What really happened with Vista: An insider's retrospective I enjoyed reading Terry Crowley's thoughtful blog (What Really Happened with Vista). Terry worked in the Office organization and did a fantastic job covering the complex machinations that went into Windows Vista and the related but doomed Longhorn project --- from an outsider's point of view. He correctly identified many of the problems that dogged the project and I don't mean to rehash any of them here. Medium
I'm harvesting credit card numbers and passwords from your site. Here's how. It's been a frantic week of security scares --- it seems like every day there's a new vulnerability. It's been a real struggle for me personally to pretend like I understand what's going on when asked about it by family members. Seeing people close to me get all flustered at the prospect of being "powned" has really put things in perspective for me. Hackernoon
Cisco can now sniff out malware inside encrypted traffic Cisco has switched on latent features in its recent routers and switches, plus a cloud service, that together make it possible to detect the fingerprints of malware in encrypted traffic. Switchzilla has not made a dent in transport layer security (TLS) to make this possible. Instead, as we reported in July 2016, Cisco researchers found that malware leaves recognisable traces even in encrypted traffic. The Register
Intel unveils 'breakthrough' quantum computer Quantum computing has been a major research topic for multiple companies the past few years, with D-Wave, IBM, and Intel all launching their own systems and improving them at a fairly rapid clip. At CES 2018 this week, Intel's CEO, Brian Krzanich, declared the company's new 49-qubit quantum computer represented a step towards "quantum supremacy." ExtremeTech
Infected USB sticks handed out at data security event The Criminal Investigation Bureau has admitted that it handed out 54 malware-infested thumb drives to the public at a data security expo hosted by the Presidential Office from Dec. 11 to Dec. 15 last year. The malware-infected USB sticks were among 250 drives that the bureau gave to the winners of a game about cybersecurity knowledge. Taipei
Ultrafine fibers have exceptional strength Researchers at MIT have developed a process that can produce ultrafine fibers --- whose diameter is measured in nanometers, or billionths of a meter --- that are exceptionally strong and tough. These fibers, which should be inexpensive and easy to produce, could be choice materials for many applications, such as protective armor and nanocomposites. MIT
Intel and Micron to discontinue flash memory partnership The long-running partnership between Intel and Micron for the development and manufacturing of NAND flash memory will soon come to an end. The two companies have announced intentions to go their separate ways after introducing their third generation of 3D NAND around the end of 2018 or early 2019. Anandtech
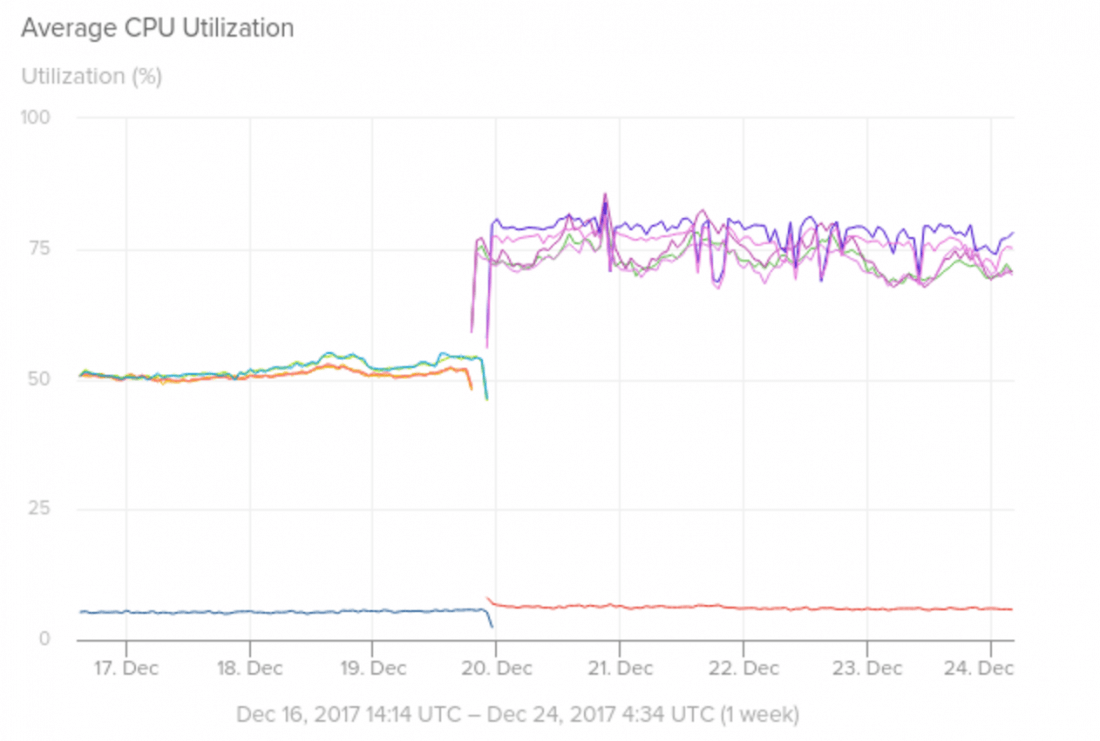
Visualizing Meltdown on AWS One January 3, 2018 the Meltdown and Spectre CPU architecture flaws were announced to the world. This announcement actually came about a week earlier than planned due to early leaks. As the reader has likely read about the bugs in previous forums, we won't go into depth in this article. AppOptics
Why Uber can find you but 911 can't Software on Apple Inc.'s iPhones and Google's Android smartphones help mobile apps like Uber and Facebook to pinpoint a user's location, making it possible to order a car, check in at a local restaurant or receive targeted advertising. But 911, with a far more pressing purpose, is stuck in the past. WSJ
100,000 IoT Sensors Monitor a 1,400-Kilometer Canal in China As an engineering feat, China's massive South-to-North Water Diversion Project is a stunner. Three artificial canals, each more than 1000 kilometers long, are in various stages of completion and designed to reroute water from the country's rainy south to its parched north. IEEE Spectrum
