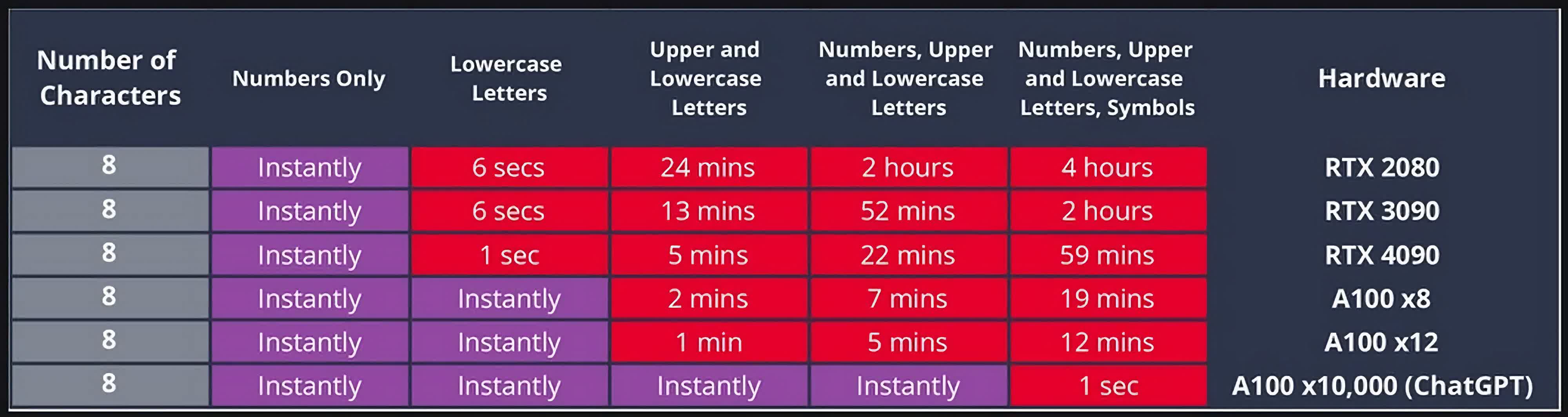
The big picture: People are often advised to create complex passwords using random lower and uppercase letters, symbols, and numbers to prevent brute-force attacks. However, a new report suggests that Nvidia's latest GPUs, like the RTX 4090 and the A100, can crack even the most complex of passwords within minutes.

According to Hive Systems, hackers are finding it increasingly difficult to crack passwords, thanks to the widespread use of stronger hashing algorithms like bcrypt, which is replacing MD5 as the hashing technology of choice for most websites and online services. But as hardware gets more powerful, cracking simple passwords is becoming quicker and easier with every passing year.
As per the 2024 edition of the Hive Systems Password Table, an 8-character password can be cracked by an array of 12 RTX 4090 GPUs in just 37 seconds if it includes only numbers with no letters or symbols. However, the time rises to an impressive 7 years if the password uses the recommended mix of numbers, upper and lowercase letters, and symbols, making it much more difficult to crack using brute force.
Hive also tested the password-cracking ability of 10,000 A100 GPUs - the same hardware that runs ChatGPT. According to the data, the state-of-the-art hardware can theoretically crack randomly generated 8-character bcrypt password hashes in just 5 days. While it won't be practical for the vast majority of cybercrime syndicates to use this sort of hardware, it does give us an idea about what hackers can do if granted an unlimited budget.
The numbers are significantly lower for passwords protected by MD5 hashes. In this case, just a single RTX 4090 can crack a complex 8-character password with numbers, lower- and uppercase letters, and symbols, in just 59 minutes. That's a significant step-up from the RTX 3090, which would take 2 hours to crack the same password. The study echoes the findings of security researcher Sam Croley, whose data from 2022 seemed to show that the new gaming flagship is more than 2x faster than the RTX 3090 in cracking passwords.
Hive used a hashing software called Hashcat to measure the time required to crack the passwords. Do note that the study does not take into account the use of Multi-factor authentication (MFA), which is becoming more common with every passing day. Most cybersecurity professionals advise people to use MFA on all their online accounts to add a second layer of protection.
Nvidia RTX 4090 can crack complex 8-character passwords in minutes