In brief: Ransomware-type malware threats encrypt files and then ask the victims to pay cryptocurrency if they want to get their data back. In 2022, however, the market started to change as fewer and fewer companies chose to be blackmailed.

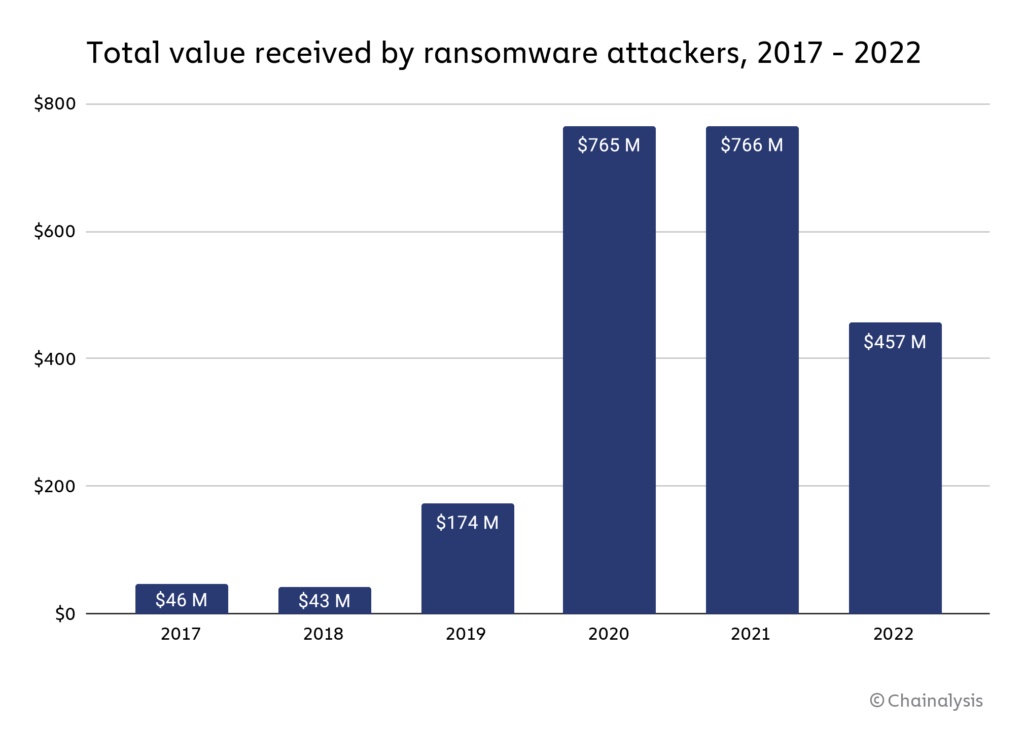
According to data provided by blockchain analysis firm Chainalysis, ransomware revenues for 2022 have shrunk from $765.6 million to at least $456.8 million, or a -40.3% drop year-over-year. The volume of attacks is as impressive as ever, but the number of victims that refuse to pay the ransom has grown as well.
Working with Coveware, Chainalysis has seen a sharp reduction in the number of ransomware victims willing to pay: they were 76% in 2019 but just 41% in 2022. It's a "highly encouraging" trend, Chainalysis says, likely influenced by different reasons.
Ransomware victims have realized that even if they pay the ransom, there's no guarantee they will get their data back or that the ransomware actor will delete the "stolen" files without selling them to third parties on the dark web. The public perception of the ransomware phenomenon has matured as well, so data leaks don't carry the same risks for brand reputation of the last few years.
Companies and public organizations, which are the main targets of modern ransomware operations, have developed better backup strategies as well, so that data recovery is a much cleaner and easier affair than it was just a couple of years ago.
Insurance companies are also much less likely to allow their clients to use an insurance payout to fulfill a ransom request. Finally, as many ransomware operations are based in Russia, victims who decide to pay could face the harsh legal consequences brought by the economic sanctions against the country after the invasion of Ukraine.
Even though the victims are not paying as much as before, the ransomware business is anything but dead: in 2022, the average lifespan of file encrypting-malware strains has dropped from 153 days to just 70 days year-over-year. The "Conti" ransomware operation came to an end while other ransomware-as-a-service (raas) operations went live, including Royal, Play, and BlackBasta. LockBit, Hive, Cuba, BlackCat, and Ragna were still in business (and still asking for ransom payments) at the end of 2022.
https://www.techspot.com/news/97326-ransomware-victims-finally-refusing-pay-up.html