In context: For all the conveniences they provide, keyless entry systems in cars have been subjected to relay attacks for several years, requiring carmakers to beef up security measures against such hacks that generally require a few hundred dollars of equipment to execute. A new key-cloning technique developed by security researchers from KU Leuven, Belgium, and the University of Birmingham, UK, makes use of vulnerabilities in DST80, a Texas Instruments encryption system found in car immobilizers used by several major manufacturers, potentially enabling hackers to drive away with the vehicle.

With security being a perpetual leapfrog of finding loopholes and patching systems across several industries, it's not surprising to see modern tech-laden cars being subject to the same process. A new discovery, however, might be a pickle to fix for Toyota, Hyundai, and Kia, companies whose decade-old and more recent models have been found vulnerable to a key-clone attack.
Although the final objective is the same, the cloning technique differs from a relay attack in the way that it requires a hacker to swipe an inexpensive Proxmark RFID reader/transmitter device with a key fob that's using DST80 inside, reports Wired.
The two-step process involves extracting the secret cryptographic value of the key fob through the exploit, which impersonates the RFID device as the key inside the car and allows for disabling the immobilizer. As the hack only affects the immobilizer and not the keyless entry system, the hacker still needs to start the engine by turning the ignition barrel.
That's where the second step of hot-wiring comes in, which the researchers say can also be done with a well-placed screwdriver in the ignition barrel, techniques used by car thieves before the immobilizer came in. "You're downgrading the security to what it was in the '80s," notes computer science professor, Flavio Garcia, from the University of Birmingham.
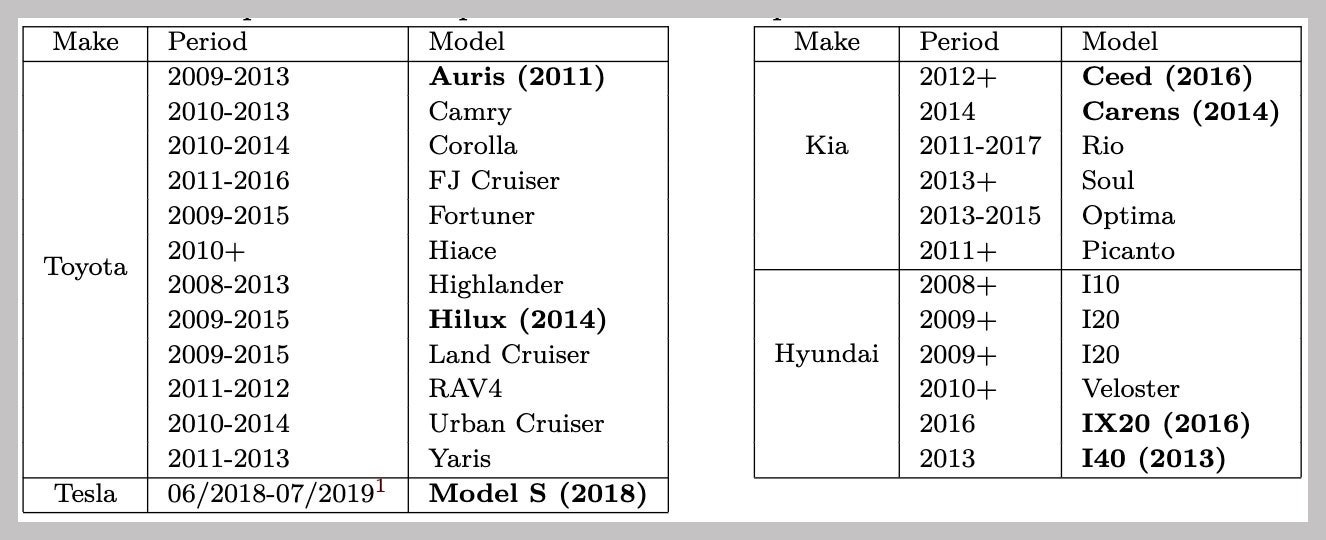
Out of all the affected cars, only Tesla issued a software fix for its Model S.
Popular cars like the Toyota Camry, Corolla and RAV4 are vulnerable to this hack, along with several models from Kia and Hyundai appear on the list. The issue also affected the 2018 Model S, which the researchers say was patched by Tesla through an OTA update last year when the DST80 vulnerability was reported to the company.
It's worth noting here that the flaw doesn't lie with DST80 itself but in how carmakers chose to implement the system. Toyota, which acknowledged this vulnerability, had fobs transmitting cryptographic keys based on the cars' serial number, while Hyundai and Kia made guessing the key easier (and quicker) by using 24 bits of randomness instead of 80 bits offered by DST80. The researchers were able to retrieve this information by getting a collection of immobilizer ECUs from eBay and reverse-engineered their firmware to analyze how they communicated with the key fobs.
"The described vulnerability applies to older models, as current models have a different configuration," said Toyota, in a statement to Wired, adding that "this vulnerability constitutes a low risk for customers, as the methodology requires both access to the physical key and to a highly specialized device that is not commonly available on the market." to which the researchers disagreed, while Hyundai noted that none of its affected models are sold in the US and reminded customers "to be diligent with who has access to their vehicle’s key fob."
Affected cars list courtesy of University of Birmingham and KU Leuven