In context: Almost a year to the day after Bloomberg reported that the US government, Apple, Amazon, and others had their servers compromised by China, a security researcher has shown a similar hack can be pulled off with $190 worth of tools and a $2 chip.
Citing six senior national security officials and several higher-ups within Apple and Amazon, Bloomberg claimed that the manufacturing facilities constructing Supermicro motherboards had been infiltrated by a branch of China’s People’s Liberation Army. The PLA was reportedly adding a rice grain-sized chip capable of monitoring and altering communications with the motherboard’s BMC (baseboard management controller). The compromised motherboards had allegedly been sold in the tens of thousands to US customers, who could all, theoretically, be leaking their data to China.
Supermicro, Apple and Amazon all denied claims that they’d discovered the chips vehemently, the NSA said the threat was a false alarm, and the debate ended there. Last December, however, the hack was proven possible by Trammell Hudson, who’d found a spot on the Supermicro motherboard where a tiny chip could replace a small resistor and remain unnoticed. He connected a proof-of-concept chip only slightly larger than the resistor through external wires and completed the hack, concluding that anyone with a fab would be able to do a better job and remain undetected.
"For an adversary who wants to spend any money on it, this would not have been a difficult task," Hudson says.
Monta Elkins, who’s the “hacker-in-chief” for security firm Foxguard, can do it without the budget. Elkins, who’ll be formally presenting his work at the CS3sthlm security conference this month, was able to gain control over a Cisco ASA 5505 firewall server with a chip lifted from a $2 Digispark Arduino board. He assembled his hack using a $150 hot-air soldering tool and a $40 microscope.
"We think this stuff is so magical, but it’s not really that hard," Elkins told Wired. "By showing people the hardware, I wanted to make it much more real. It’s not magical. It’s not impossible. I could do this in my basement. And there are lots of people smarter than me, and they can do it for almost nothing."
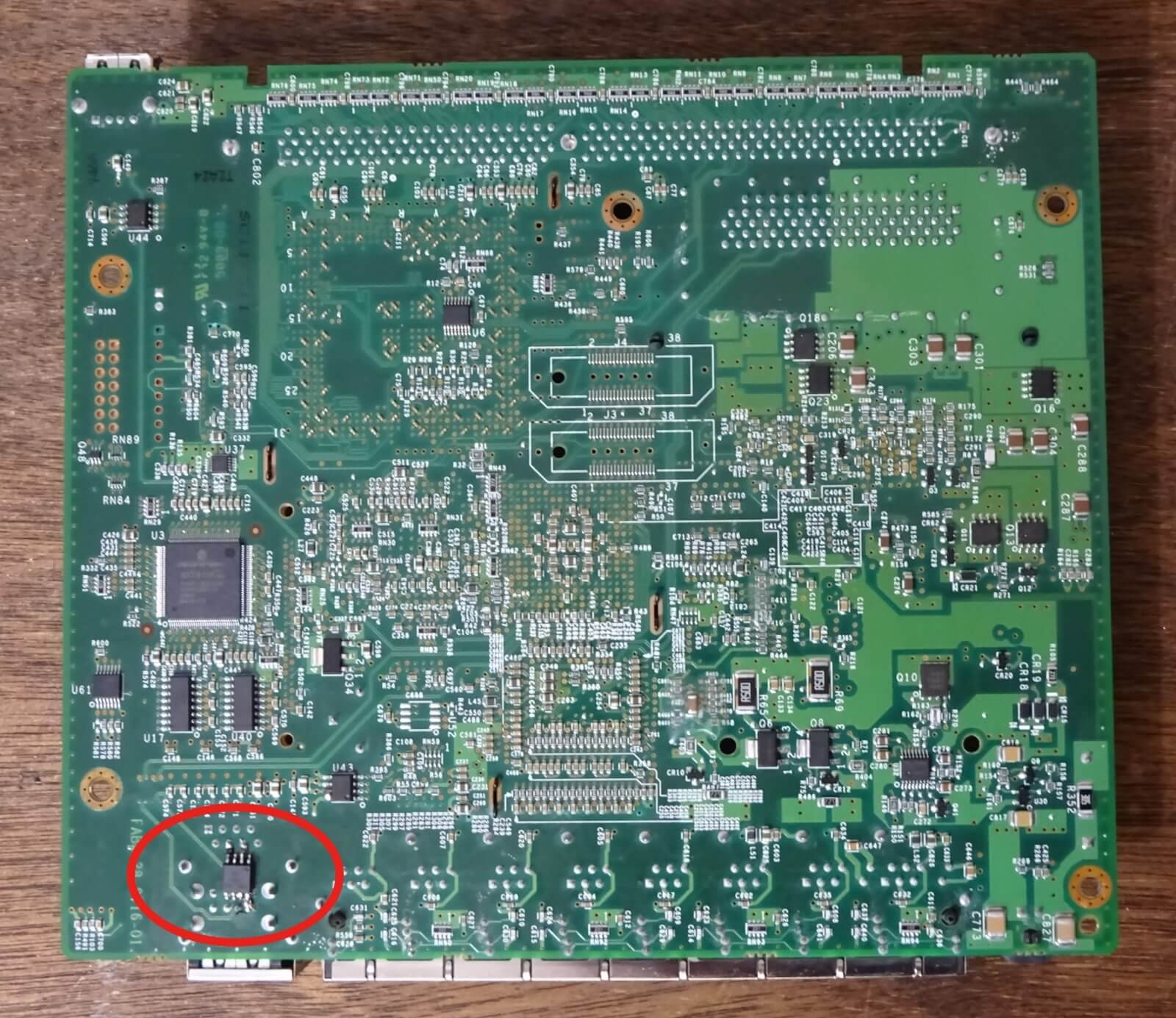
The implanted chip on the underside of the motherboard. Credit: Monta Elkins
Once soldered to the board (which didn’t require any special rewiring) the ATtiny85 chip impersonates an administrator as the server boots up and triggers a common password recovery feature. It gains access to the firewall settings which can be reconfigured remotely, enabling the hacker to disable security features or access logs of connected devices. Elkins says the hack could also be used to gain full control over the system, but he didn’t go that far with his proof-of-concept.
Perhaps the scary thing about all this is that Elkins didn’t exactly do too much here – he chose the server board because it was the cheapest one on eBay, and he chose the chip because it was the fastest to program. He could have gone further as well, by hiding the chip inside a radio-frequency shielding can on the board, but he wanted to be able to point it out on diagrams.
"What I want people to recognize is that chipping implants are not imaginary. They’re relatively straightforward," says Elkins. "If I can do this, someone with hundreds of millions in their budget has been doing this for a while."
Hardware hacking has often been considered inconceivable. Certainly, software-based espionage is much simpler against the vast majority of targets, but hardware hacking is a demonstrated technical reality that could become a major concern in the future.
Image Credit: Umberto on Unsplash
https://www.techspot.com/news/82320-hobbyists-can-plant-hidden-spy-chips-motherboards-200.html