You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Solved Heuristics.reserved.word.exploit
- Thread starter TrunkMonkey
- Start date
Jay Pfoutz
Posts: 4,279 +49
Check my signature below ~DMJ, it contains a link to the donation page.
For junk cleaners, AdwCleaner and Junkware Removal Tool took care of any adware. Which wasn't much on your computer, to be honest. Otherwise, we can finish up here, which will clean up our tools that we used and clean out leftover temporary files and old system restore points. It'll leave your computer squeaky clean...
Clean up System Restore
Now, to get you off to a clean start, we will be creating a new Restore Point, then clearing the old ones to make sure you do not get reinfected, in case you need to "restore back."
To manually create a new Restore Point
Remove tools, temp files, old Restore Points
Please run OTL
Double click OTL.exe.
Security Check
Please download Security Check by screen317 from SpywareInfoforum.org or Changelog.fr.
For junk cleaners, AdwCleaner and Junkware Removal Tool took care of any adware. Which wasn't much on your computer, to be honest. Otherwise, we can finish up here, which will clean up our tools that we used and clean out leftover temporary files and old system restore points. It'll leave your computer squeaky clean...
Clean up System Restore
Now, to get you off to a clean start, we will be creating a new Restore Point, then clearing the old ones to make sure you do not get reinfected, in case you need to "restore back."
To manually create a new Restore Point
- Go to Control Panel and select System and Maintenance
- Select System
- On the left select Advance System Settings and accept the warning if you get one
- Select System Protection Tab
- Select Create at the bottom
- Type in a name I.e. Clean
- Select Create
Remove tools, temp files, old Restore Points
Please run OTL
- Under the Custom Scans/Fixes box at the bottom, copy and paste in the following:
:files
ipconfig /flushdns /c
:commands
[CREATERESTOREPOINT]
[CLEARALLRESTOREPOINTS]
[emptyflash]
[emptytemp]
[emptyjava]
[reboot] - Then click the Run Fix button at the top.
- Note: The fix for OTL sometimes hides your Desktop and Start menu so the cleanup can be completed. Do not be alerted, as this is normal.
- It may open a log for you, but I don't need that.
Double click OTL.exe.
- Click the CleanUp button.
- Select Yes when the "Begin cleanup Process?" prompt appears.
- If you are prompted to Reboot during the cleanup, select Yes.
- The tool will delete itself once it finishes.
Security Check
Please download Security Check by screen317 from SpywareInfoforum.org or Changelog.fr.
- Save it to your Desktop.
- Double click SecurityCheck.exe and follow the onscreen instructions inside of the black box.
- A Notepad document should open automatically called checkup.txt; please post the contents of that document.
TrunkMonkey
Posts: 73 +0
Noticed OTL never had the box checked "scan all users" and I have 2 accounts. Just an FYI. How to remove other tools like JTR and Adwcleaner. Uninstall through control panel or just delete files?
TrunkMonkey
Posts: 73 +0
Results of screen317's Security Check version 0.99.56
Windows 7 Service Pack 1 x64 (UAC is enabled)
Internet Explorer 9
``````````````Antivirus/Firewall Check:``````````````
Windows Firewall Enabled!
Microsoft Security Essentials
Antivirus up to date!
`````````Anti-malware/Other Utilities Check:`````````
Malwarebytes Anti-Malware version 1.70.0.1100
Java 7 Update 9
Adobe Flash Player 11.5.502.146
Adobe Reader XI
Google Chrome 23.0.1271.97
````````Process Check: objlist.exe by Laurent````````
Microsoft Security Essentials MSMpEng.exe
Microsoft Security Essentials msseces.exe
Malwarebytes Anti-Malware mbamservice.exe
Malwarebytes Anti-Malware mbamgui.exe
Malwarebytes' Anti-Malware mbamscheduler.exe
`````````````````System Health check`````````````````
Total Fragmentation on Drive C: 7%
````````````````````End of Log``````````````````````
Windows 7 Service Pack 1 x64 (UAC is enabled)
Internet Explorer 9
``````````````Antivirus/Firewall Check:``````````````
Windows Firewall Enabled!
Microsoft Security Essentials
Antivirus up to date!
`````````Anti-malware/Other Utilities Check:`````````
Malwarebytes Anti-Malware version 1.70.0.1100
Java 7 Update 9
Adobe Flash Player 11.5.502.146
Adobe Reader XI
Google Chrome 23.0.1271.97
````````Process Check: objlist.exe by Laurent````````
Microsoft Security Essentials MSMpEng.exe
Microsoft Security Essentials msseces.exe
Malwarebytes Anti-Malware mbamservice.exe
Malwarebytes Anti-Malware mbamgui.exe
Malwarebytes' Anti-Malware mbamscheduler.exe
`````````````````System Health check`````````````````
Total Fragmentation on Drive C: 7%
````````````````````End of Log``````````````````````
Jay Pfoutz
Posts: 4,279 +49
TrunkMonkey
Posts: 73 +0
Nope just a very big thank you. Do you get donations personally or does it go to company? Either way I'll be kicking something in.
Jay Pfoutz
Posts: 4,279 +49
The donation actually goes to me personally from my link in the signature there. I frequently use donations from online towards the security community. I'm preparing for renewals of a security website that I own. Otherwise, if that's all, this topic is now solved. 
Jay Pfoutz
Posts: 4,279 +49
Topic reopened.
Please download 7-Zip and install it. If you already have it, no need to reinstall.
Then, download RootkitUnhooker and save the setup to your Desktop.
Please download 7-Zip and install it. If you already have it, no need to reinstall.
Then, download RootkitUnhooker and save the setup to your Desktop.
- Right-click on the RootkitUnhooker setup and mouse-over 7-Zip then click Extract to "RKU***"
- Once that is done, enter the folder, and double-click on the setup file. Navigate through setup and finish.
- Once that is done, you will see another folder that was created inside the RKU folder. Enter that folder, and double-click on the randomly named file. (It will be alpha-numeric and have an EXE extension on it.)
- It will initialize itself and load the scanner. It will also install its driver. Please wait for the interface to begin.
- Once inside the interface, do not fix anything. Click on the Report tab.
- Next, click on the Scan button and a popup will show. Make sure all are checked, then click on OK. It will begin scanning. When it gets to the Files tab, it will ask you what drives to scan. Just select C:\ and hit OK.
- It will finish in about 5 minutes or a little longer depending on how badly infected the system is, or if your security software is enabled.
- When finished, it will show the report in the Report tab. Please copy all of it, and post it in your next reply. Depending on how large the log is, you may have to use two or three posts to get all the information in.
TrunkMonkey
Posts: 73 +0
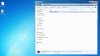 I'm not getting the folder within a folder, containing the randomly named .exe
I'm not getting the folder within a folder, containing the randomly named .exeThis is after running the set up and clicking finish. I see RKU is now installed and in the start menu.
- Right-click on the RootkitUnhooker setup and mouse-over 7-Zip then click Extract to "RKU***"
- Once that is done, enter the folder, and double-click on the setup file. Navigate through setup and finish.
- Once that is done, you will see another folder that was created inside the RKU folder. Enter that folder, and double-click on the randomly named file. (It will be alpha-numeric and have an EXE extension on it.)
TrunkMonkey
Posts: 73 +0
I have blocked that domain in the router setup and everywhere possible in chrome. FYI this is a fresh install of win7 on a brand new hard drive, and the original C: drive is also installed as a non bootable drive, so I can transfer files. I'm going to unhook that drive now (F . Let me know if I should leave it hooked up, but for now it's freaking me out.
. Let me know if I should leave it hooked up, but for now it's freaking me out.
TrunkMonkey
Posts: 73 +0
Jay Pfoutz
Posts: 4,279 +49
Sorry you had trouble with that.
- What's your current drive setup and which ones do you think are infected?
- Are you saying you just reformatted/reinstalled, or you did that before you originally got infected?
- Are the issues happening with browsing only? Or is there a lot of system trouble?
TrunkMonkey
Posts: 73 +0
Here's how it went:
Old c: drive was the one I came to you with the original major issues. Once we were done,
Removed old C: drive.
Replaced it with fresh seagate 2tb and did a fresh format/install from OEM win7 DVD.
Put old c: back in as a 2nd drive to eventually transfer files.
I have a 2nd new Seagate which is for media and data so needed to get that installed and formatted so I could move files from old c:
2nd seagate has yet to be recognized by bios or windows, another tech support conversation going on with Seagate.
In the mean time I have accessed some media from old c: but copied over nothing. Trying to keep this clean
Everything seemed good until using chrome to visit Walmart money card.com yesterday and redirect happened, but MAB blocked it and I freaked out and let you know. The credit card was compromised and $100 charged over the last few months in many tiny transactions. Uninstalled chrome and everything seems great.PC is very quick and responsive and I havent anything happen with the Internet Explorer. So maybe it's a Google only redirect I read about however I'm trying to figure out where the heck that lives being that this is a new install of Chrome and windows and a brand new hard drive. As I mentioned Google syncs everything with my phone and PC, apps, contact, et cetera. Ever heard of a google account being infected. They might have my password but I changed it yesterday. Security program on my phone has registered nothing and I have not noticed any issues there, it's running Avast. Let me know if you want me to clarify anything I will be near a browser all afternoon. Thanks a lot.
Old c: drive was the one I came to you with the original major issues. Once we were done,
Removed old C: drive.
Replaced it with fresh seagate 2tb and did a fresh format/install from OEM win7 DVD.
Put old c: back in as a 2nd drive to eventually transfer files.
I have a 2nd new Seagate which is for media and data so needed to get that installed and formatted so I could move files from old c:
2nd seagate has yet to be recognized by bios or windows, another tech support conversation going on with Seagate.
In the mean time I have accessed some media from old c: but copied over nothing. Trying to keep this clean
Everything seemed good until using chrome to visit Walmart money card.com yesterday and redirect happened, but MAB blocked it and I freaked out and let you know. The credit card was compromised and $100 charged over the last few months in many tiny transactions. Uninstalled chrome and everything seems great.PC is very quick and responsive and I havent anything happen with the Internet Explorer. So maybe it's a Google only redirect I read about however I'm trying to figure out where the heck that lives being that this is a new install of Chrome and windows and a brand new hard drive. As I mentioned Google syncs everything with my phone and PC, apps, contact, et cetera. Ever heard of a google account being infected. They might have my password but I changed it yesterday. Security program on my phone has registered nothing and I have not noticed any issues there, it's running Avast. Let me know if you want me to clarify anything I will be near a browser all afternoon. Thanks a lot.
Jay Pfoutz
Posts: 4,279 +49
I doubt a Google Account would be infected. I'd say that's strange.
Unless if a device was infected. Keep me updated. I'll keep this open for five days, before solving it again.
Unless if a device was infected. Keep me updated. I'll keep this open for five days, before solving it again.
TrunkMonkey
Posts: 73 +0
OK. Im glad to not see symptoms right now. However I was able to reproduce the redirect yesterday just by attempting to navigate to the site again via chrome. the redirect was always to the same site http://testalby.net/d/www.walmartmoneycard.com
That's when I uninstalled it immediately. I have to assume that means something is lurking.
That's when I uninstalled it immediately. I have to assume that means something is lurking.
Jay Pfoutz
Posts: 4,279 +49
Let's take a look with a couple of tools...
Farbar Service Scanner
Please download Farbar Service Scanner (FSS) and run it on the computer with the issue.
Windows Signature Verification Scan
1. Click Start, click Run, type sigverif, and then click OK.
2. Click Advanced, click Look for other files that are not digitally signed, navigate to the Winnt\System32\Drivers folder, and then click OK.
3. Click Start.
4. After it has finished running, navigate to C:\Windows\Sigverify.txt, open it and post the contents of the log here.
Malwarebytes' Anti-Rootkit
Please download Malwarebytes' Anti-Rootkit and save it to your desktop.
Farbar Service Scanner
Please download Farbar Service Scanner (FSS) and run it on the computer with the issue.
- Make sure the following options are checked:
- Internet Services
- Windows Firewall
- System Restore
- Security Center
- Windows Update
- Windows Defender
- Press "Scan".
- It will create a log (FSS.txt) in the same directory the tool is run.
- Please copy and paste the log to your reply.
Windows Signature Verification Scan
1. Click Start, click Run, type sigverif, and then click OK.
2. Click Advanced, click Look for other files that are not digitally signed, navigate to the Winnt\System32\Drivers folder, and then click OK.
3. Click Start.
4. After it has finished running, navigate to C:\Windows\Sigverify.txt, open it and post the contents of the log here.
Malwarebytes' Anti-Rootkit
Please download Malwarebytes' Anti-Rootkit and save it to your desktop.
- Be sure to print out and follow the instructions provided on that same page for performing a scan.
- Caution: This is a beta version so also read the disclaimer and back up all your data before using.
- When the scan completes, click on the Cleanup button to remove any threats found and reboot the computer if prompted to do so.
- Perform another scan with Malwarebytes Anti-Rootkit to verify that no threats remain. If they do, then click Cleanup once more and repeat the process.
- If there are problems with Internet access, Windows Update, Windows Firewall or other system issues, run the fixdamage tool located in the folder Malwarebytes Anti-Rootkit was run from and reboot your computer.
- Two files (mbar-log-YYYY-MM-DD, system-log.txt) will be created and saved within that same folder.
- Copy and paste the contents of these two log files in your next reply.
TrunkMonkey
Posts: 73 +0
Ah ha! Google IP is hosed. I sometimes would have to try a second time to reach their sites. This makes sense. I also get a constant sync error on my Galaxy S3, even though things are syncing. Wonder if it's related. Running MAB now.
Farbar Service Scanner Version: 16-01-2013
Ran by Justin Sidwell (administrator) on 15-01-2013 at 19:02:10
Running from "C:\Users\Justin Sidwell\Desktop"
Windows 7 Professional Service Pack 1 (X64)
Boot Mode: Normal
****************************************************************
Internet Services:
============
Connection Status:
==============
Localhost is accessible.
LAN connected.
Attempt to access Google IP returned error. Google IP is offline
Google.com is accessible.
Yahoo IP is accessible.
Yahoo.com is accessible.
Windows Firewall:
=============
Firewall Disabled Policy:
==================
System Restore:
============
System Restore Disabled Policy:
========================
Action Center:
============
Windows Update:
============
Windows Autoupdate Disabled Policy:
============================
Windows Defender:
==============
WinDefend Service is not running. Checking service configuration:
The start type of WinDefend service is set to Demand. The default start type is Auto.
The ImagePath of WinDefend service is OK.
The ServiceDll of WinDefend service is OK.
Windows Defender Disabled Policy:
==========================
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender]
"DisableAntiSpyware"=DWORD:1
Other Services:
==============
File Check:
========
C:\Windows\System32\nsisvc.dll => MD5 is legit
C:\Windows\System32\drivers\nsiproxy.sys => MD5 is legit
C:\Windows\System32\dhcpcore.dll => MD5 is legit
C:\Windows\System32\drivers\afd.sys => MD5 is legit
C:\Windows\System32\drivers\tdx.sys => MD5 is legit
C:\Windows\System32\Drivers\tcpip.sys => MD5 is legit
C:\Windows\System32\dnsrslvr.dll => MD5 is legit
C:\Windows\System32\mpssvc.dll => MD5 is legit
C:\Windows\System32\bfe.dll => MD5 is legit
C:\Windows\System32\drivers\mpsdrv.sys => MD5 is legit
C:\Windows\System32\SDRSVC.dll => MD5 is legit
C:\Windows\System32\vssvc.exe => MD5 is legit
C:\Windows\System32\wscsvc.dll => MD5 is legit
C:\Windows\System32\wbem\WMIsvc.dll => MD5 is legit
C:\Windows\System32\wuaueng.dll => MD5 is legit
C:\Windows\System32\qmgr.dll => MD5 is legit
C:\Windows\System32\es.dll => MD5 is legit
C:\Windows\System32\cryptsvc.dll => MD5 is legit
C:\Program Files\Windows Defender\MpSvc.dll => MD5 is legit
C:\Windows\System32\svchost.exe => MD5 is legit
C:\Windows\System32\rpcss.dll => MD5 is legit
**** End of log ****
Farbar Service Scanner Version: 16-01-2013
Ran by Justin Sidwell (administrator) on 15-01-2013 at 19:02:10
Running from "C:\Users\Justin Sidwell\Desktop"
Windows 7 Professional Service Pack 1 (X64)
Boot Mode: Normal
****************************************************************
Internet Services:
============
Connection Status:
==============
Localhost is accessible.
LAN connected.
Attempt to access Google IP returned error. Google IP is offline
Google.com is accessible.
Yahoo IP is accessible.
Yahoo.com is accessible.
Windows Firewall:
=============
Firewall Disabled Policy:
==================
System Restore:
============
System Restore Disabled Policy:
========================
Action Center:
============
Windows Update:
============
Windows Autoupdate Disabled Policy:
============================
Windows Defender:
==============
WinDefend Service is not running. Checking service configuration:
The start type of WinDefend service is set to Demand. The default start type is Auto.
The ImagePath of WinDefend service is OK.
The ServiceDll of WinDefend service is OK.
Windows Defender Disabled Policy:
==========================
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender]
"DisableAntiSpyware"=DWORD:1
Other Services:
==============
File Check:
========
C:\Windows\System32\nsisvc.dll => MD5 is legit
C:\Windows\System32\drivers\nsiproxy.sys => MD5 is legit
C:\Windows\System32\dhcpcore.dll => MD5 is legit
C:\Windows\System32\drivers\afd.sys => MD5 is legit
C:\Windows\System32\drivers\tdx.sys => MD5 is legit
C:\Windows\System32\Drivers\tcpip.sys => MD5 is legit
C:\Windows\System32\dnsrslvr.dll => MD5 is legit
C:\Windows\System32\mpssvc.dll => MD5 is legit
C:\Windows\System32\bfe.dll => MD5 is legit
C:\Windows\System32\drivers\mpsdrv.sys => MD5 is legit
C:\Windows\System32\SDRSVC.dll => MD5 is legit
C:\Windows\System32\vssvc.exe => MD5 is legit
C:\Windows\System32\wscsvc.dll => MD5 is legit
C:\Windows\System32\wbem\WMIsvc.dll => MD5 is legit
C:\Windows\System32\wuaueng.dll => MD5 is legit
C:\Windows\System32\qmgr.dll => MD5 is legit
C:\Windows\System32\es.dll => MD5 is legit
C:\Windows\System32\cryptsvc.dll => MD5 is legit
C:\Program Files\Windows Defender\MpSvc.dll => MD5 is legit
C:\Windows\System32\svchost.exe => MD5 is legit
C:\Windows\System32\rpcss.dll => MD5 is legit
**** End of log ****
TrunkMonkey
Posts: 73 +0
TrunkMonkey
Posts: 73 +0
I was able to repair Windows to some degree, at least enough to re-do your last set of instructions. It was bizarre watching it grind to a halt right before my eyes. Here is Farbar report again.
Farbar Service Scanner Version: 16-01-2013
Ran by Justin Sidwell (administrator) on 16-01-2013 at 07:25:47
Running from "C:\Users\Justin Sidwell\Desktop"
Windows 7 Professional Service Pack 1 (X64)
Boot Mode: Normal
****************************************************************
Internet Services:
============
Connection Status:
==============
Localhost is accessible.
LAN connected.
Attempt to access Google IP returned error. Google IP is offline
Google.com is accessible.
Yahoo IP is accessible.
Yahoo.com is accessible.
Windows Firewall:
=============
Firewall Disabled Policy:
==================
System Restore:
============
System Restore Disabled Policy:
========================
Action Center:
============
Windows Update:
============
Windows Autoupdate Disabled Policy:
============================
Windows Defender:
==============
WinDefend Service is not running. Checking service configuration:
The start type of WinDefend service is set to Demand. The default start type is Auto.
The ImagePath of WinDefend service is OK.
The ServiceDll of WinDefend service is OK.
Windows Defender Disabled Policy:
==========================
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender]
"DisableAntiSpyware"=DWORD:1
Other Services:
==============
File Check:
========
C:\Windows\System32\nsisvc.dll => MD5 is legit
C:\Windows\System32\drivers\nsiproxy.sys => MD5 is legit
C:\Windows\System32\dhcpcore.dll => MD5 is legit
C:\Windows\System32\drivers\afd.sys => MD5 is legit
C:\Windows\System32\drivers\tdx.sys => MD5 is legit
C:\Windows\System32\Drivers\tcpip.sys => MD5 is legit
C:\Windows\System32\dnsrslvr.dll => MD5 is legit
C:\Windows\System32\mpssvc.dll => MD5 is legit
C:\Windows\System32\bfe.dll => MD5 is legit
C:\Windows\System32\drivers\mpsdrv.sys => MD5 is legit
C:\Windows\System32\SDRSVC.dll => MD5 is legit
C:\Windows\System32\vssvc.exe => MD5 is legit
C:\Windows\System32\wscsvc.dll => MD5 is legit
C:\Windows\System32\wbem\WMIsvc.dll => MD5 is legit
C:\Windows\System32\wuaueng.dll => MD5 is legit
C:\Windows\System32\qmgr.dll => MD5 is legit
C:\Windows\System32\es.dll => MD5 is legit
C:\Windows\System32\cryptsvc.dll => MD5 is legit
C:\Program Files\Windows Defender\MpSvc.dll => MD5 is legit
C:\Windows\System32\svchost.exe => MD5 is legit
C:\Windows\System32\rpcss.dll => MD5 is legit
**** End of log ****
This is what sigverify looks like in Advanced menu. I'll hit start and see what happens but the option you described didn't appear there.
Farbar Service Scanner Version: 16-01-2013
Ran by Justin Sidwell (administrator) on 16-01-2013 at 07:25:47
Running from "C:\Users\Justin Sidwell\Desktop"
Windows 7 Professional Service Pack 1 (X64)
Boot Mode: Normal
****************************************************************
Internet Services:
============
Connection Status:
==============
Localhost is accessible.
LAN connected.
Attempt to access Google IP returned error. Google IP is offline
Google.com is accessible.
Yahoo IP is accessible.
Yahoo.com is accessible.
Windows Firewall:
=============
Firewall Disabled Policy:
==================
System Restore:
============
System Restore Disabled Policy:
========================
Action Center:
============
Windows Update:
============
Windows Autoupdate Disabled Policy:
============================
Windows Defender:
==============
WinDefend Service is not running. Checking service configuration:
The start type of WinDefend service is set to Demand. The default start type is Auto.
The ImagePath of WinDefend service is OK.
The ServiceDll of WinDefend service is OK.
Windows Defender Disabled Policy:
==========================
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender]
"DisableAntiSpyware"=DWORD:1
Other Services:
==============
File Check:
========
C:\Windows\System32\nsisvc.dll => MD5 is legit
C:\Windows\System32\drivers\nsiproxy.sys => MD5 is legit
C:\Windows\System32\dhcpcore.dll => MD5 is legit
C:\Windows\System32\drivers\afd.sys => MD5 is legit
C:\Windows\System32\drivers\tdx.sys => MD5 is legit
C:\Windows\System32\Drivers\tcpip.sys => MD5 is legit
C:\Windows\System32\dnsrslvr.dll => MD5 is legit
C:\Windows\System32\mpssvc.dll => MD5 is legit
C:\Windows\System32\bfe.dll => MD5 is legit
C:\Windows\System32\drivers\mpsdrv.sys => MD5 is legit
C:\Windows\System32\SDRSVC.dll => MD5 is legit
C:\Windows\System32\vssvc.exe => MD5 is legit
C:\Windows\System32\wscsvc.dll => MD5 is legit
C:\Windows\System32\wbem\WMIsvc.dll => MD5 is legit
C:\Windows\System32\wuaueng.dll => MD5 is legit
C:\Windows\System32\qmgr.dll => MD5 is legit
C:\Windows\System32\es.dll => MD5 is legit
C:\Windows\System32\cryptsvc.dll => MD5 is legit
C:\Program Files\Windows Defender\MpSvc.dll => MD5 is legit
C:\Windows\System32\svchost.exe => MD5 is legit
C:\Windows\System32\rpcss.dll => MD5 is legit
**** End of log ****
This is what sigverify looks like in Advanced menu. I'll hit start and see what happens but the option you described didn't appear there.

TrunkMonkey
Posts: 73 +0
TrunkMonkey
Posts: 73 +0
Malwarebytes Anti-Rootkit BETA 1.01.0.1016
www.malwarebytes.org
Database version: v2013.01.16.03
Windows 7 Service Pack 1 x64 NTFS
Internet Explorer 10.0.9200.16439
Justin Sidwell :: TOWEROFPOWER10 [administrator]
1/16/2013 8:09:33 AM
mbar-log-2013-01-16 (08-09-33).txt
Scan type: Quick scan
Scan options enabled: Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken | PUP | PUM | P2P
Scan options disabled:
Objects scanned: 27839
Time elapsed: 4 minute(s), 43 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 0
(No malicious items detected)
Registry Values Detected: 0
(No malicious items detected)
Registry Data Items Detected: 0
(No malicious items detected)
Folders Detected: 0
(No malicious items detected)
Files Detected: 0
(No malicious items detected)
(end)
Clean scan. but I don't buy it. There's folders appearing in user folders, icons disappearing from folders. We have our friend CSRSS.EXE hanging out with no user of group associated with it.
Winlogon.exe is also there, and has no username or description either.
Ive started using FireFox, as IE lost it's icon and was acting suspicious. Checked my Google account and there was a login in United Kingdom. I have emails going to my gmail with my name as the sender, for porn sites. So I turned on two step verification and changed my password all from my phone, in case they're watching from my pc. Paranoia will destroya, so true
TrunkMonkey
Posts: 73 +0
Jay Pfoutz
Posts: 4,279 +49
We'll have to keep looking here...Nothing too bad yet. Maybe a bit suspicious...what an adventure...
Here's one of my tools to use (I rarely use them, unless very necessary):
SpiderKill Rootkit Scanner
Please download SpiderKill by DragonMaster Jay and save it to your Desktop.
We'll see how things get past ActiveScan...
Please run Panda ActiveScan online scan.
Here's one of my tools to use (I rarely use them, unless very necessary):
SpiderKill Rootkit Scanner
Please download SpiderKill by DragonMaster Jay and save it to your Desktop.
- Right-click on SpiderKill.zip and click Extract All. Follow the prompts and read carefully, to save it to your Desktop.
- Double-click on the SpiderKill folder, and then double-click on SpiderKill.bat and follow all the prompts in the program.
- Within a minute, it will save its log titled SpiderKill.txt. Please post that in your next reply. You may have to use two or three posts to be able to fit the information in.
We'll see how things get past ActiveScan...
Please run Panda ActiveScan online scan.
- Choose Quick Scan then click the big green Scan now button
- If it wants to install an ActiveX component allow it
- It will start downloading the files it requires for the scan (Note: It may take a couple of minutes)
- Once the scan is completed, please hit the notepad icon next to the text Export to:
- Save it to a convenient location such as your Desktop
- Post the contents of the ActiveScan.txt in your next reply
TrunkMonkey
Posts: 73 +0
Quick FYI, I'm only closing browsers down prior to launching these tools if you say so in the instructions.
SpiderKill by DragonMaster Jay
Microsoft Windows [Version 6.1.7601]
********************Drivers list********************
Volume in drive C has no label.
Volume Serial Number is B2C6-174C
Directory of C:\Windows\System32\Drivers
01/16/2013 08:56 AM <DIR> .
01/16/2013 08:56 AM <DIR> ..
07/13/2009 06:06 PM 68,096 1394bus.sys
11/20/2010 04:44 AM 229,888 1394ohci.sys
11/20/2010 07:32 AM 334,208 acpi.sys
11/20/2010 03:30 AM 12,800 acpipmi.sys
07/13/2009 07:52 PM 491,088 adp94xx.sys
07/13/2009 07:52 PM 339,536 adpahci.sys
07/13/2009 07:52 PM 182,864 adpu320.sys
12/27/2011 09:59 PM 498,688 afd.sys
07/13/2009 06:10 PM 60,416 agilevpn.sys
07/13/2009 07:52 PM 61,008 AGP440.sys
07/13/2009 07:52 PM 15,440 aliide.sys
07/13/2009 07:52 PM 15,440 amdide.sys
07/13/2009 05:19 PM 64,512 amdk8.sys
07/13/2009 05:19 PM 60,928 amdppm.sys
01/14/2013 07:00 AM 70,200 amdsata.sys
07/13/2009 07:52 PM 194,128 amdsbs.sys
01/14/2013 07:00 AM 28,728 amdxata.sys
04/10/2012 07:40 PM 82,560 amd_sata.sys
04/10/2012 07:40 PM 42,624 amd_xata.sys
11/20/2010 04:14 AM 61,440 appid.sys
07/13/2009 07:52 PM 87,632 arc.sys
07/13/2009 07:52 PM 97,856 arcsas.sys
07/15/2009 09:38 PM 15,416 ASACPI.sys
07/13/2009 06:10 PM 23,040 asyncmac.sys
07/13/2009 07:52 PM 24,128 atapi.sys
11/20/2010 07:32 AM 155,520 ataport.sys
09/27/2012 07:09 PM 53,248 ati2erec.dll
05/14/2012 12:12 AM 96,896 AtihdW76.sys
09/27/2012 08:21 PM 10,697,216 atikmdag.sys
09/27/2012 07:12 PM 460,288 atikmpag.sys
01/14/2013 07:00 AM 16,440 AtiPcie.sys
06/10/2009 02:34 PM 270,848 b57nd60a.sys
07/13/2009 07:52 PM 28,240 battc.sys
07/13/2009 06:00 PM 6,656 beep.sys
07/13/2009 05:35 PM 45,056 blbdrive.sys
02/22/2011 10:55 PM 90,624 bowser.sys
06/10/2009 02:41 PM 18,432 BrFiltLo.sys
06/10/2009 02:41 PM 8,704 BrFiltUp.sys
07/13/2009 07:01 PM 95,232 bridge.sys
07/13/2009 07:19 PM 286,720 BrSerId.sys
06/10/2009 02:41 PM 47,104 BrSerWdm.sys
06/10/2009 02:41 PM 14,976 BrUsbMdm.sys
06/10/2009 02:41 PM 14,720 BrUsbSer.sys
07/13/2009 06:06 PM 72,192 bthmodem.sys
06/10/2009 02:34 PM 468,480 bxvbda.sys
07/13/2009 05:19 PM 92,160 cdfs.sys
11/20/2010 03:19 AM 147,456 cdrom.sys
07/13/2009 06:06 PM 45,568 circlass.sys
11/20/2010 07:32 AM 179,072 Classpnp.sys
07/13/2009 05:31 PM 17,664 CmBatt.sys
07/13/2009 07:52 PM 17,488 cmdide.sys
08/24/2012 12:09 PM 458,712 cng.sys
07/13/2009 07:52 PM 21,584 compbatt.sys
11/20/2010 04:33 AM 38,912 CompositeBus.sys
07/13/2009 07:47 PM 39,504 crashdmp.sys
07/13/2009 07:47 PM 24,144 crcdisk.sys
11/20/2010 03:27 AM 514,560 csc.sys
11/20/2010 03:26 AM 102,400 dfsc.sys
07/13/2009 05:37 PM 40,448 discache.sys
07/13/2009 07:47 PM 73,280 disk.sys
04/22/2011 04:15 PM 27,520 Diskdump.sys
07/13/2009 07:01 PM 116,224 drmk.sys
07/13/2009 06:06 PM 5,632 drmkaud.sys
07/13/2009 07:47 PM 28,736 Dumpata.sys
07/13/2009 07:43 PM 55,128 dumpfve.sys
07/13/2009 05:38 PM 16,896 dxapi.sys
07/13/2009 05:38 PM 98,816 dxg.sys
11/20/2010 07:33 AM 982,912 dxgkrnl.sys
11/20/2010 03:49 AM 258,048 dxgmms1.sys
07/13/2009 07:47 PM 530,496 elxstor.sys
01/16/2013 06:06 AM <DIR> en-US
07/13/2009 05:31 PM 9,728 errdev.sys
01/16/2013 06:07 AM <DIR> etc
06/10/2009 02:34 PM 3,286,016 evbda.sys
07/13/2009 05:23 PM 195,072 exfat.sys
07/13/2009 05:23 PM 204,800 fastfat.sys
07/13/2009 06:00 PM 29,696 fdc.sys
07/13/2009 07:47 PM 70,224 fileinfo.sys
07/13/2009 05:25 PM 34,304 filetrace.sys
07/13/2009 06:00 PM 24,576 flpydisk.sys
11/20/2010 07:33 AM 289,664 fltMgr.sys
07/13/2009 07:47 PM 55,376 fsdepends.sys
03/01/2012 12:46 AM 23,408 fs_rec.sys
11/20/2010 07:28 AM 223,248 fvevol.sys
08/22/2012 12:12 PM 288,624 FWPKCLNT.SYS
07/13/2009 07:47 PM 65,088 GAGP30KX.SYS
06/10/2009 02:30 PM 3,440,660 gm.dls
06/10/2009 02:30 PM 646 gmreadme.txt
06/10/2009 02:31 PM 31,232 hcw85cir.sys
11/20/2010 04:43 AM 122,368 hdaudbus.sys
11/20/2010 04:44 AM 350,208 HdAudio.sys
07/13/2009 05:31 PM 26,624 hidbatt.sys
07/13/2009 06:06 PM 100,864 hidbth.sys
11/20/2010 04:43 AM 76,800 hidclass.sys
07/13/2009 06:06 PM 46,592 hidir.sys
07/13/2009 06:06 PM 32,896 hidparse.sys
11/20/2010 04:43 AM 30,208 hidusb.sys
11/20/2010 07:33 AM 78,720 HpSAMD.sys
11/20/2010 03:25 AM 753,664 http.sys
11/20/2010 07:33 AM 14,720 hwpolicy.sys
07/13/2009 05:19 PM 105,472 i8042prt.sys
03/11/2011 12:41 AM 410,496 iaStorV.sys
07/13/2009 07:48 PM 44,112 iirsp.sys
07/13/2009 07:48 PM 16,960 intelide.sys
07/13/2009 05:19 PM 62,464 intelppm.sys
11/20/2010 04:52 AM 82,944 ipfltdrv.sys
11/20/2010 04:04 AM 78,848 IPMIDrv.sys
07/13/2009 06:10 PM 116,224 ipnat.sys
07/13/2009 06:09 PM 120,320 irda.sys
07/13/2009 06:08 PM 17,920 irenum.sys
07/13/2009 07:48 PM 20,544 isapnp.sys
01/06/2013 11:04 PM 123,704 jraid.sys
07/13/2009 07:48 PM 50,768 kbdclass.sys
11/20/2010 04:33 AM 33,280 kbdhid.sys
11/20/2010 04:33 AM 243,712 ks.sys
06/01/2012 11:48 PM 95,600 ksecdd.sys
08/24/2012 12:13 PM 154,480 ksecpkg.sys
07/13/2009 06:00 PM 20,992 ksthunk.sys
07/13/2009 06:08 PM 60,928 lltdio.sys
07/13/2009 07:48 PM 114,752 lsi_fc.sys
07/13/2009 07:48 PM 106,560 lsi_sas.sys
07/13/2009 07:48 PM 65,600 lsi_sas2.sys
07/13/2009 07:48 PM 115,776 lsi_scsi.sys
07/13/2009 05:26 PM 113,152 luafv.sys
01/17/2008 04:51 PM 18,816 Lycosa.sys
12/14/2012 04:49 PM 24,176 mbam.sys
07/13/2009 06:01 PM 22,016 mcd.sys
07/13/2009 07:48 PM 35,392 megasas.sys
07/13/2009 07:48 PM 284,736 MegaSR.sys
07/13/2009 06:10 PM 40,448 modem.sys
07/13/2009 05:38 PM 30,208 monitor.sys
07/13/2009 07:48 PM 49,216 mouclass.sys
07/13/2009 06:00 PM 31,232 mouhid.sys
11/20/2010 07:33 AM 94,592 mountmgr.sys
08/30/2012 10:03 PM 228,768 MpFilter.sys
11/20/2010 07:33 AM 155,008 mpio.sys
07/13/2009 06:08 PM 77,312 mpsdrv.sys
11/20/2010 03:26 AM 140,800 mrxdav.sys
04/26/2011 08:40 PM 158,208 mrxsmb.sys
07/08/2011 08:46 PM 288,768 mrxsmb10.sys
04/26/2011 08:39 PM 128,000 mrxsmb20.sys
11/20/2010 07:33 AM 31,104 msahci.sys
11/20/2010 07:33 AM 140,672 msdsm.sys
07/13/2009 05:19 PM 26,112 msfs.sys
06/02/2012 08:35 AM 3 MsftWdf_Kernel_01011_Inbox_Critical.Wdf
06/02/2012 08:57 AM 3 MsftWdf_User_01_11_00_Inbox_Critical.Wdf
07/13/2009 06:06 PM 8,192 mshidkmdf.sys
07/13/2009 07:48 PM 15,424 msisadrv.sys
11/20/2010 07:33 AM 273,792 msiscsi.sys
07/13/2009 06:00 PM 11,136 mskssrv.sys
07/13/2009 06:00 PM 7,168 mspclock.sys
07/13/2009 06:00 PM 6,784 mspqm.sys
11/20/2010 07:33 AM 366,976 msrpc.sys
07/13/2009 07:48 PM 32,320 mssmbios.sys
07/13/2009 06:00 PM 8,064 mstee.sys
07/13/2009 06:02 PM 15,360 MTConfig.sys
07/13/2009 07:48 PM 60,496 mup.sys
08/22/2012 12:12 PM 950,128 ndis.sys
07/13/2009 06:08 PM 35,328 ndiscap.sys
07/13/2009 06:10 PM 24,064 ndistapi.sys
11/20/2010 04:50 AM 56,832 ndisuio.sys
11/20/2010 04:52 AM 164,352 ndiswan.sys
11/20/2010 04:52 AM 57,856 ndproxy.sys
07/13/2009 06:09 PM 44,544 netbios.sys
11/20/2010 03:23 AM 261,632 netbt.sys
08/22/2012 12:12 PM 376,688 netio.sys
07/13/2009 07:48 PM 51,264 nfrd960.sys
08/30/2012 10:03 PM 128,456 NisDrvWFP.sys
07/13/2009 05:19 PM 44,032 npfs.sys
07/13/2009 05:21 PM 24,576 nsiproxy.sys
08/31/2012 12:19 PM 1,659,760 ntfs.sys
07/13/2009 05:19 PM 6,144 null.sys
SpiderKill by DragonMaster Jay
Microsoft Windows [Version 6.1.7601]
********************Drivers list********************
Volume in drive C has no label.
Volume Serial Number is B2C6-174C
Directory of C:\Windows\System32\Drivers
01/16/2013 08:56 AM <DIR> .
01/16/2013 08:56 AM <DIR> ..
07/13/2009 06:06 PM 68,096 1394bus.sys
11/20/2010 04:44 AM 229,888 1394ohci.sys
11/20/2010 07:32 AM 334,208 acpi.sys
11/20/2010 03:30 AM 12,800 acpipmi.sys
07/13/2009 07:52 PM 491,088 adp94xx.sys
07/13/2009 07:52 PM 339,536 adpahci.sys
07/13/2009 07:52 PM 182,864 adpu320.sys
12/27/2011 09:59 PM 498,688 afd.sys
07/13/2009 06:10 PM 60,416 agilevpn.sys
07/13/2009 07:52 PM 61,008 AGP440.sys
07/13/2009 07:52 PM 15,440 aliide.sys
07/13/2009 07:52 PM 15,440 amdide.sys
07/13/2009 05:19 PM 64,512 amdk8.sys
07/13/2009 05:19 PM 60,928 amdppm.sys
01/14/2013 07:00 AM 70,200 amdsata.sys
07/13/2009 07:52 PM 194,128 amdsbs.sys
01/14/2013 07:00 AM 28,728 amdxata.sys
04/10/2012 07:40 PM 82,560 amd_sata.sys
04/10/2012 07:40 PM 42,624 amd_xata.sys
11/20/2010 04:14 AM 61,440 appid.sys
07/13/2009 07:52 PM 87,632 arc.sys
07/13/2009 07:52 PM 97,856 arcsas.sys
07/15/2009 09:38 PM 15,416 ASACPI.sys
07/13/2009 06:10 PM 23,040 asyncmac.sys
07/13/2009 07:52 PM 24,128 atapi.sys
11/20/2010 07:32 AM 155,520 ataport.sys
09/27/2012 07:09 PM 53,248 ati2erec.dll
05/14/2012 12:12 AM 96,896 AtihdW76.sys
09/27/2012 08:21 PM 10,697,216 atikmdag.sys
09/27/2012 07:12 PM 460,288 atikmpag.sys
01/14/2013 07:00 AM 16,440 AtiPcie.sys
06/10/2009 02:34 PM 270,848 b57nd60a.sys
07/13/2009 07:52 PM 28,240 battc.sys
07/13/2009 06:00 PM 6,656 beep.sys
07/13/2009 05:35 PM 45,056 blbdrive.sys
02/22/2011 10:55 PM 90,624 bowser.sys
06/10/2009 02:41 PM 18,432 BrFiltLo.sys
06/10/2009 02:41 PM 8,704 BrFiltUp.sys
07/13/2009 07:01 PM 95,232 bridge.sys
07/13/2009 07:19 PM 286,720 BrSerId.sys
06/10/2009 02:41 PM 47,104 BrSerWdm.sys
06/10/2009 02:41 PM 14,976 BrUsbMdm.sys
06/10/2009 02:41 PM 14,720 BrUsbSer.sys
07/13/2009 06:06 PM 72,192 bthmodem.sys
06/10/2009 02:34 PM 468,480 bxvbda.sys
07/13/2009 05:19 PM 92,160 cdfs.sys
11/20/2010 03:19 AM 147,456 cdrom.sys
07/13/2009 06:06 PM 45,568 circlass.sys
11/20/2010 07:32 AM 179,072 Classpnp.sys
07/13/2009 05:31 PM 17,664 CmBatt.sys
07/13/2009 07:52 PM 17,488 cmdide.sys
08/24/2012 12:09 PM 458,712 cng.sys
07/13/2009 07:52 PM 21,584 compbatt.sys
11/20/2010 04:33 AM 38,912 CompositeBus.sys
07/13/2009 07:47 PM 39,504 crashdmp.sys
07/13/2009 07:47 PM 24,144 crcdisk.sys
11/20/2010 03:27 AM 514,560 csc.sys
11/20/2010 03:26 AM 102,400 dfsc.sys
07/13/2009 05:37 PM 40,448 discache.sys
07/13/2009 07:47 PM 73,280 disk.sys
04/22/2011 04:15 PM 27,520 Diskdump.sys
07/13/2009 07:01 PM 116,224 drmk.sys
07/13/2009 06:06 PM 5,632 drmkaud.sys
07/13/2009 07:47 PM 28,736 Dumpata.sys
07/13/2009 07:43 PM 55,128 dumpfve.sys
07/13/2009 05:38 PM 16,896 dxapi.sys
07/13/2009 05:38 PM 98,816 dxg.sys
11/20/2010 07:33 AM 982,912 dxgkrnl.sys
11/20/2010 03:49 AM 258,048 dxgmms1.sys
07/13/2009 07:47 PM 530,496 elxstor.sys
01/16/2013 06:06 AM <DIR> en-US
07/13/2009 05:31 PM 9,728 errdev.sys
01/16/2013 06:07 AM <DIR> etc
06/10/2009 02:34 PM 3,286,016 evbda.sys
07/13/2009 05:23 PM 195,072 exfat.sys
07/13/2009 05:23 PM 204,800 fastfat.sys
07/13/2009 06:00 PM 29,696 fdc.sys
07/13/2009 07:47 PM 70,224 fileinfo.sys
07/13/2009 05:25 PM 34,304 filetrace.sys
07/13/2009 06:00 PM 24,576 flpydisk.sys
11/20/2010 07:33 AM 289,664 fltMgr.sys
07/13/2009 07:47 PM 55,376 fsdepends.sys
03/01/2012 12:46 AM 23,408 fs_rec.sys
11/20/2010 07:28 AM 223,248 fvevol.sys
08/22/2012 12:12 PM 288,624 FWPKCLNT.SYS
07/13/2009 07:47 PM 65,088 GAGP30KX.SYS
06/10/2009 02:30 PM 3,440,660 gm.dls
06/10/2009 02:30 PM 646 gmreadme.txt
06/10/2009 02:31 PM 31,232 hcw85cir.sys
11/20/2010 04:43 AM 122,368 hdaudbus.sys
11/20/2010 04:44 AM 350,208 HdAudio.sys
07/13/2009 05:31 PM 26,624 hidbatt.sys
07/13/2009 06:06 PM 100,864 hidbth.sys
11/20/2010 04:43 AM 76,800 hidclass.sys
07/13/2009 06:06 PM 46,592 hidir.sys
07/13/2009 06:06 PM 32,896 hidparse.sys
11/20/2010 04:43 AM 30,208 hidusb.sys
11/20/2010 07:33 AM 78,720 HpSAMD.sys
11/20/2010 03:25 AM 753,664 http.sys
11/20/2010 07:33 AM 14,720 hwpolicy.sys
07/13/2009 05:19 PM 105,472 i8042prt.sys
03/11/2011 12:41 AM 410,496 iaStorV.sys
07/13/2009 07:48 PM 44,112 iirsp.sys
07/13/2009 07:48 PM 16,960 intelide.sys
07/13/2009 05:19 PM 62,464 intelppm.sys
11/20/2010 04:52 AM 82,944 ipfltdrv.sys
11/20/2010 04:04 AM 78,848 IPMIDrv.sys
07/13/2009 06:10 PM 116,224 ipnat.sys
07/13/2009 06:09 PM 120,320 irda.sys
07/13/2009 06:08 PM 17,920 irenum.sys
07/13/2009 07:48 PM 20,544 isapnp.sys
01/06/2013 11:04 PM 123,704 jraid.sys
07/13/2009 07:48 PM 50,768 kbdclass.sys
11/20/2010 04:33 AM 33,280 kbdhid.sys
11/20/2010 04:33 AM 243,712 ks.sys
06/01/2012 11:48 PM 95,600 ksecdd.sys
08/24/2012 12:13 PM 154,480 ksecpkg.sys
07/13/2009 06:00 PM 20,992 ksthunk.sys
07/13/2009 06:08 PM 60,928 lltdio.sys
07/13/2009 07:48 PM 114,752 lsi_fc.sys
07/13/2009 07:48 PM 106,560 lsi_sas.sys
07/13/2009 07:48 PM 65,600 lsi_sas2.sys
07/13/2009 07:48 PM 115,776 lsi_scsi.sys
07/13/2009 05:26 PM 113,152 luafv.sys
01/17/2008 04:51 PM 18,816 Lycosa.sys
12/14/2012 04:49 PM 24,176 mbam.sys
07/13/2009 06:01 PM 22,016 mcd.sys
07/13/2009 07:48 PM 35,392 megasas.sys
07/13/2009 07:48 PM 284,736 MegaSR.sys
07/13/2009 06:10 PM 40,448 modem.sys
07/13/2009 05:38 PM 30,208 monitor.sys
07/13/2009 07:48 PM 49,216 mouclass.sys
07/13/2009 06:00 PM 31,232 mouhid.sys
11/20/2010 07:33 AM 94,592 mountmgr.sys
08/30/2012 10:03 PM 228,768 MpFilter.sys
11/20/2010 07:33 AM 155,008 mpio.sys
07/13/2009 06:08 PM 77,312 mpsdrv.sys
11/20/2010 03:26 AM 140,800 mrxdav.sys
04/26/2011 08:40 PM 158,208 mrxsmb.sys
07/08/2011 08:46 PM 288,768 mrxsmb10.sys
04/26/2011 08:39 PM 128,000 mrxsmb20.sys
11/20/2010 07:33 AM 31,104 msahci.sys
11/20/2010 07:33 AM 140,672 msdsm.sys
07/13/2009 05:19 PM 26,112 msfs.sys
06/02/2012 08:35 AM 3 MsftWdf_Kernel_01011_Inbox_Critical.Wdf
06/02/2012 08:57 AM 3 MsftWdf_User_01_11_00_Inbox_Critical.Wdf
07/13/2009 06:06 PM 8,192 mshidkmdf.sys
07/13/2009 07:48 PM 15,424 msisadrv.sys
11/20/2010 07:33 AM 273,792 msiscsi.sys
07/13/2009 06:00 PM 11,136 mskssrv.sys
07/13/2009 06:00 PM 7,168 mspclock.sys
07/13/2009 06:00 PM 6,784 mspqm.sys
11/20/2010 07:33 AM 366,976 msrpc.sys
07/13/2009 07:48 PM 32,320 mssmbios.sys
07/13/2009 06:00 PM 8,064 mstee.sys
07/13/2009 06:02 PM 15,360 MTConfig.sys
07/13/2009 07:48 PM 60,496 mup.sys
08/22/2012 12:12 PM 950,128 ndis.sys
07/13/2009 06:08 PM 35,328 ndiscap.sys
07/13/2009 06:10 PM 24,064 ndistapi.sys
11/20/2010 04:50 AM 56,832 ndisuio.sys
11/20/2010 04:52 AM 164,352 ndiswan.sys
11/20/2010 04:52 AM 57,856 ndproxy.sys
07/13/2009 06:09 PM 44,544 netbios.sys
11/20/2010 03:23 AM 261,632 netbt.sys
08/22/2012 12:12 PM 376,688 netio.sys
07/13/2009 07:48 PM 51,264 nfrd960.sys
08/30/2012 10:03 PM 128,456 NisDrvWFP.sys
07/13/2009 05:19 PM 44,032 npfs.sys
07/13/2009 05:21 PM 24,576 nsiproxy.sys
08/31/2012 12:19 PM 1,659,760 ntfs.sys
07/13/2009 05:19 PM 6,144 null.sys
TrunkMonkey
Posts: 73 +0
continued...
03/11/2011 12:41 AM 148,352 nvraid.sys
03/11/2011 12:41 AM 166,272 nvstor.sys
07/13/2009 07:48 PM 122,960 NV_AGP.SYS
07/13/2009 06:07 PM 318,976 nwifi.sys
07/13/2009 06:06 PM 72,832 ohci1394.sys
11/20/2010 04:52 AM 131,584 pacer.sys
07/13/2009 06:00 PM 97,280 parport.sys
03/17/2012 01:58 AM 75,120 partmgr.sys
11/20/2010 07:33 AM 184,704 pci.sys
07/13/2009 07:45 PM 12,352 pciide.sys
07/13/2009 07:45 PM 48,720 pciidex.sys
07/13/2009 07:45 PM 220,752 pcmcia.sys
07/13/2009 07:45 PM 50,768 pcw.sys
07/13/2009 07:01 PM 651,264 PEAuth.sys
07/13/2009 06:06 PM 230,400 portcls.sys
07/13/2009 05:19 PM 60,416 processr.sys
07/13/2009 07:45 PM 1,524,816 ql2300.sys
07/13/2009 07:45 PM 128,592 ql40xx.sys
07/13/2009 06:09 PM 46,592 qwavedrv.sys
07/13/2009 06:10 PM 14,848 rasacd.sys
11/20/2010 04:52 AM 129,536 rasl2tp.sys
07/13/2009 06:10 PM 92,672 raspppoe.sys
11/20/2010 04:52 AM 111,104 raspptp.sys
07/13/2009 06:10 PM 83,968 rassstp.sys
11/20/2010 03:27 AM 309,248 rdbss.sys
07/13/2009 06:17 PM 24,064 rdpbus.sys
07/13/2009 06:16 PM 7,680 RDPCDD.sys
11/20/2010 05:06 AM 165,888 rdpdr.sys
07/13/2009 06:16 PM 7,680 RDPENCDD.sys
07/13/2009 06:16 PM 8,192 RDPREFMP.sys
08/23/2012 08:10 AM 19,456 rdpvideominiport.sys
04/27/2012 09:55 PM 210,944 rdpwd.sys
11/20/2010 07:33 AM 213,888 rdyboost.sys
11/20/2010 04:49 AM 146,432 rmcast.sys
07/04/2012 02:26 PM 41,472 RNDISMP.sys
07/13/2009 06:10 PM 11,264 rootmdm.sys
07/13/2009 06:08 PM 76,800 rspndr.sys
06/10/2011 06:34 AM 539,240 Rt64win7.sys
11/20/2010 07:33 AM 103,808 sbp2port.sys
11/20/2010 04:09 AM 29,696 scfilter.sys
11/20/2010 07:33 AM 171,392 scsiport.sys
06/10/2009 02:37 PM 23,040 secdrv.sys
07/13/2009 06:00 PM 23,552 serenum.sys
07/13/2009 06:00 PM 94,208 serial.sys
07/13/2009 06:00 PM 26,624 sermouse.sys
07/13/2009 06:01 PM 14,336 sffdisk.sys
07/13/2009 06:01 PM 13,824 sffp_mmc.sys
11/20/2010 04:34 AM 14,336 sffp_sd.sys
07/13/2009 06:01 PM 16,896 sfloppy.sys
07/13/2009 07:45 PM 43,584 sisraid2.sys
07/13/2009 07:45 PM 80,464 sisraid4.sys
07/13/2009 06:09 PM 93,184 smb.sys
07/13/2009 06:00 PM 20,992 smclib.sys
07/13/2009 07:45 PM 19,008 spldr.sys
06/10/2009 02:48 PM 426,496 spsys.sys
04/28/2011 09:06 PM 467,456 srv.sys
04/28/2011 09:05 PM 410,112 srv2.sys
04/28/2011 09:05 PM 168,448 srvnet.sys
07/13/2009 07:45 PM 24,656 stexstor.sys
03/11/2011 12:41 AM 189,824 storport.sys
11/20/2010 07:34 AM 34,688 storvsc.sys
07/13/2009 06:06 PM 68,864 stream.sys
07/13/2009 07:45 PM 12,496 swenum.sys
07/13/2009 06:01 PM 29,184 tape.sys
10/03/2012 11:56 AM 1,914,248 tcpip.sys
10/03/2012 10:07 AM 45,568 tcpipreg.sys
11/20/2010 03:22 AM 26,624 tdi.sys
07/13/2009 06:16 PM 15,872 tdpipe.sys
02/16/2012 10:57 PM 23,552 tdtcp.sys
11/20/2010 03:21 AM 119,296 tdx.sys
11/20/2010 07:33 AM 63,360 termdd.sys
11/20/2010 05:04 AM 39,424 tssecsrv.sys
08/23/2012 08:07 AM 57,856 TsUsbFlt.sys
11/20/2010 04:51 AM 125,440 tunnel.sys
07/13/2009 07:45 PM 64,080 UAGP35.SYS
11/20/2010 03:26 AM 328,192 udfs.sys
07/13/2009 07:45 PM 64,592 ULIAGPKX.SYS
11/20/2010 04:44 AM 48,640 umbus.sys
01/16/2013 06:02 AM <DIR> UMDF
07/13/2009 06:06 PM 9,728 umpass.sys
07/13/2009 06:09 PM 19,968 usb8023.sys
11/20/2010 04:44 AM 32,896 USBCAMD2.sys
03/24/2011 09:29 PM 98,816 usbccgp.sys
07/13/2009 06:06 PM 100,352 usbcir.sys
03/24/2011 09:28 PM 7,936 usbd.sys
03/24/2011 09:29 PM 52,736 usbehci.sys
08/28/2012 06:27 AM 58,536 usbfilter.sys
03/24/2011 09:29 PM 343,040 usbhub.sys
03/24/2011 09:29 PM 25,600 usbohci.sys
03/24/2011 09:29 PM 325,120 usbport.sys
07/13/2009 06:38 PM 25,088 usbprint.sys
11/20/2010 05:37 AM 31,744 usbrpm.sys
03/10/2011 10:37 PM 91,648 USBSTOR.SYS
03/24/2011 09:29 PM 30,720 usbuhci.sys
07/13/2009 07:45 PM 36,432 vdrvroot.sys
07/13/2009 05:38 PM 29,184 vga.sys
07/13/2009 05:38 PM 29,184 vgapnp.sys
11/20/2010 07:34 AM 215,936 vhdmp.sys
01/14/2013 07:14 AM 1,301,504 viahduaa.sys
07/13/2009 07:45 PM 17,488 viaide.sys
07/13/2009 05:38 PM 129,024 videoprt.sys
11/20/2010 07:34 AM 199,552 vmbus.sys
11/20/2010 03:57 AM 21,760 VMBusHID.sys
11/20/2010 03:57 AM 6,656 vms3cap.sys
11/20/2010 07:34 AM 46,464 vmstorfl.sys
11/20/2010 07:34 AM 71,552 volmgr.sys
11/20/2010 07:34 AM 363,392 volmgrx.sys
11/20/2010 07:34 AM 295,808 volsnap.sys
07/13/2009 07:45 PM 161,872 vsmraid.sys
07/13/2009 06:07 PM 24,576 vwifibus.sys
07/13/2009 06:07 PM 59,904 vwififlt.sys
07/13/2009 06:07 PM 17,920 vwifimp.sys
07/13/2009 06:02 PM 27,776 wacompen.sys
11/20/2010 04:52 AM 88,576 wanarp.sys
07/13/2009 05:37 PM 42,496 watchdog.sys
07/13/2009 07:45 PM 21,056 wd.sys
07/25/2012 10:55 PM 785,512 Wdf01000.sys
07/25/2012 10:55 PM 54,376 WdfLdr.sys
07/13/2009 06:09 PM 12,800 wfplwf.sys
07/13/2009 07:45 PM 22,096 wimmount.sys
11/20/2010 07:33 AM 52,096 winhv.sys
07/13/2009 05:31 PM 14,336 wmiacpi.sys
07/13/2009 07:45 PM 16,464 wmilib.sys
07/13/2009 06:10 PM 21,504 ws2ifsl.sys
07/25/2012 08:26 PM 87,040 WUDFPf.sys
07/25/2012 08:26 PM 198,656 WUDFRd.sys
295 File(s) 56,814,168 bytes
Directory of C:\Windows\System32\Drivers\en-US
01/16/2013 06:06 AM <DIR> .
01/16/2013 06:06 AM <DIR> ..
07/13/2009 08:29 PM 11,776 1394ohci.sys.mui
07/13/2009 08:23 PM 9,216 acpi.sys.mui
07/13/2009 08:30 PM 14,848 afd.sys.mui
07/13/2009 08:25 PM 2,560 AGP440.sys.mui
07/13/2009 08:25 PM 2,048 amdide.sys.mui
07/13/2009 08:28 PM 14,336 amdk8.sys.mui
07/13/2009 08:28 PM 14,336 amdppm.sys.mui
07/13/2009 08:29 PM 3,072 ataport.sys.mui
07/13/2009 08:29 PM 3,072 atikmdag.sys.mui
07/13/2009 08:27 PM 7,168 battc.sys.mui
07/13/2009 08:30 PM 25,600 bfe.dll.mui
07/13/2009 08:28 PM 2,560 BrParwdm.sys.mui
07/13/2009 08:25 PM 10,240 BrSerIb.sys.mui
07/13/2009 08:30 PM 10,240 BrSerId.sys.mui
07/13/2009 08:30 PM 2,048 bthenum.sys.mui
07/13/2009 08:27 PM 4,608 bthpan.sys.mui
07/13/2009 08:27 PM 7,680 bthport.sys.mui
07/13/2009 08:30 PM 2,560 BTHUSB.SYS.mui
07/13/2009 08:29 PM 2,048 cdrom.sys.mui
07/13/2009 08:29 PM 2,048 disk.sys.mui
07/13/2009 08:28 PM 2,560 Dot4usb.sys.mui
07/13/2009 08:23 PM 5,120 fltmgr.sys.mui
07/13/2009 08:30 PM 14,336 fvevol.sys.mui
07/13/2009 08:29 PM 2,560 GAGP30KX.SYS.mui
07/13/2009 08:28 PM 4,096 hdaudbus.sys.mui
07/13/2009 08:30 PM 3,072 HdAudio.sys.mui
07/13/2009 08:24 PM 3,072 hidbth.sys.mui
07/13/2009 08:30 PM 32,256 http.sys.mui
07/13/2009 08:29 PM 10,240 i8042prt.sys.mui
07/13/2009 08:28 PM 14,336 intelppm.sys.mui
11/20/2010 07:11 AM 6,144 IPMIDrv.sys.mui
07/13/2009 08:23 PM 3,584 ipnat.sys.mui
07/13/2009 08:30 PM 3,584 isapnp.sys.mui
11/20/2010 07:10 AM 4,608 kbdclass.sys.mui
07/13/2009 08:24 PM 2,560 kbdhid.sys.mui
07/13/2009 08:29 PM 6,144 luafv.sys.mui
07/13/2009 08:28 PM 3,584 modem.sys.mui
07/13/2009 08:26 PM 4,096 mouclass.sys.mui
07/13/2009 08:24 PM 2,560 mouhid.sys.mui
07/13/2009 08:29 PM 2,560 mountmgr.sys.mui
07/13/2009 08:27 PM 26,624 mpio.sys.mui
07/13/2009 08:29 PM 5,632 msdsm.sys.mui
07/13/2009 08:24 PM 3,072 mssmbios.sys.mui
07/13/2009 08:27 PM 2,560 MTConfig.sys.mui
07/13/2009 08:29 PM 35,328 ndis.sys.mui
07/13/2009 08:29 PM 5,632 ndiscap.sys.mui
07/13/2009 08:23 PM 3,072 ndisuio.sys.mui
07/13/2009 08:26 PM 59,904 ntfs.sys.mui
07/13/2009 08:24 PM 2,560 NV_AGP.SYS.mui
07/13/2009 08:23 PM 13,824 nwifi.sys.mui
07/13/2009 08:29 PM 11,776 ohci1394.sys.mui
07/13/2009 08:25 PM 15,360 pacer.sys.mui
07/13/2009 08:29 PM 3,584 parport.sys.mui
07/13/2009 08:29 PM 2,560 partmgr.sys.mui
07/13/2009 08:29 PM 8,192 pci.sys.mui
07/13/2009 08:28 PM 4,096 pcmcia.sys.mui
07/13/2009 08:26 PM 2,560 pnpmem.sys.mui
07/13/2009 08:23 PM 3,584 portcls.sys.mui
07/13/2009 08:29 PM 14,336 processr.sys.mui
07/13/2009 08:30 PM 3,584 pscr.sys.mui
07/13/2009 08:24 PM 2,560 qwavedrv.sys.mui
07/13/2009 08:25 PM 4,608 rdbss.sys.mui
11/20/2010 07:01 AM 2,560 rdpwd.sys.mui
07/13/2009 08:28 PM 3,072 RNDISMP.sys.mui
07/13/2009 08:25 PM 3,072 rndismp6.sys.mui
07/13/2009 08:28 PM 3,072 rndismpx.sys.mui
07/13/2009 08:30 PM 2,560 scfilter.sys.mui
07/13/2009 08:24 PM 3,072 scsiport.sys.mui
07/13/2009 08:30 PM 10,240 serial.sys.mui
07/13/2009 08:29 PM 5,120 sermouse.sys.mui
07/13/2009 08:26 PM 2,560 serscan.sys.mui
07/13/2009 08:25 PM 2,560 srv.sys.mui
07/13/2009 08:28 PM 44,032 tcpip.sys.mui
07/13/2009 08:29 PM 4,096 tpm.sys.mui
08/23/2012 09:09 AM 3,072 tsusbflt.sys.mui
07/13/2009 08:24 PM 7,680 tunnel.sys.mui
07/13/2009 08:24 PM 2,560 UAGP35.SYS.mui
07/13/2009 08:23 PM 2,560 ULIAGPKX.SYS.mui
07/13/2009 08:29 PM 3,072 umbus.sys.mui
07/13/2009 08:24 PM 11,776 usbhub.sys.mui
07/13/2009 08:26 PM 24,576 usbport.sys.mui
07/13/2009 08:24 PM 2,048 usbrpm.sys.mui
07/13/2009 08:26 PM 3,584 vdrvroot.sys.mui
07/13/2009 08:29 PM 3,584 vhdmp.sys.mui
07/13/2009 08:23 PM 2,560 volmgrx.sys.mui
07/13/2009 08:28 PM 23,552 volsnap.sys.mui
07/13/2009 08:29 PM 2,048 vwifibus.sys.mui
07/13/2009 08:27 PM 4,096 wacompen.sys.mui
07/13/2009 08:26 PM 2,048 wd.sys.mui
07/25/2012 10:47 PM 2,560 wdf01000.sys.mui
07/13/2009 08:29 PM 2,048 ws2ifsl.sys.mui
91 File(s) 707,584 bytes
Directory of C:\Windows\System32\Drivers\etc
01/16/2013 06:07 AM <DIR> .
01/16/2013 06:07 AM <DIR> ..
06/10/2009 03:00 PM 824 hosts
06/10/2009 03:00 PM 3,683 lmhosts.sam
06/10/2009 03:00 PM 407 networks
06/10/2009 03:00 PM 1,358 protocol
06/10/2009 03:00 PM 17,463 services
5 File(s) 23,735 bytes
Directory of C:\Windows\System32\Drivers\UMDF
01/16/2013 06:02 AM <DIR> .
01/16/2013 06:02 AM <DIR> ..
01/16/2013 06:06 AM <DIR> en-US
07/13/2009 07:41 PM 299,520 WpdFs.dll
1 File(s) 299,520 bytes
Directory of C:\Windows\System32\Drivers\UMDF\en-US
01/16/2013 06:06 AM <DIR> .
01/16/2013 06:06 AM <DIR> ..
07/13/2009 08:24 PM 2,560 WpdMtpDr.dll.mui
07/13/2009 08:26 PM 6,144 WUDFUsbccidDriver.dll.mui
2 File(s) 8,704 bytes
Total Files Listed:
394 File(s) 57,853,711 bytes
14 Dir(s) 1,728,493,649,920 bytes free
***********************Hidden Drivers********************
Volume in drive C has no label.
Volume Serial Number is B2C6-174C
Directory of C:\Windows\System32\Drivers
01/13/2013 02:23 AM 0 Msft_User_WpdFs_01_09_00.Wdf
1 File(s) 0 bytes
0 Dir(s) 1,728,493,658,112 bytes free
*********************Processes*******************
PROCESS PID PRIO PATH
mbamgui.exe 2664 Normal C:\Program Files (x86)\Malwarebytes' Anti-Malware\mbamgui.exe
firefox.exe 2548 Normal C:\Program Files (x86)\Mozilla Firefox\firefox.exe
plugin-container.exe 4768 Normal C:\Program Files (x86)\Mozilla Firefox\plugin-container.exe
FlashPlayerPlugin_11_5_502_146.exe 4988 Normal C:\Windows\SysWOW64\Macromed\Flash\FlashPlayerPlugin_11_5_502_146.exe
FlashPlayerPlugin_11_5_502_146.exe 1396 Normal C:\Windows\SysWOW64\Macromed\Flash\FlashPlayerPlugin_11_5_502_146.exe
processes.exe 4964 Normal C:\Users\Justin Sidwell\Desktop\SpiderKill\SpiderKill\processes.exe
*********************Modules of explorer.exe and svchost.exe*******************
******************************************
EOF
03/11/2011 12:41 AM 148,352 nvraid.sys
03/11/2011 12:41 AM 166,272 nvstor.sys
07/13/2009 07:48 PM 122,960 NV_AGP.SYS
07/13/2009 06:07 PM 318,976 nwifi.sys
07/13/2009 06:06 PM 72,832 ohci1394.sys
11/20/2010 04:52 AM 131,584 pacer.sys
07/13/2009 06:00 PM 97,280 parport.sys
03/17/2012 01:58 AM 75,120 partmgr.sys
11/20/2010 07:33 AM 184,704 pci.sys
07/13/2009 07:45 PM 12,352 pciide.sys
07/13/2009 07:45 PM 48,720 pciidex.sys
07/13/2009 07:45 PM 220,752 pcmcia.sys
07/13/2009 07:45 PM 50,768 pcw.sys
07/13/2009 07:01 PM 651,264 PEAuth.sys
07/13/2009 06:06 PM 230,400 portcls.sys
07/13/2009 05:19 PM 60,416 processr.sys
07/13/2009 07:45 PM 1,524,816 ql2300.sys
07/13/2009 07:45 PM 128,592 ql40xx.sys
07/13/2009 06:09 PM 46,592 qwavedrv.sys
07/13/2009 06:10 PM 14,848 rasacd.sys
11/20/2010 04:52 AM 129,536 rasl2tp.sys
07/13/2009 06:10 PM 92,672 raspppoe.sys
11/20/2010 04:52 AM 111,104 raspptp.sys
07/13/2009 06:10 PM 83,968 rassstp.sys
11/20/2010 03:27 AM 309,248 rdbss.sys
07/13/2009 06:17 PM 24,064 rdpbus.sys
07/13/2009 06:16 PM 7,680 RDPCDD.sys
11/20/2010 05:06 AM 165,888 rdpdr.sys
07/13/2009 06:16 PM 7,680 RDPENCDD.sys
07/13/2009 06:16 PM 8,192 RDPREFMP.sys
08/23/2012 08:10 AM 19,456 rdpvideominiport.sys
04/27/2012 09:55 PM 210,944 rdpwd.sys
11/20/2010 07:33 AM 213,888 rdyboost.sys
11/20/2010 04:49 AM 146,432 rmcast.sys
07/04/2012 02:26 PM 41,472 RNDISMP.sys
07/13/2009 06:10 PM 11,264 rootmdm.sys
07/13/2009 06:08 PM 76,800 rspndr.sys
06/10/2011 06:34 AM 539,240 Rt64win7.sys
11/20/2010 07:33 AM 103,808 sbp2port.sys
11/20/2010 04:09 AM 29,696 scfilter.sys
11/20/2010 07:33 AM 171,392 scsiport.sys
06/10/2009 02:37 PM 23,040 secdrv.sys
07/13/2009 06:00 PM 23,552 serenum.sys
07/13/2009 06:00 PM 94,208 serial.sys
07/13/2009 06:00 PM 26,624 sermouse.sys
07/13/2009 06:01 PM 14,336 sffdisk.sys
07/13/2009 06:01 PM 13,824 sffp_mmc.sys
11/20/2010 04:34 AM 14,336 sffp_sd.sys
07/13/2009 06:01 PM 16,896 sfloppy.sys
07/13/2009 07:45 PM 43,584 sisraid2.sys
07/13/2009 07:45 PM 80,464 sisraid4.sys
07/13/2009 06:09 PM 93,184 smb.sys
07/13/2009 06:00 PM 20,992 smclib.sys
07/13/2009 07:45 PM 19,008 spldr.sys
06/10/2009 02:48 PM 426,496 spsys.sys
04/28/2011 09:06 PM 467,456 srv.sys
04/28/2011 09:05 PM 410,112 srv2.sys
04/28/2011 09:05 PM 168,448 srvnet.sys
07/13/2009 07:45 PM 24,656 stexstor.sys
03/11/2011 12:41 AM 189,824 storport.sys
11/20/2010 07:34 AM 34,688 storvsc.sys
07/13/2009 06:06 PM 68,864 stream.sys
07/13/2009 07:45 PM 12,496 swenum.sys
07/13/2009 06:01 PM 29,184 tape.sys
10/03/2012 11:56 AM 1,914,248 tcpip.sys
10/03/2012 10:07 AM 45,568 tcpipreg.sys
11/20/2010 03:22 AM 26,624 tdi.sys
07/13/2009 06:16 PM 15,872 tdpipe.sys
02/16/2012 10:57 PM 23,552 tdtcp.sys
11/20/2010 03:21 AM 119,296 tdx.sys
11/20/2010 07:33 AM 63,360 termdd.sys
11/20/2010 05:04 AM 39,424 tssecsrv.sys
08/23/2012 08:07 AM 57,856 TsUsbFlt.sys
11/20/2010 04:51 AM 125,440 tunnel.sys
07/13/2009 07:45 PM 64,080 UAGP35.SYS
11/20/2010 03:26 AM 328,192 udfs.sys
07/13/2009 07:45 PM 64,592 ULIAGPKX.SYS
11/20/2010 04:44 AM 48,640 umbus.sys
01/16/2013 06:02 AM <DIR> UMDF
07/13/2009 06:06 PM 9,728 umpass.sys
07/13/2009 06:09 PM 19,968 usb8023.sys
11/20/2010 04:44 AM 32,896 USBCAMD2.sys
03/24/2011 09:29 PM 98,816 usbccgp.sys
07/13/2009 06:06 PM 100,352 usbcir.sys
03/24/2011 09:28 PM 7,936 usbd.sys
03/24/2011 09:29 PM 52,736 usbehci.sys
08/28/2012 06:27 AM 58,536 usbfilter.sys
03/24/2011 09:29 PM 343,040 usbhub.sys
03/24/2011 09:29 PM 25,600 usbohci.sys
03/24/2011 09:29 PM 325,120 usbport.sys
07/13/2009 06:38 PM 25,088 usbprint.sys
11/20/2010 05:37 AM 31,744 usbrpm.sys
03/10/2011 10:37 PM 91,648 USBSTOR.SYS
03/24/2011 09:29 PM 30,720 usbuhci.sys
07/13/2009 07:45 PM 36,432 vdrvroot.sys
07/13/2009 05:38 PM 29,184 vga.sys
07/13/2009 05:38 PM 29,184 vgapnp.sys
11/20/2010 07:34 AM 215,936 vhdmp.sys
01/14/2013 07:14 AM 1,301,504 viahduaa.sys
07/13/2009 07:45 PM 17,488 viaide.sys
07/13/2009 05:38 PM 129,024 videoprt.sys
11/20/2010 07:34 AM 199,552 vmbus.sys
11/20/2010 03:57 AM 21,760 VMBusHID.sys
11/20/2010 03:57 AM 6,656 vms3cap.sys
11/20/2010 07:34 AM 46,464 vmstorfl.sys
11/20/2010 07:34 AM 71,552 volmgr.sys
11/20/2010 07:34 AM 363,392 volmgrx.sys
11/20/2010 07:34 AM 295,808 volsnap.sys
07/13/2009 07:45 PM 161,872 vsmraid.sys
07/13/2009 06:07 PM 24,576 vwifibus.sys
07/13/2009 06:07 PM 59,904 vwififlt.sys
07/13/2009 06:07 PM 17,920 vwifimp.sys
07/13/2009 06:02 PM 27,776 wacompen.sys
11/20/2010 04:52 AM 88,576 wanarp.sys
07/13/2009 05:37 PM 42,496 watchdog.sys
07/13/2009 07:45 PM 21,056 wd.sys
07/25/2012 10:55 PM 785,512 Wdf01000.sys
07/25/2012 10:55 PM 54,376 WdfLdr.sys
07/13/2009 06:09 PM 12,800 wfplwf.sys
07/13/2009 07:45 PM 22,096 wimmount.sys
11/20/2010 07:33 AM 52,096 winhv.sys
07/13/2009 05:31 PM 14,336 wmiacpi.sys
07/13/2009 07:45 PM 16,464 wmilib.sys
07/13/2009 06:10 PM 21,504 ws2ifsl.sys
07/25/2012 08:26 PM 87,040 WUDFPf.sys
07/25/2012 08:26 PM 198,656 WUDFRd.sys
295 File(s) 56,814,168 bytes
Directory of C:\Windows\System32\Drivers\en-US
01/16/2013 06:06 AM <DIR> .
01/16/2013 06:06 AM <DIR> ..
07/13/2009 08:29 PM 11,776 1394ohci.sys.mui
07/13/2009 08:23 PM 9,216 acpi.sys.mui
07/13/2009 08:30 PM 14,848 afd.sys.mui
07/13/2009 08:25 PM 2,560 AGP440.sys.mui
07/13/2009 08:25 PM 2,048 amdide.sys.mui
07/13/2009 08:28 PM 14,336 amdk8.sys.mui
07/13/2009 08:28 PM 14,336 amdppm.sys.mui
07/13/2009 08:29 PM 3,072 ataport.sys.mui
07/13/2009 08:29 PM 3,072 atikmdag.sys.mui
07/13/2009 08:27 PM 7,168 battc.sys.mui
07/13/2009 08:30 PM 25,600 bfe.dll.mui
07/13/2009 08:28 PM 2,560 BrParwdm.sys.mui
07/13/2009 08:25 PM 10,240 BrSerIb.sys.mui
07/13/2009 08:30 PM 10,240 BrSerId.sys.mui
07/13/2009 08:30 PM 2,048 bthenum.sys.mui
07/13/2009 08:27 PM 4,608 bthpan.sys.mui
07/13/2009 08:27 PM 7,680 bthport.sys.mui
07/13/2009 08:30 PM 2,560 BTHUSB.SYS.mui
07/13/2009 08:29 PM 2,048 cdrom.sys.mui
07/13/2009 08:29 PM 2,048 disk.sys.mui
07/13/2009 08:28 PM 2,560 Dot4usb.sys.mui
07/13/2009 08:23 PM 5,120 fltmgr.sys.mui
07/13/2009 08:30 PM 14,336 fvevol.sys.mui
07/13/2009 08:29 PM 2,560 GAGP30KX.SYS.mui
07/13/2009 08:28 PM 4,096 hdaudbus.sys.mui
07/13/2009 08:30 PM 3,072 HdAudio.sys.mui
07/13/2009 08:24 PM 3,072 hidbth.sys.mui
07/13/2009 08:30 PM 32,256 http.sys.mui
07/13/2009 08:29 PM 10,240 i8042prt.sys.mui
07/13/2009 08:28 PM 14,336 intelppm.sys.mui
11/20/2010 07:11 AM 6,144 IPMIDrv.sys.mui
07/13/2009 08:23 PM 3,584 ipnat.sys.mui
07/13/2009 08:30 PM 3,584 isapnp.sys.mui
11/20/2010 07:10 AM 4,608 kbdclass.sys.mui
07/13/2009 08:24 PM 2,560 kbdhid.sys.mui
07/13/2009 08:29 PM 6,144 luafv.sys.mui
07/13/2009 08:28 PM 3,584 modem.sys.mui
07/13/2009 08:26 PM 4,096 mouclass.sys.mui
07/13/2009 08:24 PM 2,560 mouhid.sys.mui
07/13/2009 08:29 PM 2,560 mountmgr.sys.mui
07/13/2009 08:27 PM 26,624 mpio.sys.mui
07/13/2009 08:29 PM 5,632 msdsm.sys.mui
07/13/2009 08:24 PM 3,072 mssmbios.sys.mui
07/13/2009 08:27 PM 2,560 MTConfig.sys.mui
07/13/2009 08:29 PM 35,328 ndis.sys.mui
07/13/2009 08:29 PM 5,632 ndiscap.sys.mui
07/13/2009 08:23 PM 3,072 ndisuio.sys.mui
07/13/2009 08:26 PM 59,904 ntfs.sys.mui
07/13/2009 08:24 PM 2,560 NV_AGP.SYS.mui
07/13/2009 08:23 PM 13,824 nwifi.sys.mui
07/13/2009 08:29 PM 11,776 ohci1394.sys.mui
07/13/2009 08:25 PM 15,360 pacer.sys.mui
07/13/2009 08:29 PM 3,584 parport.sys.mui
07/13/2009 08:29 PM 2,560 partmgr.sys.mui
07/13/2009 08:29 PM 8,192 pci.sys.mui
07/13/2009 08:28 PM 4,096 pcmcia.sys.mui
07/13/2009 08:26 PM 2,560 pnpmem.sys.mui
07/13/2009 08:23 PM 3,584 portcls.sys.mui
07/13/2009 08:29 PM 14,336 processr.sys.mui
07/13/2009 08:30 PM 3,584 pscr.sys.mui
07/13/2009 08:24 PM 2,560 qwavedrv.sys.mui
07/13/2009 08:25 PM 4,608 rdbss.sys.mui
11/20/2010 07:01 AM 2,560 rdpwd.sys.mui
07/13/2009 08:28 PM 3,072 RNDISMP.sys.mui
07/13/2009 08:25 PM 3,072 rndismp6.sys.mui
07/13/2009 08:28 PM 3,072 rndismpx.sys.mui
07/13/2009 08:30 PM 2,560 scfilter.sys.mui
07/13/2009 08:24 PM 3,072 scsiport.sys.mui
07/13/2009 08:30 PM 10,240 serial.sys.mui
07/13/2009 08:29 PM 5,120 sermouse.sys.mui
07/13/2009 08:26 PM 2,560 serscan.sys.mui
07/13/2009 08:25 PM 2,560 srv.sys.mui
07/13/2009 08:28 PM 44,032 tcpip.sys.mui
07/13/2009 08:29 PM 4,096 tpm.sys.mui
08/23/2012 09:09 AM 3,072 tsusbflt.sys.mui
07/13/2009 08:24 PM 7,680 tunnel.sys.mui
07/13/2009 08:24 PM 2,560 UAGP35.SYS.mui
07/13/2009 08:23 PM 2,560 ULIAGPKX.SYS.mui
07/13/2009 08:29 PM 3,072 umbus.sys.mui
07/13/2009 08:24 PM 11,776 usbhub.sys.mui
07/13/2009 08:26 PM 24,576 usbport.sys.mui
07/13/2009 08:24 PM 2,048 usbrpm.sys.mui
07/13/2009 08:26 PM 3,584 vdrvroot.sys.mui
07/13/2009 08:29 PM 3,584 vhdmp.sys.mui
07/13/2009 08:23 PM 2,560 volmgrx.sys.mui
07/13/2009 08:28 PM 23,552 volsnap.sys.mui
07/13/2009 08:29 PM 2,048 vwifibus.sys.mui
07/13/2009 08:27 PM 4,096 wacompen.sys.mui
07/13/2009 08:26 PM 2,048 wd.sys.mui
07/25/2012 10:47 PM 2,560 wdf01000.sys.mui
07/13/2009 08:29 PM 2,048 ws2ifsl.sys.mui
91 File(s) 707,584 bytes
Directory of C:\Windows\System32\Drivers\etc
01/16/2013 06:07 AM <DIR> .
01/16/2013 06:07 AM <DIR> ..
06/10/2009 03:00 PM 824 hosts
06/10/2009 03:00 PM 3,683 lmhosts.sam
06/10/2009 03:00 PM 407 networks
06/10/2009 03:00 PM 1,358 protocol
06/10/2009 03:00 PM 17,463 services
5 File(s) 23,735 bytes
Directory of C:\Windows\System32\Drivers\UMDF
01/16/2013 06:02 AM <DIR> .
01/16/2013 06:02 AM <DIR> ..
01/16/2013 06:06 AM <DIR> en-US
07/13/2009 07:41 PM 299,520 WpdFs.dll
1 File(s) 299,520 bytes
Directory of C:\Windows\System32\Drivers\UMDF\en-US
01/16/2013 06:06 AM <DIR> .
01/16/2013 06:06 AM <DIR> ..
07/13/2009 08:24 PM 2,560 WpdMtpDr.dll.mui
07/13/2009 08:26 PM 6,144 WUDFUsbccidDriver.dll.mui
2 File(s) 8,704 bytes
Total Files Listed:
394 File(s) 57,853,711 bytes
14 Dir(s) 1,728,493,649,920 bytes free
***********************Hidden Drivers********************
Volume in drive C has no label.
Volume Serial Number is B2C6-174C
Directory of C:\Windows\System32\Drivers
01/13/2013 02:23 AM 0 Msft_User_WpdFs_01_09_00.Wdf
1 File(s) 0 bytes
0 Dir(s) 1,728,493,658,112 bytes free
*********************Processes*******************
PROCESS PID PRIO PATH
mbamgui.exe 2664 Normal C:\Program Files (x86)\Malwarebytes' Anti-Malware\mbamgui.exe
firefox.exe 2548 Normal C:\Program Files (x86)\Mozilla Firefox\firefox.exe
plugin-container.exe 4768 Normal C:\Program Files (x86)\Mozilla Firefox\plugin-container.exe
FlashPlayerPlugin_11_5_502_146.exe 4988 Normal C:\Windows\SysWOW64\Macromed\Flash\FlashPlayerPlugin_11_5_502_146.exe
FlashPlayerPlugin_11_5_502_146.exe 1396 Normal C:\Windows\SysWOW64\Macromed\Flash\FlashPlayerPlugin_11_5_502_146.exe
processes.exe 4964 Normal C:\Users\Justin Sidwell\Desktop\SpiderKill\SpiderKill\processes.exe
*********************Modules of explorer.exe and svchost.exe*******************
******************************************
EOF
Similar threads
- Locked
- Replies
- 0
- Views
- 3K
- Locked
- Replies
- 0
- Views
- 5K
Latest posts
-
The Radeon RX 9070 XT is Now Faster, AMD FineWine
- b3rdm4n replied
-
Greek man sentenced to prison for running a private torrent site 10 years ago
- Squid Surprise replied
-
Bitcoin worth $8.6 billion moved for the first time since 2011, bought for just $210K
- Squid Surprise replied
-
Agentic AI is all hype for now, says Gartner
- poohbear replied
-
Samsung delays $37B Texas chip plant with no customers in sight
- airbornex replied
-
TechSpot is dedicated to computer enthusiasts and power users.
Ask a question and give support.
Join the community here, it only takes a minute.