In brief: Governments around the world increasingly deploy mobile spyware in response to civil strife. Reports from Google and Lookout Threat Lab describe multiple spyware campaigns undertaken through Italian company RCS Labs. In some cases, ISPs helped distribute its "Hermit" spyware, which the company can sideload onto iPhones.

A report from Google's Threat Analysis Team describes how Italian company RCS Labs distributes its Hermit spyware on behalf of clients which include national governments. It aligns with Lookout Threat Lab's report from earlier this month.
Attackers distribute Hermit through SMS links leading to fake web pages impersonating real companies, like a Facebook account recovery page or a support page for Chinese tech company Oppo. The pages might ask users to download apps that deliver the spyware.
However, in some cases, the target's ISP might cooperate with attackers by disabling the target's internet service. The target then receives a message with a link to restore service which installs Hermit.
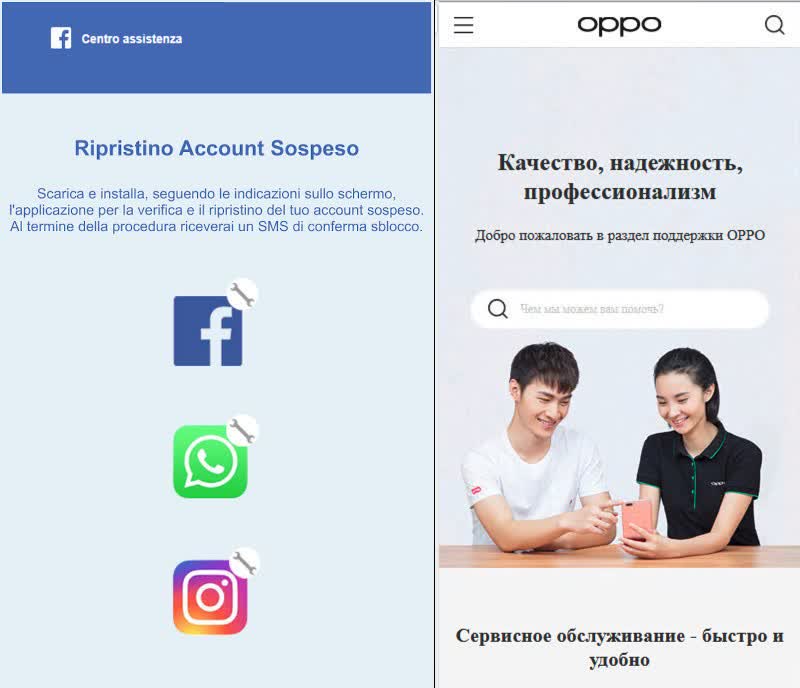
Examples of fake web pages that distributed Hermit spyware
Through drive-by downloads and multiple known exploits, RCS can sideload apps containing Hermit onto iOS devices because the company is part of the Apple Developer Enterprise Program. The apps never appear on the Apple App Store but have legitimate iOS certificates and run within the iOS app sandbox. Similar drive-by downloads are possible on Android if users enable sideloading, and the apps never appear on Google Play.
Google and Lookout detected Hermit's deployment most notably in Kazakhstan. Lookout also noticed it in Kurdish areas of Syria and found RCS has connections to the governments of Vietnam, Myanmar, Pakistan, Chile, Mongolia, Bangladesh, and Turkmenistan.
To avoid spyware, users should keep their mobile devices updated, avoid suspicious or unknown links, be cautious when installing new apps, and occasionally review their apps.
https://www.techspot.com/news/95094-security-researchers-detail-hermit-spyware-android-ios.html