@
Skrekkur oh damn, anything but Eve Online! Intel please don't mess with my favorite MMO and its servers!
for those who want to test their PC and see if it still is vulnerable here's the powershell script and instructions:
- Press the Windows key and type PowerShell.
- Right click the PowerShell shortcut and select Run as Administrator.
- Type Install-Module SpeculationControl and press Enter.
- If you are prompted to install the NuGet provider, type Y and press Enter, and repeat if you are warned about installing from an untrusted repository.
- With the installation complete, type Import-Module SpeculationControl and press Enter.
- Type Get-SpeculationControlSettings and press Enter.
I ran into a Windows PowerShell execution policy issue when doing step 5. If that happens to you then run the following command:
Set-ExecutionPolicy -ExecutionPolicy AllSigned
After you are finished with the test you can set it back to the default one using:
Set-ExecutionPolicy -ExecutionPolicy Restricted
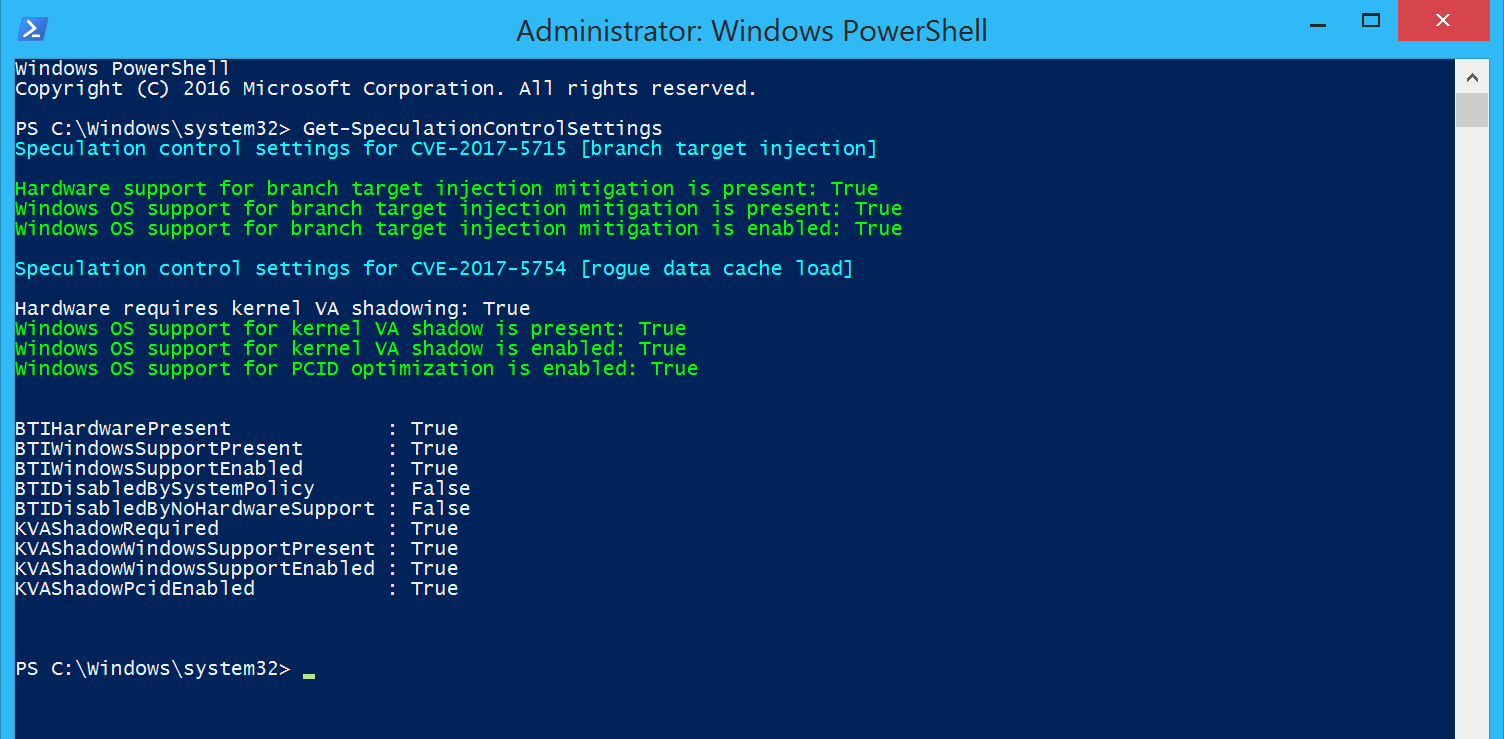
If you have the windows and bios patches the results should look like this:
Speculation control settings for CVE-2017-5715 [branch target injection]
Hardware support for branch target injection mitigation is present: True
Windows OS support for branch target injection mitigation is present: True
Windows OS support for branch target injection mitigation is enabled: True
Speculation control settings for CVE-2017-5754 [rogue data cache load]
Hardware requires kernel VA shadowing: True
Windows OS support for kernel VA shadow is present: True
Windows OS support for kernel VA shadow is enabled: True
Windows OS support for PCID optimization is enabled: True