TL;DR: A Russian modular botnet called Cyclops Blink is hijacking Asus routers worldwide, reportedly in an attempt to build an army of compromised routers for use in cyberwarfare. The hackers want to use the vulnerable devices as command-and-control (C&C or C2) servers.

Cyclops Blink is a Kremlin-linked malware that has existed since 2019. It is tied to the elite Sandworm hacking group. According to UK's National Cyber Security Centre (NCSC), it initially targeted WatchGuard Firebox devices. Sandworm was linked to other well-known cyber-attacks, like the NotPetya ransomware, which has caused billions of dollars worth of damage globally since June 2017, and the BlackEnergy malware behind the Ukrainian blackouts of 2015-16.
Researchers with Trend Micro note that Cyclops Blink casts a wide net in terms of the devices it infects, with no specific focus on high-value government or diplomatic entities. Hackers compromised some of the infected equipment more than two and a half years ago.
Cyclops Blink attempts to establish persistence for threat actors on the device, creating a point of remote access to compromised networks. Due to its modular design, it can easily be updated to target new devices. It has recently gained a new module allowing it to attack Asus routers.

Trend Micro notes that the targets do not appear to be of particular value for cyberwarfare.
"It should be noted that these victims do not appear to be evidently valuable targets for either economic, military, or political espionage. For example, some of the live C&Cs are hosted on WatchGuard devices used by a law firm in Europe, a medium-sized company producing medical equipment for dentists in Southern Europe and a plumber in the United States … The purpose of this botnet is still unclear: Whether it is intended to be used for distributed denial-of-service (DDoS) attacks, espionage, or proxy networks remains to be seen. But what is evident is that Cyclops Blink is an advanced piece of malware that focuses on persistence and the ability to survive domain sinkhole attempts and the takedown of its infrastructure."
Researchers believe there is another vendor with compromised firmware, but unfortunately, they cannot identify the vendor yet.
Cyclops Blink uses hard-coded TCP ports to communicate with C&C servers. For every port, it makes a new rule in the Netfilter Linux kernel firewall to allow output communication to it. Once a connection is established, the malware initializes an OpenSSL library, and its core component then executes a set of hard-coded modules. The malware then pushes various parameters to these modules, which return data that the core component encrypts using OpenSSL functions before sending it back to the C2 server.
Trend Micro believes the malware is the successor to the VPNFilter malware from 2018. It, too, was designed to infect routers and networked devices to siphon data and compromise them for future use.
The new Asus module is built to access and replace a router's flash memory. The botnet reads 80 bytes from the flash memory, writes it to the main communication pipe, and then waits for a command with the data needed to replace the content. A second module gathers data from the infected device and sends it to the C2 server. A third module, "file download (0x0f)," downloads files from the internet using DNS over HTTPS (DoH).
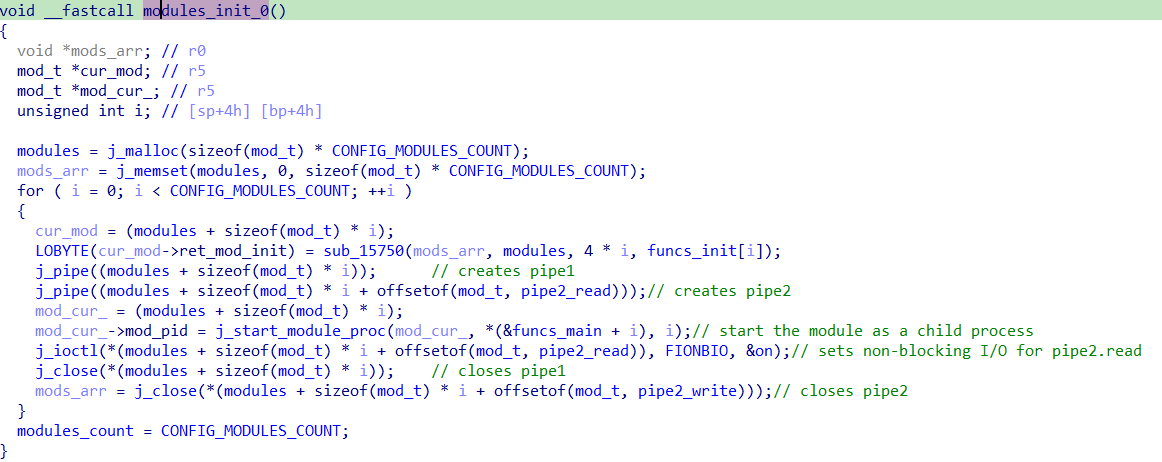
The function that initializes the modules
Affected Asus model numbers and their firmware details are as follows:
- GT-AC5300
- GT-AC2900
- RT-AC5300
- RT-AC88U
- RT-AC3100
- RT-AC86U
- RT-AC68U
- AC68R
- AC68W
- AC68P
- RT-AC66U_B1
- RT-AC3200
- RT-AC2900
- RT-AC1900P
- RT-AC1900P
- RT-AC87U (EOL)
- RT-AC66U (EOL)
- RT-AC56U (EOL)
As of publication, Asus has not released new firmware updates but has released the following mitigation instructions:
- Reset the device to factory default: Login into the web GUI, go to Administration → Restore/Save/Upload Setting, click the "Initialize all the setting and clear all the data log," and then click Restore button."
- Update to the latest available firmware.
- Ensure the default admin password has been changed to a more secure one.
- Disable Remote Management (disabled by default, can only be enabled via Advanced Settings).
The three models designated as EOL (end of life) are no longer supported and won't receive any firmware security updates. Asus recommends buying a new one.
The related security advisory for WatchGuard network devices can be found on WatchGuard's website.
Image credit: Julie Mineeva
