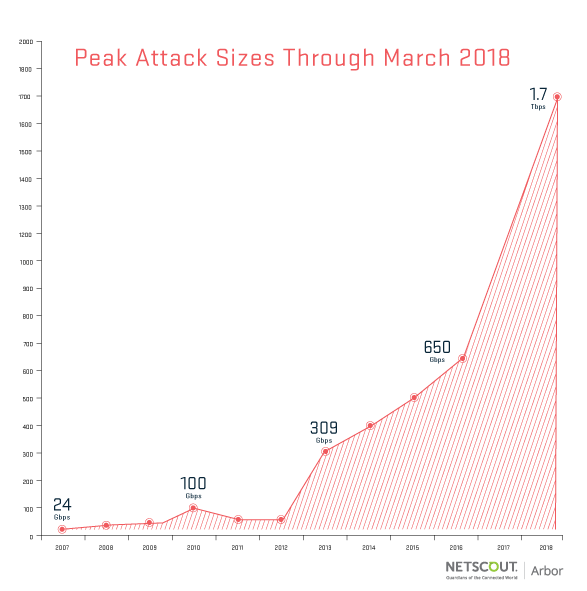
As we reported last week code repository, GitHub was hit with the largest DDoS attack ever recorded on Wednesday. The directed denial of service only incapacitated the site for around nine minutes, but the strike pummeled servers with data volumes reaching almost 2Tbps.
Initially, GitHub reported the attack peaking at 1.3 Tbps, but this week DDoS mitigation service Netscout Arbor confirmed that the peak was closer to 1.7Tbps --- 2.5 times bigger than the previous record. These volumes were achieved using a reflection/amplification vector that exploits memcached servers to amplify the attacker's sent data by a factor of 51,000.
Initially, the attack seemed to be random. However, cybersecurity firm Cybereason reports that analysis of the data payload revealed a ransom note. The message was embedded within a line of Python code that was delivered by the compromised machines. It demanded GitHub hand over 50 XMR (Monero cryptocurrency). This amounts to about $15,000 US.
Cybersecurity strategist Nick Bilogorskiy with Juniper Networks told SecurityWeek, "It is a pretty clever trick to embed the ransom demand inside the DOS payload. It is also fitting with the times that attackers are asking for Monero rather than Bitcoin because Monero disguises the origin, destination and amount of each transaction, making it more suitable for ransoms."
DDoS mitigation services including Akamai, Cloudflare and Arbor are forecasting more memcached attacks on the horizon. The attack vector used to be relatively rare because it required skilled techs to execute it manually.
"[However], the attack techniques have now been weaponized and made available to all skill-levels via so-called booter/stresser [sic] botnets," said SecurityWeek.
Fortunately, memcached attacks are relatively easy to mitigate, and admins have already begun taking preventative measures.
Ashley Stephenson, CEO of Corero Network Security said, "Overall memcached is expected to top the DDoS charts for a relatively short period of time. Ironically, as we have seen before, the more attackers who try to leverage this vector the weaker the resulting DDoS attacks as the total bandwidth of vulnerable servers is fixed and is shared across the victims."
In other words, attackers using this vector are likely to run themselves out of business relatively quickly.
