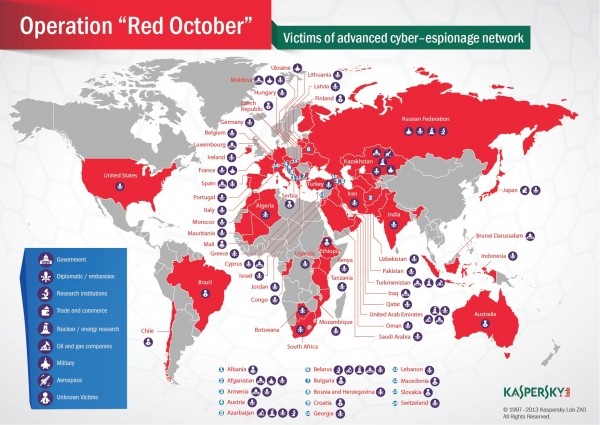
Kaspersky has uncovered an advanced cyber espionage network that rivals the sophistication of last year's infamous Flame malware but is perhaps more devious, as each attack is handcrafted for its victim to help ensure its success. Referred to as Operation Red October (abbreviated as "Rocra"), the campaign has been ongoing since at least May 2007 and carefully targets victims in over two dozen countries who hold positions in government, military, aerospace, research, trade and commerce, nuclear, oil and other such industries.
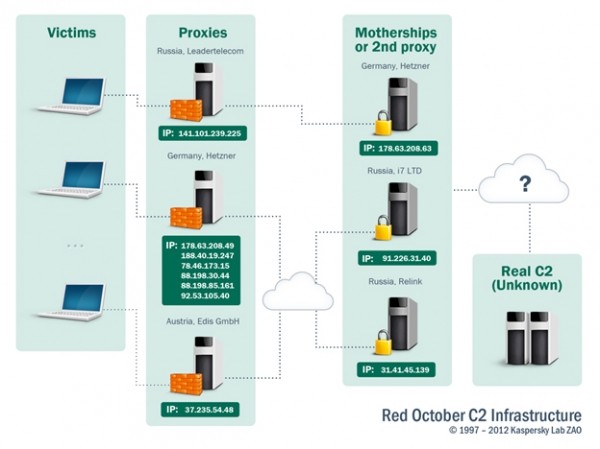
Investigators aren't sure who's behind the attacks, but it's believed that the exploits used may have been created by Chinese hackers, while the various malware modules deployed seem to have been created by folks who speak Russian. Kaspersky can't identify the source of the operation at this point because it's being run through at least two layers of proxy servers across Russia, Germany and Austria. In other words, the location of the primary command and control center (dubbed the "mothership" C&C) remains unknown.
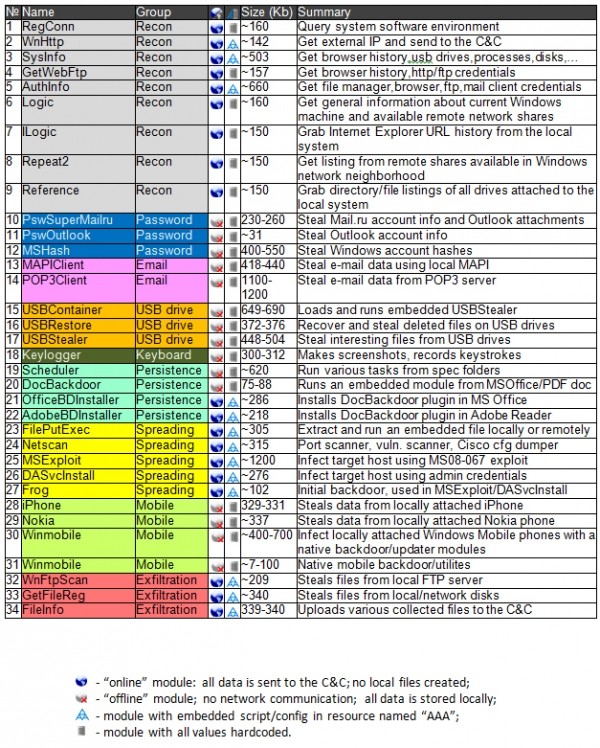
Whoever they are, the operators clearly know what they're doing if they've been secretly lurking on the systems of major governments and industries around the globe for half a decade. During that time, they used at least two different exploits in Microsoft Word and one in Excel to infect targets through spear phishing schemes. After compromising a system, the attackers would harvest whatever sensitive data they could through a series of persistent and one-time tasks conducted with over a thousand modules (malicious files).
Some examples of the tasks include swiping information from USB drives (even deleted files), recording keystrokes, taking screenshots, retrieving email from Outlook and mail servers, collecting browsing history and saved passwords, scanning networks to find more potential victims and so on. In addition to being in the dark about who's pulling the strings, Kaspersky isn't sure what they're doing with all this info, besides maybe selling it on the black market. The outfit says there's no evidence that the campaign is state sponsored.