In context: In theory, most malicious Android apps come from suspicious web pages or third-party app stores, but security researchers often find them hidden in Google's official Play Store. A new report from Kaspersky suggests hacked Play Store apps are getting more sophisticated.
In a new report published this week, security company Kaspersky describes a dark web market offering services to hack targets with Android malware and spyware. Hackers can sneak much of that malicious code onto the Google Play Store, circumventing Google's most stringent protections.
The first step in the process, and arguably the most dangerous for end users, is hijacking Play Store developer accounts. A prospective attacker can pay a hacker $25-$80 for a developer account that was either stolen or registered with stolen credentials. This lets cybercriminals convert previously trusted apps into vectors for malware.
If an attacker uploads a new app, they might not immediately load it with spyware to avoid drawing attention from Google, but instead, the strategy is to wait until it accrues enough downloads. Hackers also offer services to inflate download numbers and launch Google ad campaigns to make fraudulent apps appear more legitimate.
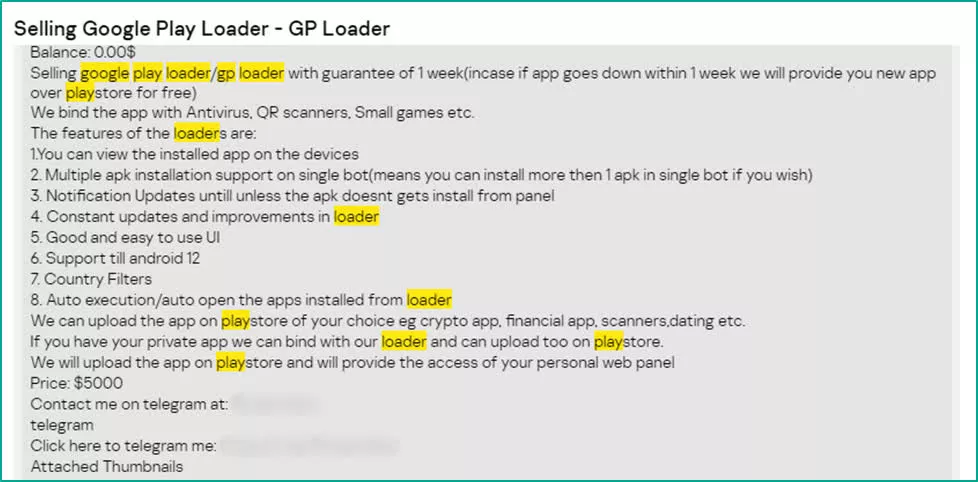
Then, hackers can use loaders to push malicious code to target devices through seemingly legitimate updates, but these might not contain the final malware payload. The app might ask for the user's permission to download apps or other information from outside the Google Play Store, which then fully infects the device to take full control or steal information. Compromised apps sometimes stop working properly until the user grants permission to download the full payload.
Hackers offer a sophisticated range of services and deals when selling malware, including demonstration videos, bundles, auctions, and various payment plans. Malware sellers may ask for a one-time payment, a percentage of the profits from a fraudulent operation, or a subscription fee.
To increase the chances of successful infection, hackers sell obfuscation services that complicate payloads to harden them against Google's security. Conversely, cheaper options exist for binding services that try to infect targets with non-Play Store APKs, which have a lower success rate than loaders.
The most straightforward precaution for users is to never allow Play Store apps to download anything from outside the Play Store, especially if those apps don't usually ask for such permission. Always being careful with what permissions are granted to apps. Developers meanwhile should be extra careful in securing their accounts through common best practices like multi-factor authentication and general vigilance. The most commonly affected apps are cryptocurrency trackers, QR code scanners, dating and financial apps.
