Another day another Android malware report. This time cybersecurity software maker Check Point reports that at least 10 million devices have been infected by a new malware dubbed HummingBad that's netting its Beijing-based creators up to $300,000 in monthly revenue through the forced downloading of apps and clicking of ads.
Curiously, the company behind the attack is said to also run a legitimate advertising analytics business. According to the report (PDF), Yingmob has several teams developing tracking and ad platforms, while the malicious component was developed by the 'Development Team for Overseas Platform' which includes four groups with a total of 25 employees.
HummingBad uses a "drive-by-download" attack in which phones are infected when visiting a malicious website. It first tries to gain root access by exploiting multiple known Android vulnerabilities. If rooting fails a second component uses a fake system update notification to trick users into granting system-level permissions.
Once a phone is infected HummingBad will generate fraudulent ad revenue and install additional fraudulent apps. Check Point believes the group behind the attack can further escalate the attack by pooling resources from over 10 million devices to create powerful botnets, conduct highly-targeted attacks, or build new streams of revenue by selling access to devices under their control to the highest bidder.
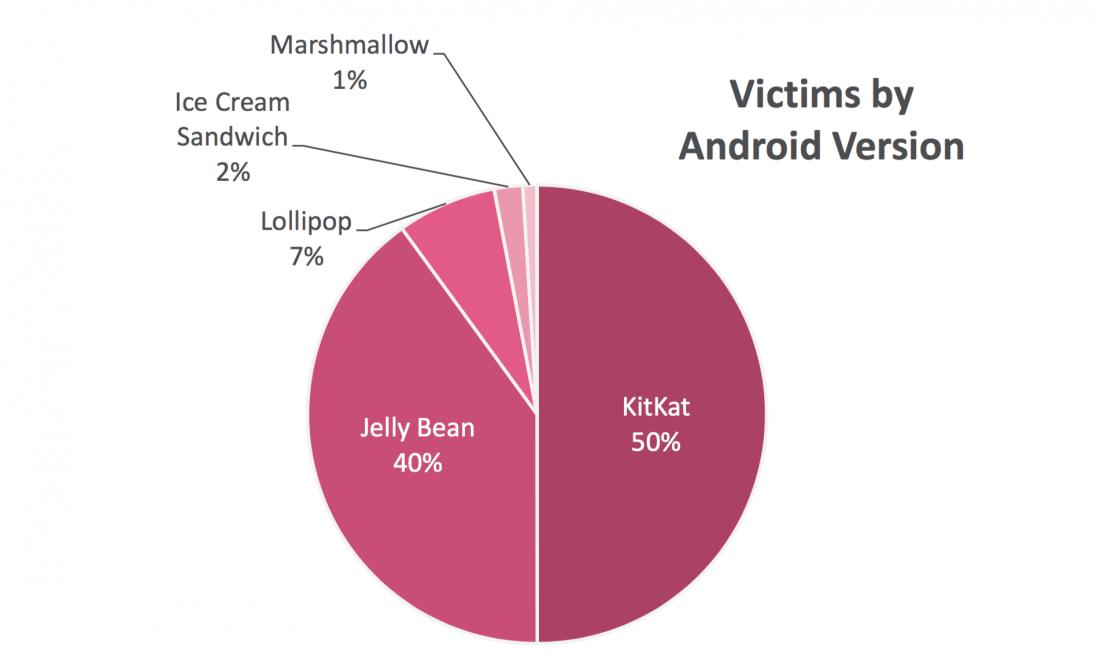
The bulk of infected devices are in China, India, Philippines, Indonesia, Turkey and Brazil. The US is eighth on the list with 288,800 infected devices. As many as 90% of those infected are running either Kitkat or Jelly Bean versions of Android, with Lollipop, Ice Cream Sandwich and Marshmallow making up the remaining 10%.