In a nutshell: Full-time bug bounty hunter Bhavuk Jain discovered a zero-day exploit in Apple's "Sign in with Apple" system that earned him a $100,000 bounty from the Cupertino tech company. The potentially serious zero-day vulnerability could have allowed malicious users to completely take over the accounts of users of third-party websites using the authentication method.
Sign in with Apple is a login method launched last year used to access online accounts. It works similarly to sign in with Google or Facebook buttons that you frequently see. However, Apple touts the privacy of its system over the others, saying that users can sign in to a site or application using iCloud without revealing their email address.
The way it works is when the Sign in with Apple button is activated, an Apple authentication server creates a JSON Web Token (JWT). Users can choose to share their Apple email ID or hide it. If hidden, the server creates an "Apple relay email ID," which is essentially a fake email. The system uses whichever email is chosen, fake or real, to create the JWT. Then the token is validated by the third-party website with the Apple authentication server (diagram below).
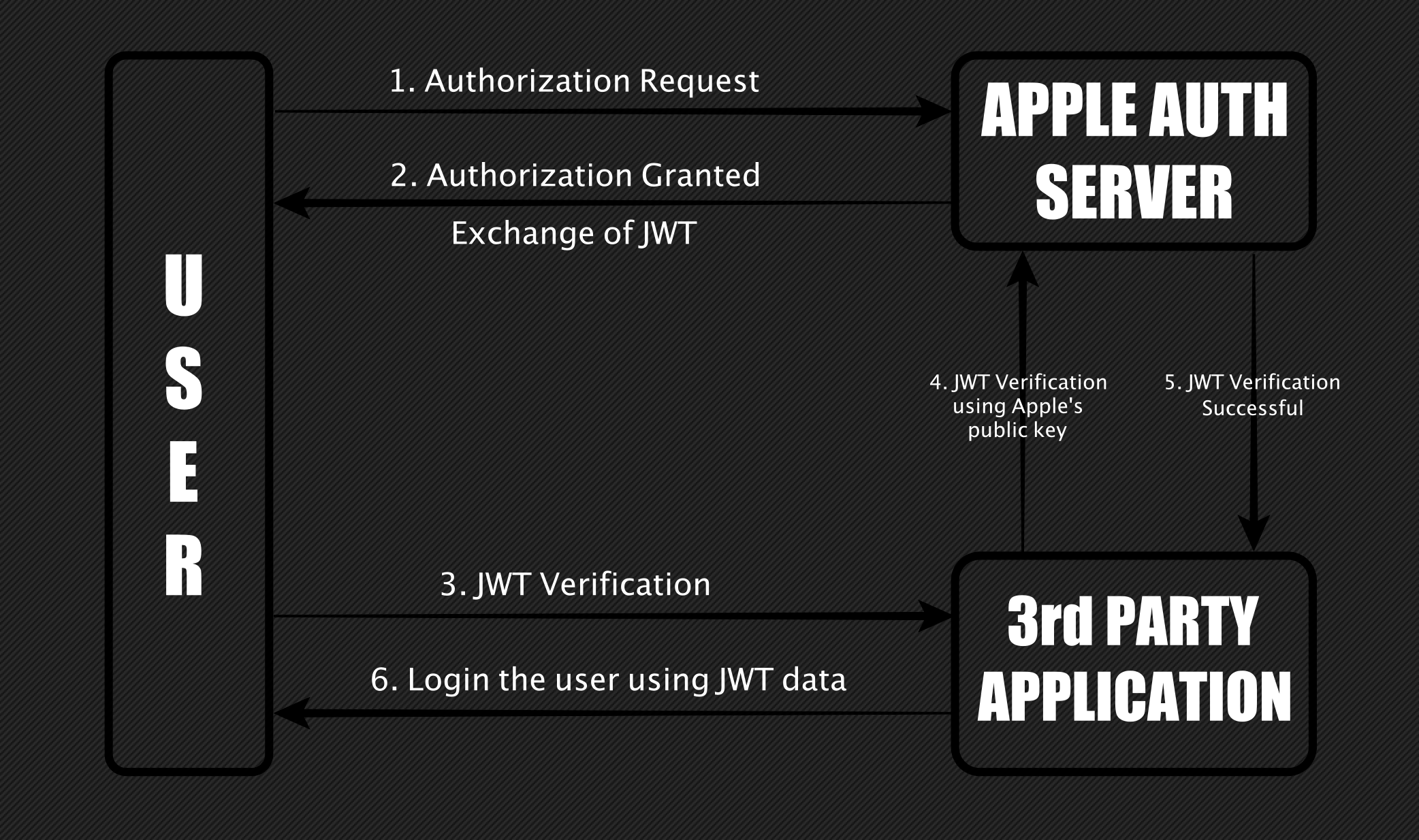
For example, when I used it to sign in to Dropbox, Apple's servers created the email ID "bhbfnub2js@privaterelay.appleid.com." That ID is now permanently linked to my iCloud account for signing in to Dropbox. The method will generate a new one for each application or website you use the Sign in with Apple button.
The problem is, as full stack developer Bhavuk Jain discovered, the system responds to a JWT request for any email ID. The vulnerability essentially allows an attacker to forge an authentication key for any account using the login method.
"When the signature of these tokens was verified using Apple's public key, they showed as valid. This means an attacker could forge a JWT by linking any email ID to it and gaining access to the victim's account," said Jain.
The implications of this exploit are clear. Once authenticated, an attacker can fully take over the victim's account. Several applications have already implemented Sign in with Apple, including Dropbox, Spotify, Airbnb, Giphy, and others.
Jain notified Apple of the bug in April, and it conducted an investigation. Analysis of the company's logs found no misuse nor had the exploit been used to compromise any accounts. It has since patched the security hole. Apple also thanked Jain with a $100,000 bug bounty through the Apple Security Bounty program.
Image credit: Sign In by The Wall Street Journal, Diagram by Bhavuk Jain