A hot potato: Microsoft rushed to release a fix for the recently discovered 'PrintNightmare' vulnerability, pushing it as a mandatory security update for several Windows versions. Although the patch bolstered protection with the added requirement of admin credentials during installation of unsigned printer drivers on print servers, a security researcher and developer reverse engineered a Windows DLL to bypass Microsoft's check for remote libraries and was able to exploit a fully patched server.
Update (9 July): With questions hanging around the effectiveness of Microsoft's latest out-of-band patch for PrintNightmare, the company has posted a clarified guidance on the issue following demonstrations of security researchers bypassing the fix.
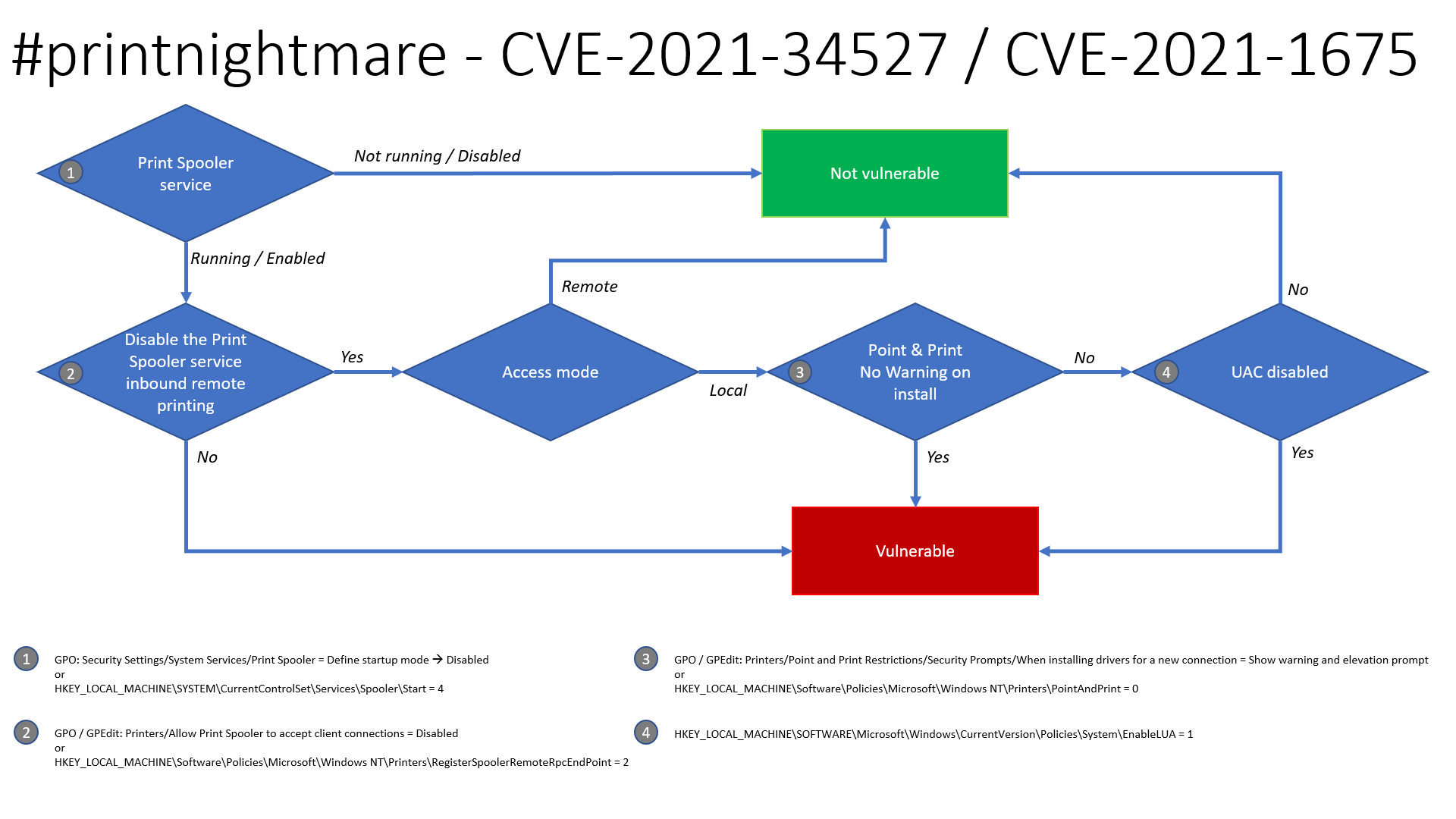
Our investigation has shown that the OOB security update is working as designed and is effective against the known printer spooling exploits and other public reports collectively being referred to as PrintNightmare. All reports we have investigated have relied on the changing of default registry setting related to Point and Print to an insecure configuration.
Microsoft strongly advises users to update to the latest patch and make sure to review system registry settings by going through the following steps:
- In ALL cases, apply the CVE-2021-34527 security update. The update will not change existing registry settings
- After applying the security update, review the registry settings documented in the CVE-2021-34527 advisory
- If the registry keys documented do not exist, no further action is required
- If the registry keys documented exist, in order to secure your system, you must confirm that the following registry keys are set to 0 (zero) or are not present:
- HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
- NoWarningNoElevationOnInstall = 0 (DWORD) or not defined (default setting)
- UpdatePromptSettings = 0 (DWORD) or not defined (default setting)
In related news, the PrintNightmare patch (KB5004945) has caused problems for Zebra printers, with the company releasing the following statement to The Verge:
We are aware of a printing issue caused by the July 6 Windows "KB5004945" update affecting multiple brands of printers. Microsoft has investigated this issue and plans to release an update addressing the issue within the next 1-2 business days. An immediate way to address the issue is to uninstall the Windows "KB5004945" update or uninstall the affected printer driver and reinstall using Administrative credentials. Long term, we encourage the use of the newer Windows update Microsoft is planning to release. Customers who need assistance regarding Zebra printers may contact our Technical Support Team.
PrintNightmare allows a remote attacker to take advantage of a flaw in the Windows Printer Spooler service and execute arbitrary commands with escalated privileges. Microsoft quickly addressed the critical vulnerability - found on all Windows versions - with an out-of-band security update.
However, it now looks like the exploit could be turning into an actual nightmare for Microsoft and IT admins following a demonstration of how the fix could be bypassed to leave a fully patched server vulnerable to PrintNightmare.
Dealing with strings & filenames is hard😉
--- 🥝 Benjamin Delpy (@gentilkiwi) July 7, 2021
New function in #mimikatz 🥝to normalize filenames (bypassing checks by using UNC instead of \\server\share format)
So a RCE (and LPE) with #printnightmare on a fully patched server, with Point & Print enabled
> https://t.co/Wzb5GAfWfd pic.twitter.com/HTDf004N7r
Benjamin Delpy, a security researcher and developer of the Mimikatz security tool, notes that Microsoft employs a "\\" check in the filename format to determine if a library is remote or not. However, it can be bypassed by using UNC, which allowed Delpy to run an exploit on a fully patched Windows Server 2019 with Point and Print service enabled.
Microsoft also notes in its advisory that using the 'Point and Print' technology "weakens the local security posture in such a way that exploitation will be possible." The combination of UNC bypass and the PoC (removed from GitHub but circulating on the web) potentially leaves room for attackers to cause widespread harm.
Speaking to The Register, Delpy described the issue as "weird from Microsoft," noting that he believed the company did not test the fix for real. It remains to be seen when (and if) Microsoft can permanently patch 'PrintNightmare,' which has already begun disrupting workflows for organizations globally.
Many universities, for example, have started disabling campus-wide printing, while other internet-connected institutions and businesses that don't use remote printing still need to ensure that appropriate group policy settings are in place since 'PrintNightmare' is under active exploitation.