Why it matters: Even after 18 months, WannaCry still poses a significant threat to businesses worldwide. According to Kryptos Logic, over half a million computers are still infected. The ransomware has been mostly eradicated in the United States and United Kingdom, but remains a widespread problem in other parts of the world.

It has been a year and a half since the initial WannaCry ransomware outbreak, and the malware still poses a threat to thousands of computers. Recent data shows that hundreds of thousands of computers are still infected with the malicious software even though it is currently dormant.
The malware is inactive thanks to security researcher Marcus Hutchins at Kryptos Logic. Bleeping Computer notes that Hutchins found a bit of code in the ransomware that referenced an odd domain. The domain was unregistered, so he registered it only to discover that he had activated a kill switch.
WannaCry periodically pings this address. As long as the sinkholed domain is up and running the software will not encrypt files. If it were to go down, then the malware would kick in and begin causing trouble.
Kryptos Logic gave the domain over to Cloudflare for hosting as a protective measure against DDoS attacks. Cloudflare also gives them access to various metrics of the address. Kryptos Logic’s Head of Security & Threat Intelligence Research Jamie Hankins recently tweeted some of these statistics.
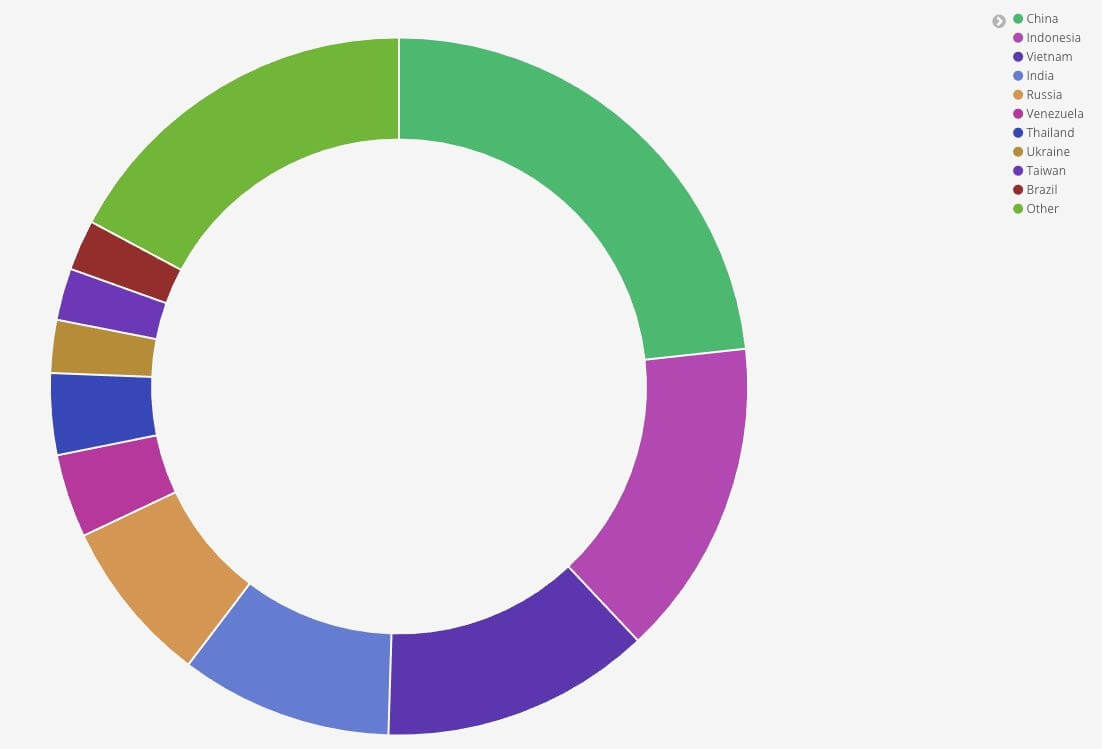
During one week, the kill switch domain received more than 17 million pings. These beacons come from over 630,000 unique IP addresses originating in 194 different countries. China, Indonesia, and Vietnam are the top three countries by way of infections, and nearly half the traffic to the domain is from these regions.
“The UK consists of approximately 0.15% of the total connections with the USA coming in at 1.35% for a single day's statistics,” Hankins told Bleeping Computer. “These numbers can be skewed by DHCP churn over longer time periods.”
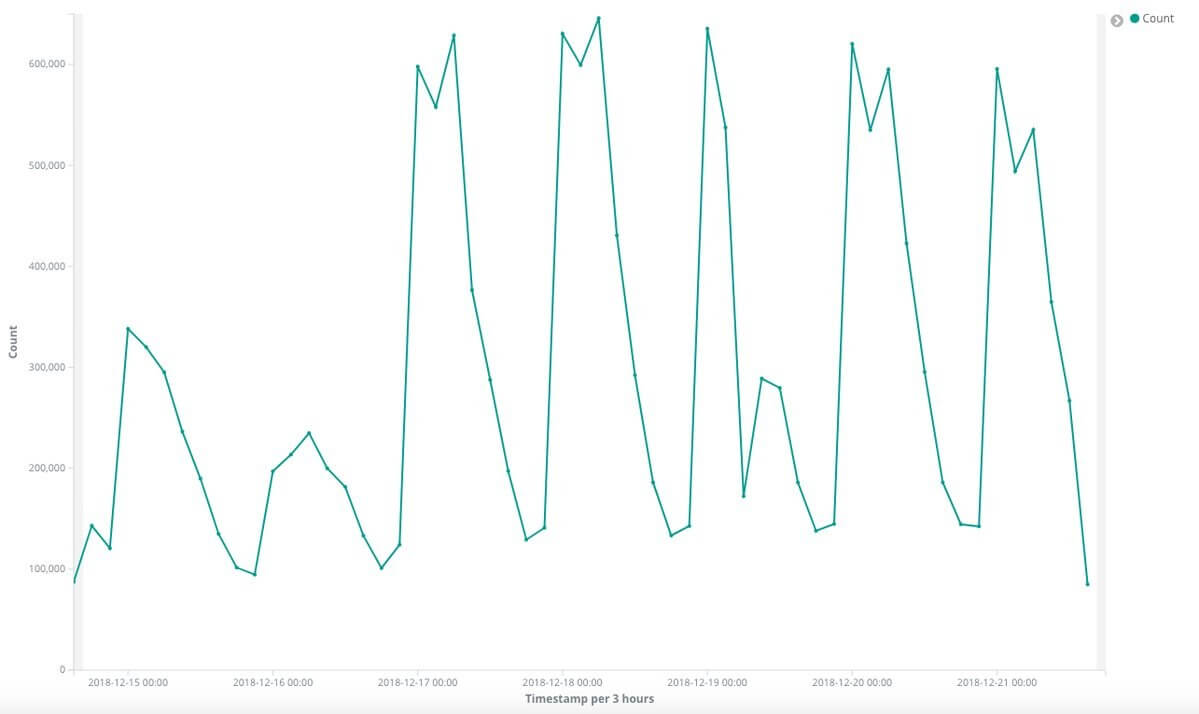
The domain is more active on weekdays than on the weekend. This statistic was expected considering the ransomware’s primary targets would be enterprise computers. Businesses are much more likely to pay a high price for valuable files than private users.
While WannaCry remains dormant for now, Hankins warns that all it would take for the malware to rear its ugly head is an internet outage.
Kryptos Logic has a tool called TellTale, which identifies WannaCry infections. Admins can use it to look up and monitor their range of IP addresses. TellTale can spot other types of malware as well.
https://www.techspot.com/news/78037-wannacry-lies-dormant-thousands-computers.html