Why it matters: As ransomware remains a prevalent security threat, an essential step in countering attackers is identifying their methods. Security researchers found that several of the most prolific groups share a significant proportion of their tactics, potentially making them more predictable.

A new report from security company Kaspersky reveals that eight of the most active ransomware gangs operate with very similar patterns. Analysis, digital forensics specialists, and other security workers could use these similarities to identify and fight these attackers more efficiently.
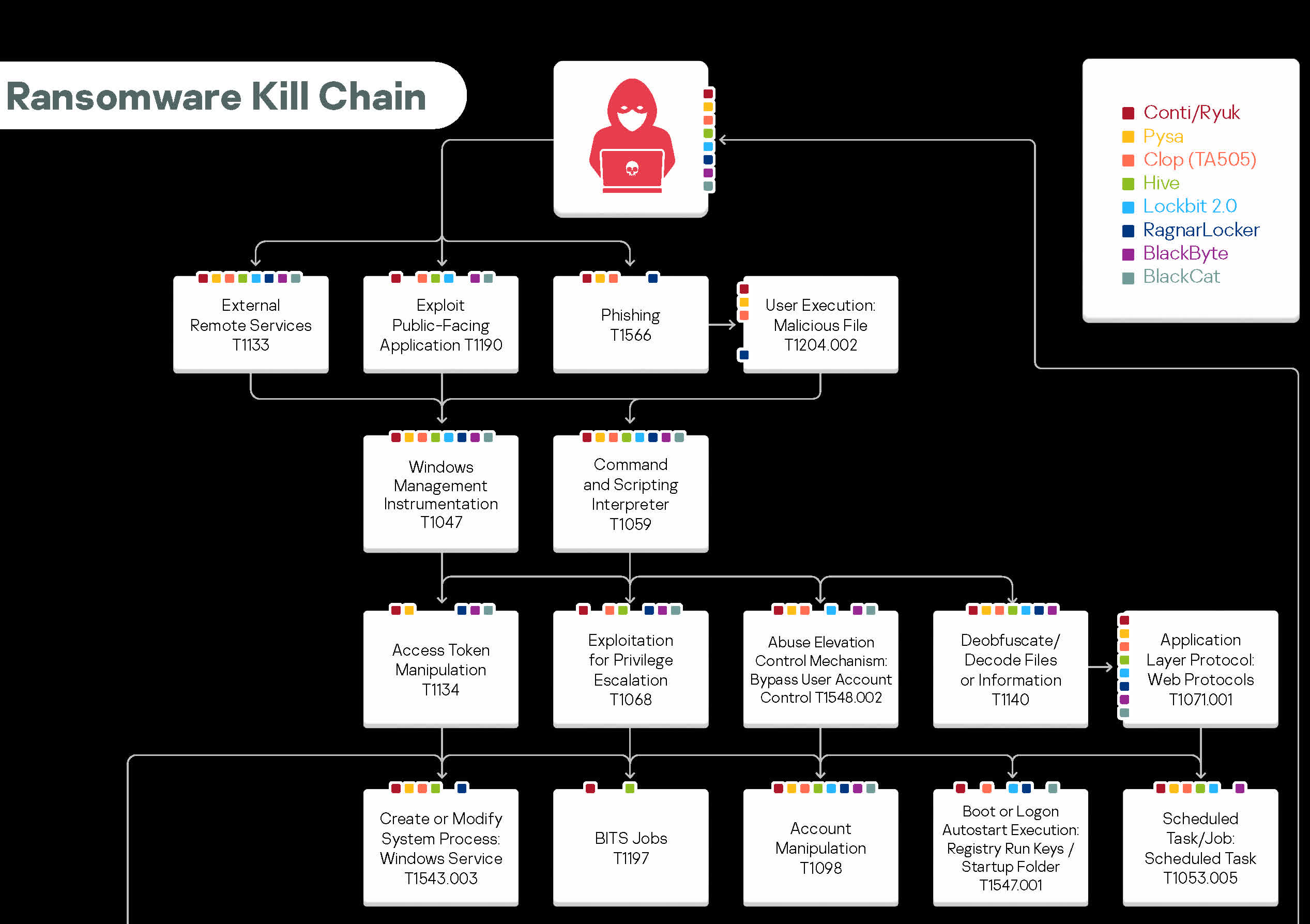
The report analyzes the tactics, techniques, and procedures of (TTP) of the ransomware groups Conti/Ryuk, Pysa, Clop (TA505), Hive, Lockbit 2.0, RagnarLocker, BlackByte, and BlackCat. VentureBeat notes that these eight gangs have attacked over 500 organizations in various industries in the US, the UK, and Germany in the last year. Kaspersky built an interesting chart listing dozens of steps in ransomware attacks and indicating which attackers undergo each step. None of them are unique to one group.
 Click on the image to view the full-size chart
Click on the image to view the full-size chart
For instance, all the groups like to start by attacking external remote services, while only half also open with phishing. All the gangs tend to favor targets like Windows Management Instrumentation, command and scripting interpreters, application layer protocols, web protocols, signed binary execution, and others.
Common steps like preventing system recovery or encrypting the most impactful data seem obvious. However, some of the least prevalent tactics involve BITS jobs, lifting account credentials from password stores, or getting them from web browsers.
Early in June, a Foxconn facility in Mexico suffered an attack from Lockbit 2.0. Other recent ransomware victims include QNAP, Asustor, and Nvidia.