In a nutshell: Ransomware remains a scourge, but there is some good news: the average payment amount made by victims fell in Q4 after spending more than a year rising drastically. The reason? Fewer companies are giving in to ransom demands.

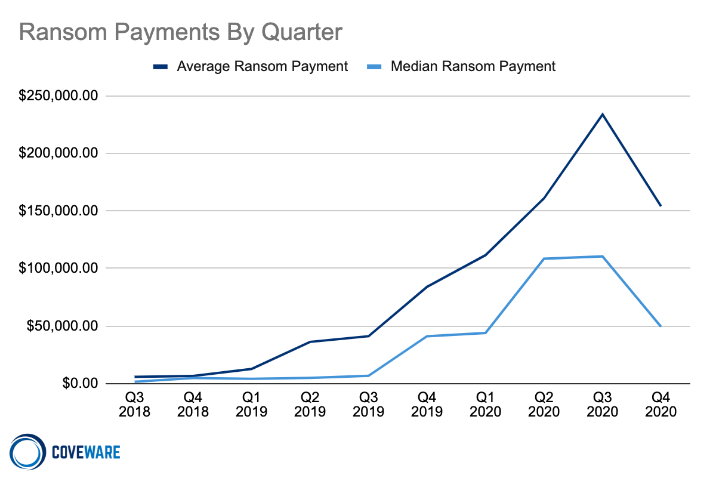
Cybersecurity firm Coveware’s latest quarterly ransomware report shows that after continuously rising since Q3 2018, average ransomware payments fell 34 percent in the fourth quarter of last year to $154,108. Median ransomware payments, meanwhile, were down 55 percent to $49,450.
Generally, anyone who suffers a ransomware attack is advised not to hand over any crypto as it’s no guarantee perpetrators will hand over the encryption key. It seems more companies are heeding this advice.
Another reason behind the fall relates to ransomware attacks in which criminals threaten to release sensitive information if their demands aren’t met. Coveware writes that these made up 70 percent of all ransomware attacks in Q4, up from 50 percent during the previous quarter. It’s common for the data to be leaked online even when ransoms are paid, so fewer victims are giving in to the extortion.
In cases involving stolen data, just sixty percent of the companies agreed to pay in Q4, that’s down from 75 percent in Q3.
“Coveware continues to witness signs that stolen data is not deleted or purged after payment. Moreover, we are seeing groups take measures to fabricate data exfiltration in cases where it did not occur,” states the report.
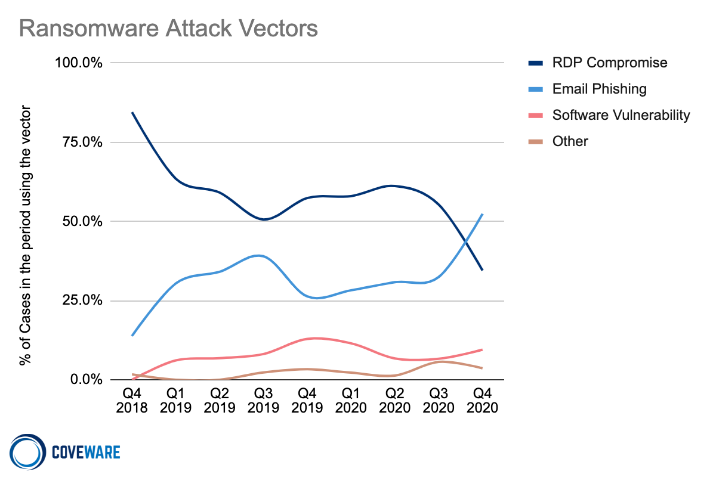
Looking at ransomware attack vectors, email phishing has now surpassed Remote Desktop Protocol (RDP) compromises as the most popular, being behind more than 50 percent of all incidents in the fourth quarter. RDPs, which exploit leaked credentials, remain popular as employee usernames and passwords sell for as low as $50.
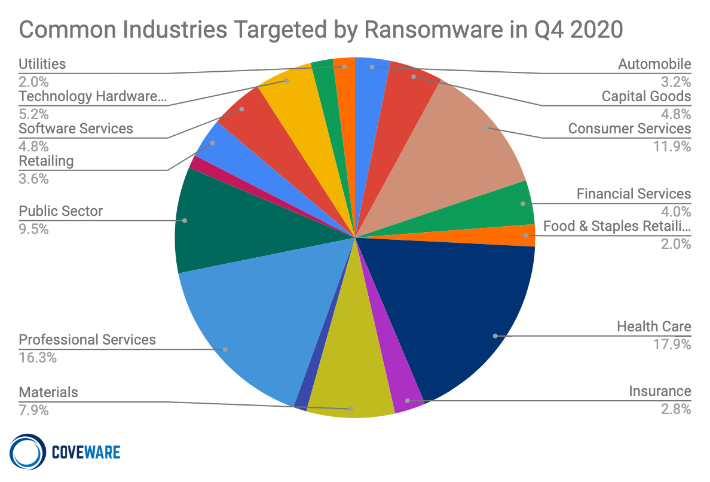
Professional services was the second-most-common industry targeted by ransomware criminals (16.3 pecent), sitting behind health care (17.9 percent). Hospitals and health centers have long been a common target—criminals assume they are more willing to pay up. With the pandemic already pushing these organizations to breaking point, ransomware attacks could potentially cost lives.
Masthead credit: Andrey_Popov
https://www.techspot.com/news/88490-ransomware-payments-falling-more-victims-refuse-pay.html