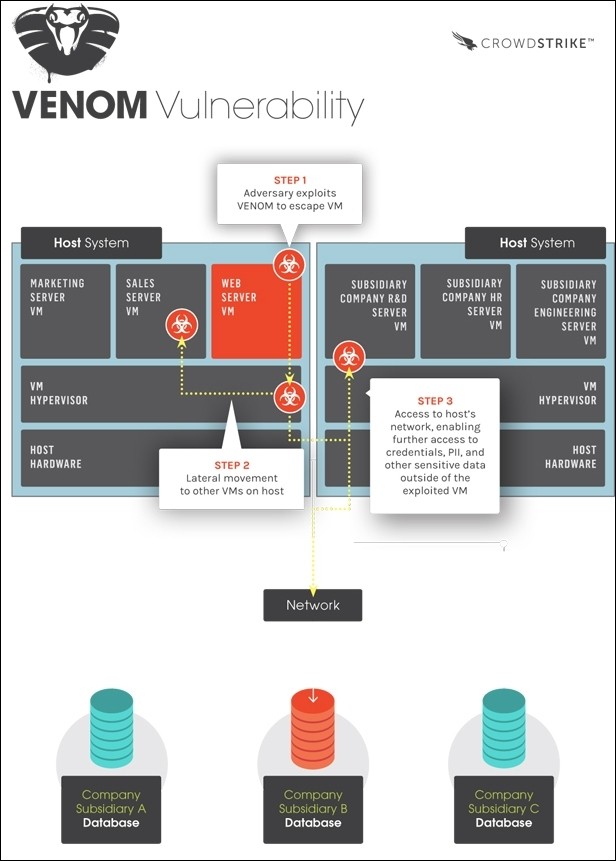
Researchers have uncovered a new bug that's much more dangerous than last year's Heartbleed vulnerability. Venom, short for Virtualized Environment Neglected Operations Manipulation, could allow an attacker to infiltrate a datacenter and take over its entire network.
As ZDNet notes, most datacenters use virtual machines to segregate customers, allowing the admins to run multiple instances on a single server. The virtual machines all share resources but operate as separate entities in the host hypervisor, which is responsible for powering the virtual machines.
Venom allows a bad actor to escape their own virtual machine and access others on the network.
Discovered by Jason Geffner from security firm CrowdStrike, the zero-day vulnerability dates back to 2004 and is caused by a legacy floppy disk controller that, when sent a specific string of code, can crash the hypervisor.
A number of modern virtualization platforms such as KVM, VirtualBox and Ken are all vulnerable. Datacenters running Bochs hypervisors, Microsoft Hyper-V and VMware are safe. Geffner told the publication in a phone interview that millions of virtual machines are using one of the vulnerable platforms.
How bad is it compared to Heartbleed?
The security researcher said Heartbleed lets a hacker look through a window of a house and gather information based on what they see. Continuing the analogy, he added that Venom allows a bad actor to break into a house then subsequently do the same to every other house in the neighborhood.
Dan Kaminsky, a well-known security researcher, said the bug went unnoticed for so long simply because hardly anyone bothered to look at the legacy disk drive system.
The good news is that because the flaw was found in-house at CrowdStrike, there's no publicly known code to exploit it which will give companies some lead time in resolving the bug and issuing patches.
