In context: A zero-day vulnerability is an undiscovered security flaw that has already been exploited by cybercriminals and other threat actors. According to new research from Google, the zero-day threat continues to grow at a slow but steady pace.
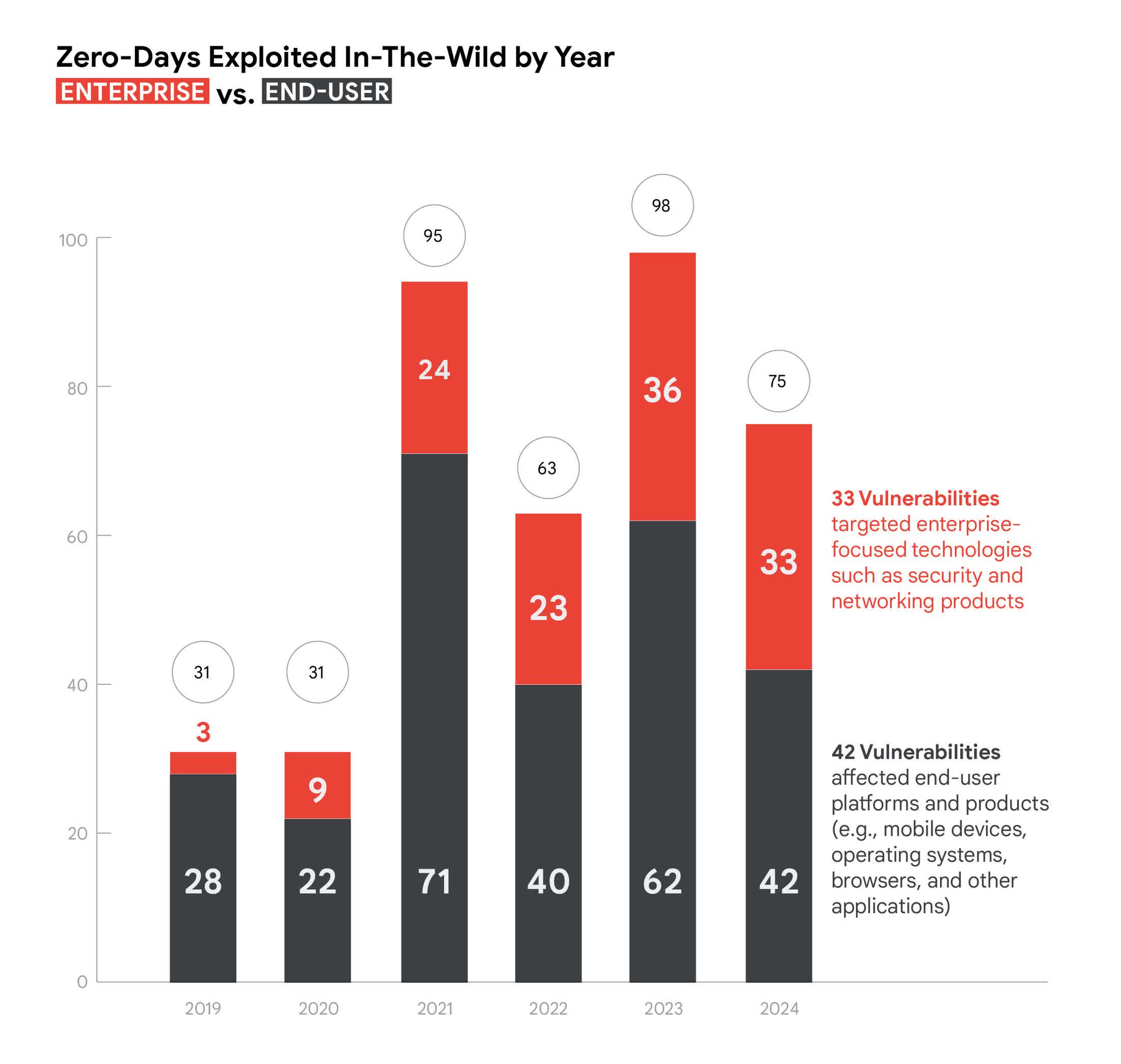
The zero-day business is steadily improving for cybercriminals and becoming increasingly dangerous for end users, professionals, and enterprise organizations. After analyzing 75 zero-day vulnerabilities that could be confidently attributed in 2024, the Google Threat Intelligence Group released a report detailing the facts and trends uncovered during the investigation.
The report focuses on zero-day bugs that were both detected and disclosed, meaning a significant number of undetected vulnerabilities may still be lurking in IT systems and devices.
While the 75 exploited bugs identified in 2024 represent a decrease from the 98 reported in 2023, the overall trend remains consistent: the zero-day exploitation market continues to grow at a steady pace. Attackers are increasingly targeting enterprise environments, with a particular emphasis on security and network infrastructure products.

Cyber-espionage operations are leading the way in zero-day exploit attribution, according to Google. Government-backed threat groups – and in some cases, third-party hackers working on behalf of hostile state actors – were responsible for over 50 percent of the vulnerabilities that the Google Threat Intelligence Group was able to attribute in 2024. Chinese state-sponsored hackers accounted for five known zero-day exploits, while North Korean cyber-espionage groups matched that figure for the first time ever.
Another significant threat comes from commercial spyware vendors, who often claim to sell their tools exclusively to legitimate government clients. However, even when such companies are shut down by law enforcement or face public backlash, GTIG noted that the demand for these invasive products remains high enough to sustain and even grow the industry.
Google's report also offers some guidance for software and hardware vendors seeking to curb the spread of zero-day threats. While vulnerabilities are becoming easier to acquire and exploit, widely used products such as mobile operating systems and web browsers have improved their security posture. Nonetheless, end-user products continue to be prime targets for both cybercriminals and nation-state attackers. This, Google says, underscores the need for stronger and continuously evolving security practices across the tech ecosystem.