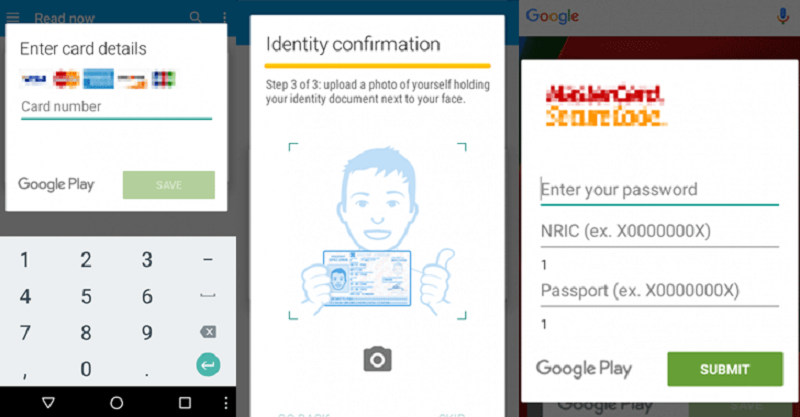
Not content with stealing your financial details, personal information, and login credentials, there's now an Android banking Trojan that also asks victims to take a selfie with their ID cards.
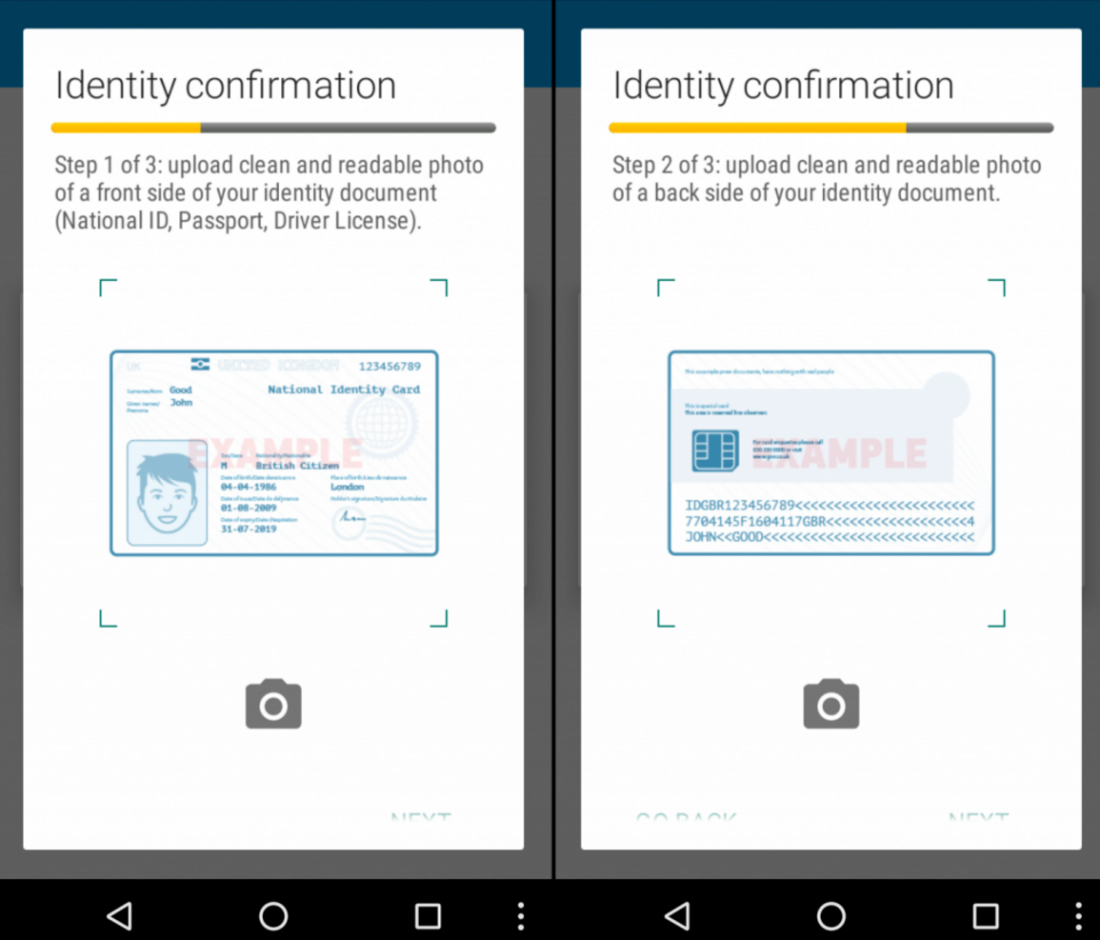
McAfee Labs' Mobile Research Team discovered the malicious application, which is a new variant of the Acecard Trojan Malware (aka Torec) that was first identified back in February. In addition to asking for credit card details and information such as "mother's maiden name," the updated app offers "identify confirmation," which involves uploading photos of identity documents such as a driver's license along with a selfie of the gullible user holding the ID.
As is the case with many Trojans, Acecard installs itself by tricking the user into thinking they're installing a video codec/plugin or app for watching adult videos. Once it's on the Android device, the malware asks for administrator privileges, before running in the background while monitoring specific apps.
Acecard then shows a phishing overlay that pretends to be Google Play asking for a credit card number. This is followed by requests for name, date of birth, phone number, card expiration date, and CCV. It will also request second-factor authentication for some cards. Anyone who lives in Hong Kong will be asked for a copy of their HK ID card, while Singapore residents must add their National Registration card and passport.
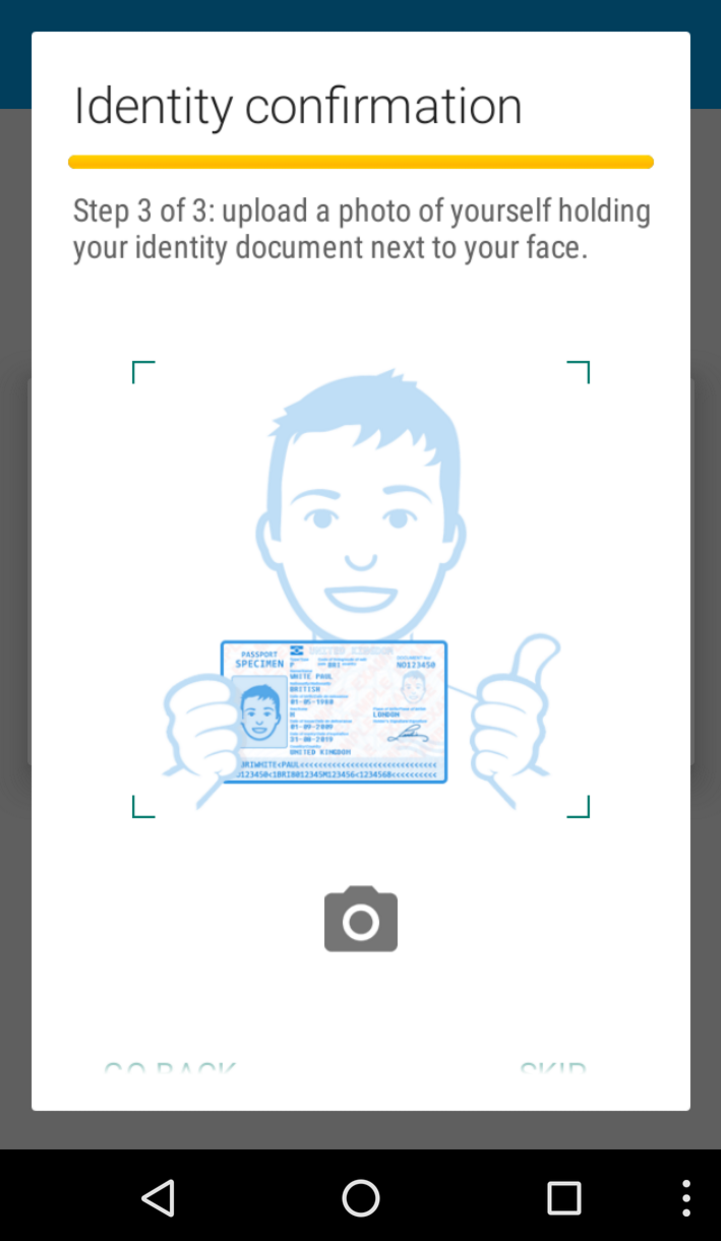
It's at this point where the malware requests photos of the documents, along with selfies of the victim holding their ID. If someone's got this far, there's a pretty good chance they'll send the photographs without getting suspicious. They'll probably only realize something's amiss when their bank accounts are emptied, credit cards get maxed out, and bizarre doppelgangers start appearing on social media sites.