A hot potato: It's not the first time IT admins and users have been alerted to a flaw in the Windows Print Spooler service. The latest 0-day vulnerability in this Windows component was apparently meant to be detailed in the upcoming annual Black Hat security conference, however, security researchers accidentally posted a proof-of-concept prematurely, and now Microsoft is warning users about the 0-day flaw being actively exploited in the wild.

Update (July 7): Microsoft has released mandatory security updates for several Windows versions including 10, 8.1, 7, and Server editions to patch the 'PrintNightmare' exploit.
For most users, this out-of-band update should download automatically via Windows Update. Microsoft also notes that a patch for Windows 10 version 1607, Windows Server 2016 and Server 2012 will be released soon.
The original story follows below:
Microsoft fixed an RCE vulnerability in the Windows Print Spooler service in its June Patch Tuesday security update, but now another 0-day flaw has surfaced that's currently being investigated by the company and is noted to be under active exploitation.
Dubbed 'PrintNightmare,' the US Cybersecurity & Infrastructure Security Agency (CISA) has called it a 'critical' remote code execution vulnerability, though Microsoft is yet to assign it a severity score.
Essentially, a function in the Windows Print Spooler service allows a remotely authenticated attacker to run arbitrary code with SYSTEM privileges. "An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights," notes Microsoft.
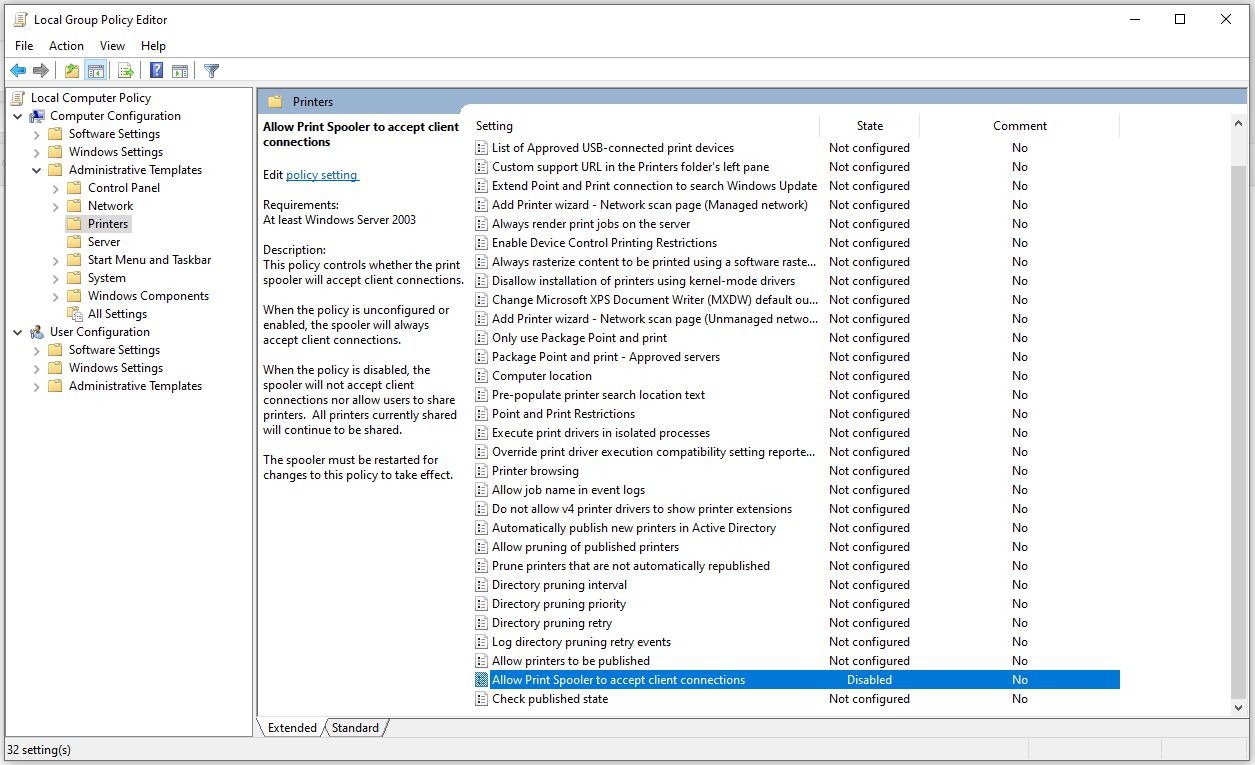
System admins have been strongly advised to disable the Windows Print Spooler service on servers/domain controllers/PCs that aren't used for printing, while another recommended workaround is to disable inbound remote printing via Group Policy in case users still want access to local printing with a directly attached device.
This spooler service flaw is also reminiscent of the one discovered in 2016, and Microsoft notes that the latest vulnerability exists on all versions of Windows, though it's not yet clear which versions are exploitable. A fix is currently said to be in the works, which Microsoft may release outside of its usual Patch Tuesday schedule.
Image credit: PCMag