c:\windows\SysWow64\tdc.ocx
2012-10-31 12:47 . 2012-10-31 12:4755296----a-w-c:\windows\system32\msfeedsbs.dll
2012-10-31 12:47 . 2012-10-31 12:47534528----a-w-c:\windows\system32\ieapfltr.dll
2012-10-31 12:47 . 2012-10-31 12:4749664----a-w-c:\windows\system32\imgutil.dll
2012-10-31 12:47 . 2012-10-31 12:4748640----a-w-c:\windows\SysWow64\mshtmler.dll
2012-10-31 12:47 . 2012-10-31 12:4748640----a-w-c:\windows\system32\mshtmler.dll
2012-10-31 12:47 . 2012-10-31 12:47452608----a-w-c:\windows\system32\dxtmsft.dll
2012-10-31 12:47 . 2012-10-31 12:47448512----a-w-c:\windows\system32\html.iec
2012-10-31 12:47 . 2012-10-31 12:47403248----a-w-c:\windows\system32\iedkcs32.dll
2012-10-31 12:47 . 2012-10-31 12:4739936----a-w-c:\windows\system32\iernonce.dll
2012-10-31 12:47 . 2012-10-31 12:473695416----a-w-c:\windows\system32\ieapfltr.dat
2012-10-31 12:47 . 2012-10-31 12:47367104----a-w-c:\windows\SysWow64\html.iec
2012-10-31 12:47 . 2012-10-31 12:4735840----a-w-c:\windows\SysWow64\imgutil.dll
2012-10-31 12:47 . 2012-10-31 12:4730720----a-w-c:\windows\system32\licmgr10.dll
2012-10-31 12:47 . 2012-10-31 12:47282112----a-w-c:\windows\system32\dxtrans.dll
2012-10-31 12:47 . 2012-10-31 12:47267776----a-w-c:\windows\system32\ieaksie.dll
2012-10-31 12:47 . 2012-10-31 12:47249344----a-w-c:\windows\system32\webcheck.dll
2012-10-31 12:47 . 2012-10-31 12:4723552----a-w-c:\windows\SysWow64\licmgr10.dll
2012-10-31 12:47 . 2012-10-31 12:47222208----a-w-c:\windows\system32\msls31.dll
2012-10-31 12:47 . 2012-10-31 12:47197120----a-w-c:\windows\system32\msrating.dll
2012-10-31 12:47 . 2012-10-31 12:47165888----a-w-c:\windows\system32\iexpress.exe
2012-10-31 12:47 . 2012-10-31 12:47163840----a-w-c:\windows\system32\ieakui.dll
2012-10-31 12:47 . 2012-10-31 12:47161792----a-w-c:\windows\SysWow64\msls31.dll
2012-10-31 12:47 . 2012-10-31 12:47160256----a-w-c:\windows\system32\wextract.exe
2012-10-31 12:47 . 2012-10-31 12:47160256----a-w-c:\windows\system32\ieakeng.dll
2012-10-31 12:47 . 2012-10-31 12:47152064----a-w-c:\windows\SysWow64\wextract.exe
2012-10-31 12:47 . 2012-10-31 12:47150528----a-w-c:\windows\SysWow64\iexpress.exe
2012-10-31 12:47 . 2012-10-31 12:47149504----a-w-c:\windows\system32\occache.dll
2012-10-31 12:47 . 2012-10-31 12:47145920----a-w-c:\windows\system32\iepeers.dll
2012-10-31 12:47 . 2012-10-31 12:47135168----a-w-c:\windows\system32\IEAdvpack.dll
2012-10-31 12:47 . 2012-10-31 12:4712288----a-w-c:\windows\system32\mshta.exe
2012-10-31 12:47 . 2012-10-31 12:4711776----a-w-c:\windows\SysWow64\mshta.exe
2012-10-31 12:47 . 2012-10-31 12:47114176----a-w-c:\windows\system32\admparse.dll
2012-10-31 12:47 . 2012-10-31 12:47111616----a-w-c:\windows\system32\iesysprep.dll
2012-10-31 12:47 . 2012-10-31 12:47110592----a-w-c:\windows\SysWow64\IEAdvpack.dll
2012-10-31 12:47 . 2012-10-31 12:4710752----a-w-c:\windows\system32\msfeedssync.exe
2012-10-31 12:47 . 2012-10-31 12:47103936----a-w-c:\windows\system32\inseng.dll
2012-10-31 12:47 . 2012-10-31 12:47101888----a-w-c:\windows\SysWow64\admparse.dll
2012-10-30 15:38 . 2012-10-30 15:38254528----a-w-c:\windows\system32\drivers\dtsoftbus01.sys
2012-10-30 14:53 . 2012-10-30 14:5316896----a-w-c:\windows\AsTaskSched.dll
2012-10-29 09:05 . 2012-10-30 14:5753248----a-w-c:\windows\SysWow64\CSVer.dll
2012-10-02 22:21 . 2012-10-30 15:1860776----a-w-c:\windows\system32\OpenCL.dll
2012-10-02 22:21 . 2012-10-30 15:1852584----a-w-c:\windows\SysWow64\OpenCL.dll
2012-10-02 22:21 . 2012-10-30 15:18973672----a-w-c:\windows\system32\nvumdshimx.dll
2012-10-02 22:21 . 2012-10-30 15:189146728----a-w-c:\windows\system32\nvcuda.dll
2012-10-02 22:21 . 2012-10-30 15:18831848----a-w-c:\windows\SysWow64\nvumdshim.dll
2012-10-02 22:21 . 2012-10-30 15:187697768----a-w-c:\windows\SysWow64\nvcuda.dll
2012-10-02 22:21 . 2012-10-30 15:187414632----a-w-c:\windows\system32\nvopencl.dll
2012-10-02 22:21 . 2012-10-30 15:186127464----a-w-c:\windows\SysWow64\nvopencl.dll
2012-10-02 22:21 . 2012-10-30 15:18364904----a-w-c:\windows\system32\nvEncodeAPI64.dll
2012-10-02 22:21 . 2012-10-30 15:18313704----a-w-c:\windows\SysWow64\nvEncodeAPI.dll
2012-10-02 22:21 . 2012-10-30 15:182747240----a-w-c:\windows\system32\nvcuvid.dll
2012-10-02 22:21 . 2012-10-30 15:182731880----a-w-c:\windows\system32\nvapi64.dll
2012-10-02 22:21 . 2012-10-30 15:1826331496----a-w-c:\windows\system32\nvoglv64.dll
2012-10-02 22:21 . 2012-10-30 15:182574696----a-w-c:\windows\SysWow64\nvcuvid.dll
2012-10-02 22:21 . 2012-10-30 15:1825256296----a-w-c:\windows\system32\nvcompiler.dll
2012-10-02 22:21 . 2012-10-30 15:18247144----a-w-c:\windows\system32\nvinitx.dll
2012-10-02 22:21 . 2012-10-30 15:182428776----a-w-c:\windows\SysWow64\nvapi.dll
2012-10-02 22:21 . 2012-10-30 15:182218344----a-w-c:\windows\system32\nvcuvenc.dll
2012-10-02 22:21 . 2012-10-30 15:18202600----a-w-c:\windows\SysWow64\nvinit.dll
2012-10-02 22:21 . 2012-10-30 15:1819906920----a-w-c:\windows\SysWow64\nvoglv32.dll
2012-10-02 22:21 . 2012-10-30 15:181867112----a-w-c:\windows\SysWow64\nvcuvenc.dll
2012-10-02 22:21 . 2012-10-30 15:1818252136----a-w-c:\windows\system32\nvd3dumx.dll
2012-10-02 22:21 . 2012-10-30 15:181760104----a-w-c:\windows\system32\nvdispco64.dll
2012-10-02 22:21 . 2012-10-30 15:1817559912----a-w-c:\windows\SysWow64\nvcompiler.dll
2012-10-02 22:21 . 2012-10-30 15:1815309160----a-w-c:\windows\SysWow64\nvd3dum.dll
2012-10-02 22:21 . 2012-10-30 15:1814922600----a-w-c:\windows\system32\nvwgf2umx.dll
2012-10-02 22:21 . 2012-10-30 15:181482600----a-w-c:\windows\system32\nvdispgenco64.dll
2012-10-02 22:21 . 2012-10-30 15:1813443944----a-w-c:\windows\system32\drivers\nvlddmkm.sys
2012-10-02 22:21 . 2012-10-30 15:1812501352----a-w-c:\windows\SysWow64\nvwgf2um.dll
2012-10-02 19:51 . 2012-10-31 15:283536817----a-w-c:\windows\system32\nvcoproc.bin
2012-10-02 19:51 . 2012-10-31 15:283293544----a-w-c:\windows\system32\nvsvc64.dll
2012-10-02 19:51 . 2012-10-31 15:286200680----a-w-c:\windows\system32\nvcpl.dll
2012-10-02 19:50 . 2012-10-31 15:28891240----a-w-c:\windows\system32\nvvsvc.exe
2012-10-02 19:50 . 2012-10-31 15:2863336----a-w-c:\windows\system32\nvshext.dll
2012-10-02 19:50 . 2012-10-31 15:282557800----a-w-c:\windows\system32\nvsvcr.dll
2012-10-02 19:50 . 2012-10-31 15:28118120----a-w-c:\windows\system32\nvmctray.dll
2012-10-02 13:15 . 2012-10-02 13:15430952----a-w-c:\windows\SysWow64\nvStreaming.exe
2012-09-14 19:19 . 2012-10-31 11:202048----a-w-c:\windows\system32\tzres.dll
2012-09-14 18:28 . 2012-10-31 11:202048----a-w-c:\windows\SysWow64\tzres.dll
.
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
.
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"DAEMON Tools Pro Agent"="c:\program files (x86)\DAEMON Tools Pro\DTAgent.exe" [2011-03-18 839488]
"Sidebar"="c:\program files\Windows Sidebar\sidebar.exe" [2010-11-20 1475584]
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
"USB3MON"="c:\program files (x86)\Intel\Intel(R) USB 3.0 eXtensible Host Controller Driver\Application\iusb3mon.exe" [2012-03-26 291608]
"Adobe Reader Speed Launcher"="c:\program files (x86)\Adobe\Reader 10.0\Reader\Reader_sl.exe" [2012-07-27 35768]
"Adobe ARM"="c:\program files (x86)\Common Files\Adobe\ARM\1.0\AdobeARM.exe" [2012-07-27 919008]
"SunJavaUpdateSched"="c:\program files (x86)\Common Files\Java\Java Update\jusched.exe" [2012-07-03 252848]
"Adobe"="c:\programdata\Adobe\56CF60.vbe" [2012-10-02 7147]
"AVP"="c:\program files (x86)\Kaspersky Lab\Kaspersky Anti-Virus 2011\avp.exe" [2012-12-10 365336]
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\policies\system]
"ConsentPromptBehaviorAdmin"= 5 (0x5)
"ConsentPromptBehaviorUser"= 3 (0x3)
"EnableUIADesktopToggle"= 0 (0x0)
.
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\policies\explorer]
"HideSCAHealth"= 1 (0x1)
.
[HKEY_LOCAL_MACHINE\software\microsoft\security center\Monitoring\KasperskyAntiVirus]
"DisableMonitoring"=dword:00000001
.
R3 RdpVideoMiniport;Remote Desktop Video Miniport Driver;c:\windows\system32\drivers\rdpvideominiport.sys [2010-11-20 20992]
R3 Synth3dVsc;Synth3dVsc;c:\windows\system32\drivers\synth3dvsc.sys [x]
R3 TsUsbFlt;TsUsbFlt;c:\windows\system32\drivers\tsusbflt.sys [2010-11-20 59392]
R3 tsusbhub;tsusbhub;c:\windows\system32\drivers\tsusbhub.sys [x]
R3 VGPU;VGPU;c:\windows\system32\drivers\rdvgkmd.sys [x]
R3 WatAdminSvc;Windows Activation Technologies Service;c:\windows\system32\Wat\WatAdminSvc.exe [2012-10-31 1255736]
S0 iusb3hcs;Intel(R) USB 3.0 Host Controller Switch Driver;c:\windows\system32\DRIVERS\iusb3hcs.sys [2012-03-26 19224]
S1 dtsoftbus01;DAEMON Tools Virtual Bus Driver;c:\windows\system32\DRIVERS\dtsoftbus01.sys [2012-10-30 254528]
S1 kl2;kl2;c:\windows\system32\DRIVERS\kl2.sys [2010-06-09 11864]
S1 KLIM6;Kaspersky Anti-Virus NDIS 6 Filter;c:\windows\system32\DRIVERS\klim6.sys [2010-04-22 27736]
S2 cpuz135;cpuz135;c:\windows\system32\drivers\cpuz135_x64.sys [2012-03-09 23816]
S2 DTSAudioSvc;DTSAudioSvc;c:\program files\Realtek\Audio\HDA\DTSU2PAuSrv64.exe [2012-01-23 233328]
S2 Intel(R) PROSet Monitoring Service;Intel(R) PROSet Monitoring Service;c:\windows\system32\IProsetMonitor.exe [2011-11-09 189608]
S2 Stereo Service;NVIDIA Stereoscopic 3D Driver Service;c:\program files (x86)\NVIDIA Corporation\3D Vision\nvSCPAPISvr.exe [2012-10-02 382824]
S3 ALSysIO;ALSysIO;c:\users\Jonathan\AppData\Local\Temp\ALSysIO64.sys [x]
S3 iusb3hub;Intel(R) USB 3.0 Hub Driver;c:\windows\system32\DRIVERS\iusb3hub.sys [2012-03-26 356632]
S3 iusb3xhc;Intel(R) USB 3.0 eXtensible Host Controller Driver;c:\windows\system32\DRIVERS\iusb3xhc.sys [2012-03-26 789272]
S3 klmouflt;Kaspersky Lab KLMOUFLT;c:\windows\system32\DRIVERS\klmouflt.sys [2009-11-02 22544]
.
.
Contents of the 'Scheduled Tasks' folder
.
2012-12-10 c:\windows\Tasks\GoogleUpdateTaskMachineCore.job
- c:\program files (x86)\Google\Update\GoogleUpdate.exe [2012-10-30 15:01]
.
2012-12-09 c:\windows\Tasks\GoogleUpdateTaskMachineUA.job
- c:\program files (x86)\Google\Update\GoogleUpdate.exe [2012-10-30 15:01]
.
.
--------- X64 Entries -----------
.
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"RTHDVCPL"="c:\program files\Realtek\Audio\HDA\RtkNGUI64.exe" [2012-05-15 6470760]
"RtHDVBg_DTS"="c:\program files\Realtek\Audio\HDA\RAVBg64.exe" [2012-05-11 1175656]
.
------- Supplementary Scan -------
.
uLocal Page = c:\windows\system32\blank.htm
mLocal Page = c:\windows\SysWOW64\blank.htm
TCP: DhcpNameServer = 192.168.1.254 192.168.1.254
.
.
--------------------- LOCKED REGISTRY KEYS ---------------------
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{19114156-8E9A-4D4E-9EE9-17A0E48D3BBB}]
@Denied: (A 2) (Everyone)
@="FlashBroker"
"LocalizedString"="@c:\\Windows\\system32\\Macromed\\Flash\\FlashUtil10d.exe,-101"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{19114156-8E9A-4D4E-9EE9-17A0E48D3BBB}\Elevation]
"Enabled"=dword:00000001
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{19114156-8E9A-4D4E-9EE9-17A0E48D3BBB}\LocalServer32]
@="c:\\Windows\\SysWow64\\Macromed\\Flash\\FlashUtil10d.exe"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{19114156-8E9A-4D4E-9EE9-17A0E48D3BBB}\TypeLib]
@="{FAB3E735-69C7-453B-A446-B6823C6DF1C9}"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB6E-AE6D-11cf-96B8-444553540000}]
@Denied: (A 2) (Everyone)
@="Shockwave Flash Object"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB6E-AE6D-11cf-96B8-444553540000}\InprocServer32]
@="c:\\Windows\\SysWow64\\Macromed\\Flash\\Flash10d.ocx"
"ThreadingModel"="Apartment"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB6E-AE6D-11cf-96B8-444553540000}\MiscStatus]
@="0"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB6E-AE6D-11cf-96B8-444553540000}\ProgID]
@="ShockwaveFlash.ShockwaveFlash.10"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB6E-AE6D-11cf-96B8-444553540000}\ToolboxBitmap32]
@="c:\\Windows\\SysWow64\\Macromed\\Flash\\Flash10d.ocx, 1"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB6E-AE6D-11cf-96B8-444553540000}\TypeLib]
@="{D27CDB6B-AE6D-11cf-96B8-444553540000}"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB6E-AE6D-11cf-96B8-444553540000}\Version]
@="1.0"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB6E-AE6D-11cf-96B8-444553540000}\VersionIndependentProgID]
@="ShockwaveFlash.ShockwaveFlash"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB70-AE6D-11cf-96B8-444553540000}]
@Denied: (A 2) (Everyone)
@="Macromedia Flash Factory Object"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB70-AE6D-11cf-96B8-444553540000}\InprocServer32]
@="c:\\Windows\\SysWow64\\Macromed\\Flash\\Flash10d.ocx"
"ThreadingModel"="Apartment"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB70-AE6D-11cf-96B8-444553540000}\ProgID]
@="FlashFactory.FlashFactory.1"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB70-AE6D-11cf-96B8-444553540000}\ToolboxBitmap32]
@="c:\\Windows\\SysWow64\\Macromed\\Flash\\Flash10d.ocx, 1"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB70-AE6D-11cf-96B8-444553540000}\TypeLib]
@="{D27CDB6B-AE6D-11cf-96B8-444553540000}"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB70-AE6D-11cf-96B8-444553540000}\Version]
@="1.0"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\CLSID\{D27CDB70-AE6D-11cf-96B8-444553540000}\VersionIndependentProgID]
@="FlashFactory.FlashFactory"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\Interface\{1D4C8A81-B7AC-460A-8C23-98713C41D6B3}]
@Denied: (A 2) (Everyone)
@="IFlashBroker3"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\Interface\{1D4C8A81-B7AC-460A-8C23-98713C41D6B3}\ProxyStubClsid32]
@="{00020424-0000-0000-C000-000000000046}"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Wow6432Node\Interface\{1D4C8A81-B7AC-460A-8C23-98713C41D6B3}\TypeLib]
@="{FAB3E735-69C7-453B-A446-B6823C6DF1C9}"
"Version"="1.0"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\VideoLAN.VLCPlugin.*1*]
@="?????????????????? v1"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\VideoLAN.VLCPlugin.*1*\CLSID]
@="{E23FE9C6-778E-49D4-B537-38FCDE4887D8}"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\VideoLAN.VLCPlugin.*2*]
@="?????????????????? v2"
.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\VideoLAN.VLCPlugin.*2*\CLSID]
@="{9BE31822-FDAD-461B-AD51-BE1D1C159921}"
.
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\PCW\Security]
@Denied: (Full) (Everyone)
.
Completion time: 2012-12-10 11:03:53
ComboFix-quarantined-files.txt 2012-12-10 11:03
ComboFix2.txt 2012-12-10 10:53
.
Pre-Run: 227,437,318,144 bytes free
Post-Run: 227,354,509,312 bytes free
.
- - End Of File - - 023B152F55C8A6264C094CB2FF461C3B
Malwarebytes Anti-Malware 1.65.1.1000
www.malwarebytes.org
Database version: v2012.12.10.01
Windows 7 Service Pack 1 x64 NTFS
Internet Explorer 9.0.8112.16421
Jonathan :: JONATHAN-PC [administrator]
10/12/2012 02:08:13
mbam-log-2012-12-10 (02-08-13).txt
Scan type: Quick scan
Scan options enabled: Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken | PUP | PUM
Scan options disabled: P2P
Objects scanned: 221663
Time elapsed: 1 minute(s), 15 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 0
(No malicious items detected)
Registry Values Detected: 1
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run|win32 (Trojan.StartPage) -> Data: "C:\kernels\drivers.vbs" -> Quarantined and deleted successfully.
Registry Data Items Detected: 0
(No malicious items detected)
Folders Detected: 0
(No malicious items detected)
Files Detected: 3
C:\win32.exe (Trojan.Agent) -> Quarantined and deleted successfully.
C:\Users\Jonathan\AppData\Local\Temp\svchost.exe (Trojan.Agent.Gen) -> Quarantined and deleted successfully.
C:\Kernels\drivers.vbs (Trojan.StartPage) -> Quarantined and deleted successfully.
(end)