VeraCrypt adds enhanced security to the algorithms used for system and partitions encryption making it immune to new developments in brute-force attacks. VeraCrypt also solves many vulnerabilities and security issues found in TrueCrypt.
Is VeraCrypt more secure than TrueCrypt?
Yes, VeraCrypt is considered more secure than its predecessor, TrueCrypt. After TrueCrypt's discontinuation, VeraCrypt addressed known vulnerabilities and implemented several security enhancements. These include increased iterations for key derivation functions, support for newer encryption algorithms, and protection against certain types of attacks.
Should I use full disk encryption (FDE) or just encrypt a partition?
Consider your security requirements and technical comfort level when choosing between the two. The choice depends on your specific needs:
- Full Disk Encryption (FDE): Encrypts the entire drive, including the operating system. This offers comprehensive protection but may be more complex to set up, especially on systems with UEFI and GPT partitions.
- Partition/Container Encryption: Encrypts specific partitions or creates encrypted containers within a file. This method is more flexible and easier to manage, especially for encrypting external drives or specific data folders.
Can I use VeraCrypt on SSDs, and are there any concerns?
Yes, VeraCrypt can be used on SSDs. However, due to the wear-leveling feature of SSDs, which distributes data across the drive to prolong its lifespan, there may be concerns about residual data remnants. To mitigate this, it's recommended to perform a full format (not a quick format) when creating encrypted volumes, ensuring that all sectors are overwritten with random data.
What is a hidden volume, and how does it provide plausible deniability?
A hidden volume is a feature in VeraCrypt that allows you to create a concealed volume within another VeraCrypt volume. This setup provides plausible deniability, as the existence of the hidden volume cannot be proven without the correct password. Even if someone forces you to reveal the password to the outer volume, the hidden volume remains secure and undetectable.
Features
- Creates a virtual encrypted disk within a file and mounts it as a real disk.
- Encrypts an entire partition or storage device such as USB flash drive or hard drive.
- Encrypts a partition or drive where Windows is installed (pre-boot authentication).
- Encryption is automatic, real-time(on-the-fly) and transparent.
- Parallelization and pipelining allow data to be read and written as fast as if the drive was not encrypted.
- Encryption can be hardware-accelerated on modern processors.
- Provides plausible deniability, in case an adversary forces you to reveal the password: Hidden volume (steganography) and hidden operating system.
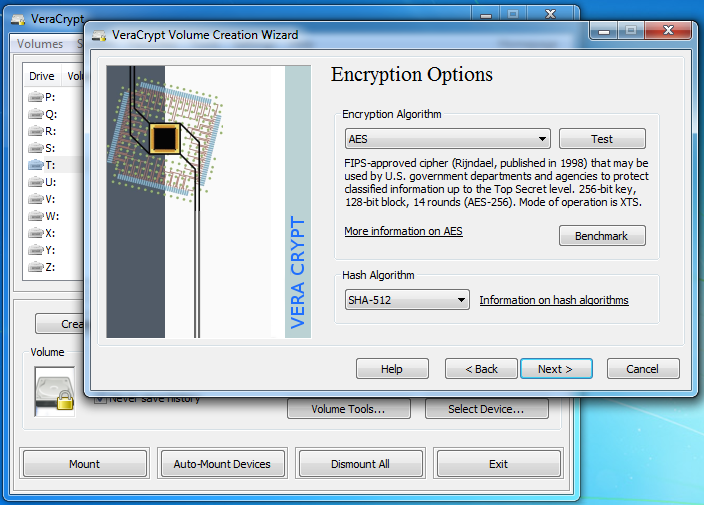
VeraCrypt adds enhanced security to the algorithms used for system and partitions encryption making it immune to new developments in brute-force attacks. For example, when the system partition is encrypted, TrueCrypt uses PBKDF2-RIPEMD160 with 1000 iterations whereas in VeraCrypt we use 327661. And for standard containers and other partitions, TrueCrypt uses at most 2000 iterations but VeraCrypt uses 655331 for RIPEMD160 and 500000 iterations for SHA-2 and Whirlpool.
This enhanced security adds some delay only to the opening of encrypted partitions without any performance impact to the application use phase. This is acceptable to the legitimate owner but it makes it much more harder for an attacker to gain access to the encrypted data.
What's New
All OSes:
- Fix whirlpool implementation for big-endian platforms (GH #1529).
- Rename "Dismount All" to "Unmount All" in UI. Use ALT+u as new accelerator key instead of ALT+s
- Add contributed Chinese and Russian CHM documentation.
- Update translations.
Windows:
- Implemented screen protection against screenshots and screen recording, enabled by default.
- This feature can be disabled during installation or via the Performance/Driver Configuration settings.
- Added checkboxes to the MSI installer to control memory protection and screen protection features.
- Introduced command-line options DISABLEMEMORYPROTECTION and DISABLESCREENPROTECTION for the MSI installer to manage these features.
- Both options accept values 0 (enabled) or 1 (disabled).
- Example usage:
- msiexec /i VeraCrypt_Setup_x64_1.26.24.msi DISABLESCREENPROTECTION=1 /qn REBOOT=ReallySuppress MSIRESTARTMANAGERCONTROL=Disable ACCEPTLICENSE=YES
- Fix race conditions when multiple instances of veracrypt.exe are started simultaneously.
- Updated libzip to version 1.11.3.
Linux:
- Add support for AppImage packaging and usage.
- Fix absolute path of 'true' command not being used when checking if sudo session is active.
- Fix failure to use Hungarian language translations.
- Improve generic installer scripts (GH #1514).
- Add support for /run/media/veracrypt as default mount prefix when /media is not available(GH #1524).
- Remove pcsclite dependency from .deb/.rpm packages since it is detected/loaded dynamically at runtime.
macOS:
- Fix absolute path of 'true' command not being used when checking if sudo session is active.
- Create simlink of VeraCrypt in /usr/local/bin to allow using it from command line.
- Fix failure to use Hungarian language translations.