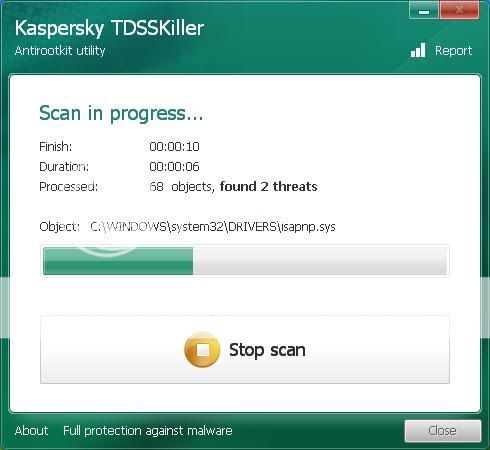
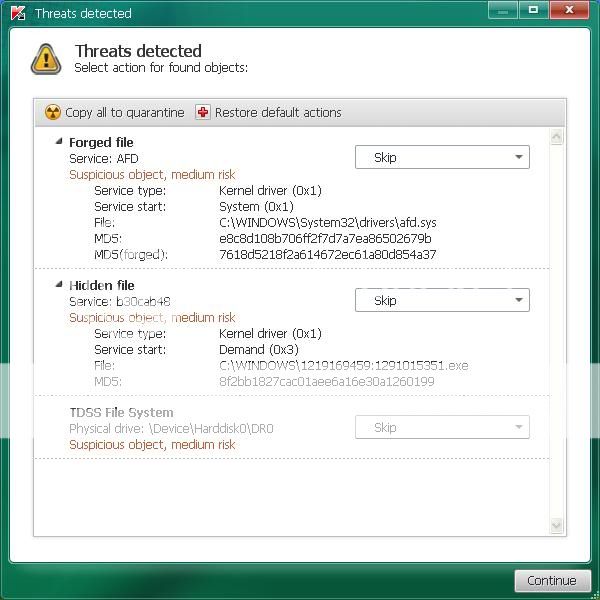
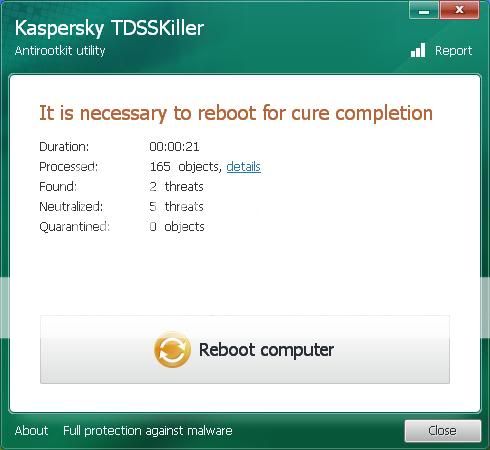
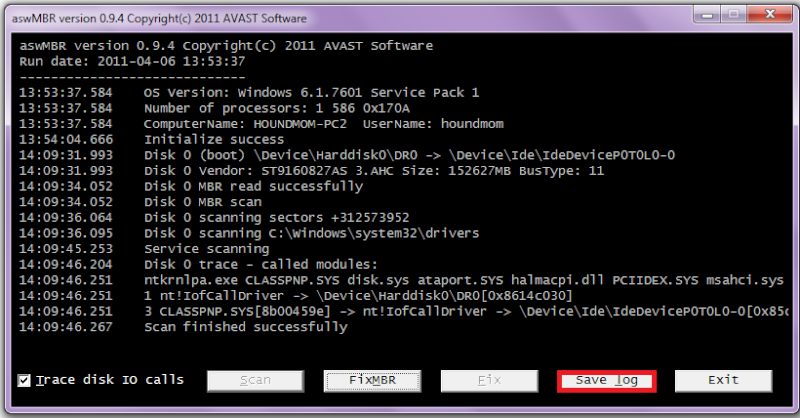
Ok I downloaded the program to a USB drive from another computer because I could not get it to download to my (infected) computer. Now the set-up went smooth. Then I proceeded to check all the boxes you said to excluding the dvd/cd drive. When scan started these boxes began to pop up and I thought maybe if I just left it it would continue. But no it stopped until I chose an option which I went with the recomended unless skip was an only option. I work from 7am to 5pm and I had ran this program last night at 9 and let it do its thing till I came home today and it stopped by itself at 49 percent. here are the logs you requested.
Status: Vulnerability (events: 12)
8/12/2012 9:33:56 PM Vulnerability vulnerability
http://www.securelist.com/en/advisories/43267 C:\Documents and Settings\All Users\HP\HP Deskjet 3000 J310 series\Help\flash\FlashPla.exe Low
8/12/2012 10:33:19 PM Vulnerability vulnerability
http://www.securelist.com/en/advisories/46809 C:\Program Files (x86)\DAEMON Tools Lite\DTLite.exe Low
8/12/2012 10:35:49 PM Vulnerability vulnerability
http://www.securelist.com/en/advisories/49472 C:\Program Files (x86)\Java\jre6\bin\java.exe Low
8/12/2012 10:37:53 PM Vulnerability vulnerability
http://www.securelist.com/en/advisories/49831 C:\Program Files (x86)\Pidgin\pidgin.exe Low
8/12/2012 10:39:54 PM Vulnerability vulnerability
http://www.securelist.com/en/advisories/43267 C:\ProgramData\HP\HP Deskjet 3000 J310 series\Help\flash\FlashPla.exe Low
8/12/2012 10:44:01 PM Vulnerability vulnerability
http://www.securelist.com/en/advisories/43267 C:\Users\All Users\HP\HP Deskjet 3000 J310 series\Help\flash\FlashPla.exe Low
8/12/2012 11:03:06 PM Vulnerability vulnerability
http://www.securelist.com/en/advisories/49086 C:\Windows\SysWOW64\Adobe\Shockwave 11\SwInit.exe Low
8/13/2012 6:38:59 AM Vulnerability vulnerability
http://www.securelist.com/en/advisories/46809 c:\Program Files (x86)\DAEMON Tools Lite\DTLite.exe Low
8/13/2012 6:47:27 AM Vulnerability vulnerability
http://www.securelist.com/en/advisories/49831 c:\Program Files (x86)\Pidgin\pidgin.exe Low
8/13/2012 6:47:28 AM Vulnerability vulnerability
http://www.securelist.com/en/advisories/47447 c:\Program Files (x86)\QuickTime\QuickTimePlayer.exe Low
8/13/2012 6:51:22 AM Vulnerability vulnerability
http://www.securelist.com/en/advisories/49472 c:\Program Files (x86)\Java\jre6\bin\java.exe Low
8/13/2012 6:54:25 AM Vulnerability vulnerability
http://www.securelist.com/en/advisories/43267 c:\ProgramData\HP\HP Deskjet 3000 J310 series\Help\flash\FlashPla.exe Low
Status: Deleted (events: 16)
8/13/2012 6:43:06 AM Deleted Trojan program Trojan.Win64.TDSS.a C:\Documents and Settings\All Users\Microsoft\Windows\DRM\97BC.tmp High
8/13/2012 6:43:06 AM Deleted Trojan program Trojan.Win64.TDSS.a C:\Documents and Settings\All Users\Microsoft\Windows\DRM\97BC.tmp//MPRESS High
8/13/2012 6:43:50 AM Deleted Trojan program Trojan.Win64.TDSS.a C:\Documents and Settings\All Users\Microsoft\Windows\DRM\97BD.tmp High
8/13/2012 6:43:50 AM Deleted Trojan program Trojan.Win64.TDSS.a C:\Documents and Settings\All Users\Microsoft\Windows\DRM\97BD.tmp//MPRESS High
8/13/2012 6:43:28 AM Deleted Trojan program Trojan.Win32.TDSS.istv C:\Documents and Settings\All Users\Microsoft\Windows\DRM\97BC.tmp.dat High
8/13/2012 6:44:38 AM Deleted Trojan program Trojan.Win32.TDSS.istw C:\Documents and Settings\All Users\Microsoft\Windows\DRM\9DB0.tmp High
8/13/2012 6:45:36 AM Deleted Trojan program Backdoor.Win32.ZAccess.uvz C:\FRST\Quarantine\{1ae38341-e383-e5cb-ae21-864215ad12c4}\U\80000064.@ High
8/13/2012 5:39:55 PM Deleted Trojan program Rootkit.Win32.TDSS.gq C:\TDSSKiller_Quarantine\11.07.2012_22.36.09\mbr0000\tdlfs0000\tsk0009.dta High
8/13/2012 5:39:34 PM Deleted Trojan program Rootkit.Boot.Pihar.b C:\TDSSKiller_Quarantine\11.07.2012_22.36.09\mbr0000\mbr0000\tsk0000.dta High
8/13/2012 5:39:34 PM Deleted Trojan program Rootkit.Boot.Pihar.b C:\TDSSKiller_Quarantine\11.07.2012_22.36.09\mbr0000\mbr0000\tsk0000.dta//HDDImage High
8/13/2012 5:39:48 PM Deleted Trojan program Rootkit.Boot.Pihar.b C:\TDSSKiller_Quarantine\11.07.2012_22.36.09\mbr0000\mbr0000\tsk0001.dta High
8/13/2012 5:39:48 PM Deleted Trojan program Rootkit.Boot.Pihar.b C:\TDSSKiller_Quarantine\11.07.2012_22.36.09\mbr0000\mbr0000\tsk0001.dta//vbr0 High
8/13/2012 5:40:02 PM Deleted Trojan program Trojan.Win32.Miner.dw C:\Windows\Installer\{1ae38341-e383-e5cb-ae21-864215ad12c4}\U\00000008.@ High
8/13/2012 5:40:02 PM Deleted Trojan program Trojan.Win32.Miner.dw C:\Windows\Installer\{1ae38341-e383-e5cb-ae21-864215ad12c4}\U\00000008.@//data0000.res High
8/13/2012 5:40:05 PM Deleted Trojan program Backdoor.Win32.ZAccess.mbs C:\Windows\Installer\{1ae38341-e383-e5cb-ae21-864215ad12c4}\U\000000cb.@ High
8/13/2012 6:08:54 PM Deleted Trojan program Backdoor.Win32.ZAccess.mbs c:\Windows\Installer\{1ae38341-e383-e5cb-ae21-864215ad12c4}\U\000000cb.@ High
Status: Absent (events: 10)
8/13/2012 5:41:54 PM Not found Trojan program Backdoor.Win64.ZAccess.bs C:\FRST\Quarantine\Desktop.ini High
8/13/2012 5:41:54 PM Not found Trojan program Trojan.Win64.TDSS.a C:\ProgramData\Microsoft\Windows\DRM\97BD.tmp//MPRESS High
8/13/2012 5:41:54 PM Not found Trojan program Trojan.Win32.TDSS.istw C:\ProgramData\Microsoft\Windows\DRM\9DB0.tmp High
8/13/2012 5:41:54 PM Not found Trojan program Trojan.Win32.TDSS.istv C:\ProgramData\Microsoft\Windows\DRM\97BC.tmp.dat High
8/13/2012 5:41:54 PM Not found Trojan program Trojan.Win64.TDSS.a C:\ProgramData\Microsoft\Windows\DRM\97BC.tmp//MPRESS High
8/13/2012 5:41:54 PM Not found Trojan program Trojan.Win64.TDSS.a C:\Users\All Users\Microsoft\Windows\DRM\97BD.tmp//MPRESS High
8/13/2012 5:41:54 PM Not found Trojan program Trojan.Win32.TDSS.istv C:\Users\All Users\Microsoft\Windows\DRM\97BC.tmp.dat High
8/13/2012 5:41:54 PM Not found Trojan program Trojan.Win32.TDSS.istw C:\Users\All Users\Microsoft\Windows\DRM\9DB0.tmp High
8/13/2012 5:41:54 PM Not found Trojan program Trojan.Win64.TDSS.a C:\Users\All Users\Microsoft\Windows\DRM\97BC.tmp//MPRESS High
8/13/2012 5:41:54 PM Not found Trojan program Backdoor.Win64.ZAccess.br C:\Windows\Installer\{1ae38341-e383-e5cb-ae21-864215ad12c4}\n High
Status: Quarantined (events: 5)
8/13/2012 6:45:33 AM Quarantined Trojan program HEUR:Backdoor.Win64.Generic C:\FRST\Quarantine\{1ae38341-e383-e5cb-ae21-864215ad12c4}\U\80000000.@ High
8/13/2012 5:39:51 PM Quarantined Trojan program HEUR:Trojan.Win32.Generic C:\TDSSKiller_Quarantine\11.07.2012_22.36.09\mbr0000\tdlfs0000\tsk0000.dta High
8/13/2012 5:39:58 PM Quarantined Trojan program HEUR:Trojan.Win32.Generic C:\TDSSKiller_Quarantine\11.07.2012_22.36.09\mbr0000\tdlfs0000\tsk0014.dta High
8/13/2012 5:40:09 PM Quarantined Trojan program HEUR:Backdoor.Win64.Generic C:\Windows\Installer\{1ae38341-e383-e5cb-ae21-864215ad12c4}\U\80000000.@ High
8/13/2012 6:14:35 PM Quarantined Trojan program HEUR:Backdoor.Win64.Generic c:\Windows\Installer\{1ae38341-e383-e5cb-ae21-864215ad12c4}\U\80000000.@ High
Status: Detected (events: 1)
8/13/2012 8:47:30 PM Detected Trojan program Backdoor.Win32.ZAccess.oun C:\Windows\assembly\GAC_32\Desktop.ini High
Status: Will be deleted when the computer is restarted (events: 2)
8/13/2012 5:41:54 PM Will be deleted when the computer is restarted Trojan program Backdoor.Win64.ZAccess.bs C:\Windows\assembly\GAC_64\Desktop.ini High
8/13/2012 5:40:13 PM Will be deleted when the computer is restarted Trojan program Backdoor.Win64.ZAccess.br C:\Windows\SysWOW64\config\systemprofile\AppData\Local\{1ae38341-e383-e5cb-ae21-864215ad12c4}\n High
Status: Will be disinfected when the computer is restarted (events: 1)
8/13/2012 5:41:20 PM Will be disinfected when the computer is restarted virus Virus.Win64.ZAccess.b C:\Windows\System32\services.exe High
Status: Disinfected (events: 1)
8/13/2012 5:43:27 PM Disinfected virus Virus.Win64.ZAccess.b c:\Windows\System32\services.exe High