Mobile security company Bluebox claims to have discovered a flaw in Android that could leave any device released in the last four years vulnerable to attacks. The method demonstrated allowed modifying an app's code without affecting its cryptographic signature, inserting malicious code completely unnoticed, leading to anything from data theft to creating botnets. The implications are huge, the researchers say.
The vulnerability has reportedly been around since the release of Android 1.6 in 2009 and Google was notified about it in February. But due to the way Android updates work, it's up to manufacturers to produce and release firmware updates for their specific hardware, and so far only the Galaxy S 4 has been patched.
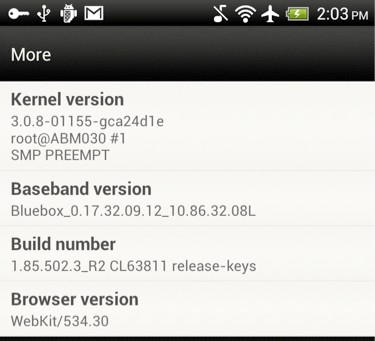
As proof of the vulnerability's existence, Bluebox CTO Jeff Forristal accompanied his blog post with a screenshot from an HTC device that had system-level software information modified to display "Bluebox" in the Baseband Version string (a value normally controlled & configured by the system firmware).
Technical details and related tools will be released at his BlackHat USA 2013 talk by the end of the month.
It's worth noting that for all the doom and gloom that Bluebox is spelling – it appears to be a serious issue after all – falling prey to hackers would require you to download an actual app that has been modified with malicious code. In other words, it requires user action, and most likely downloading from a non-official source.