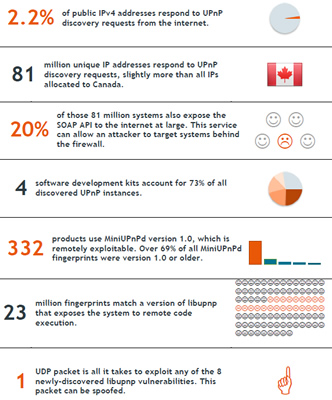
Several security vulnerabilities found within common UPnP implementations have prompted experts at Rapid 7 to recommend the public disable UPnP entirely. Research spanning several months in 2012 revealed that over 2 percent – or about 50 million – of all IPv4 accessible networks suffer from one of just three flaws outlined in the paper (there are eight flaws in total). These vulnerabilities enable hackers to remotely access networks or even execute code. In fact, one remote code execution bug affects 23 million networks and can be triggered by the transmission of a single UDP packet.
UPnP is a zero-config technology that allows software and devices to automagically trigger the opening and forwarding of ports on managed network equipment (e.g. gateway, router, commercial switches). At home, UPnP is particularly useful for game servers, file sharing and P2P applications – essentially any service that depends on incoming connections but doesn't utilize a mediation server. Without UPnP, users must manually configure port forwarding and IP address assignment via their router and firewall administration utilities.
According to security researchers, 81 million unique IPv4 addresses responded to remote UPnP discovery requests. Of those 81 million, about 20 percent allowed SOAP access – an unsettling result when you consider this allowance can permit hackers remote access to networked devices behind a router. Possible exploits include stack overflows, remote code execution and unauthorized access to network management interfaces and even the networks themselves.
Portable UPnP, one of the four major UPnP libraries affected, released a patch today which resolves these troublesome exploits. However, it's up to equipment vendors (e.g. D-Link, Linksys etc..) to incorporate such security fixes into their firmware and distribute it to their users. For this reason, many devices that are no longer supported will remain unprotected indefinitely.
Not sure if your equipment is affected by one of the flaws? Rapid7 is offering a free utility to verify the safety of your network's UPnP implementation. There have been numerous complaints about downloading, installing and running this scanner though: your mileage may vary until they get the bugs worked out. If you're unsure or don't want to take any chances, disabling UPnP is probably the way to go.