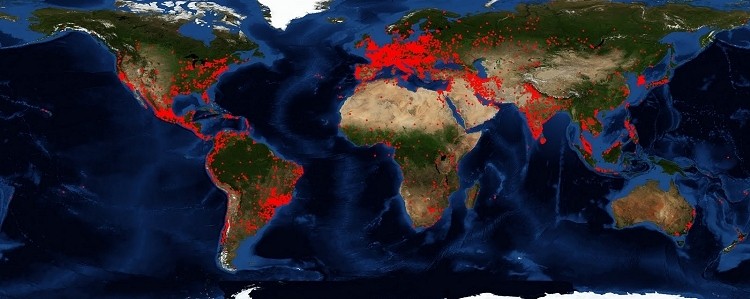
Symantec is going toe to toe with ZeroAccess, one of the largest known botnets in existence today. On any given day, ZeroAccess has upwards of 1.9 million computers at its disposal... or at least, it did. The team has been working on a method called a sinkhole to take down the botnet since March but a report published by security researchers in May discussing the weakness likely prompted the ZeroAccess botmaster to upgrade the botnet to prevent the sinkhole.
As such, a new version of the botnet surfaced that patched the flaw which made it vulnerable to being sinkholed. With a viable plan in place, Symantec moved ahead with the plan and began to sinkhole non-updated ZeroAccess infections on July 16. The operation resulted in the detachment of over half a million bots and made a serious dent in the number of bots controlled by the botmaster.
To understand the impact of the sinkhole, Symantec suggests users need to understand exactly what the botnet is used for.
Unlike other botnets, ZeroAccess appears to be designed primarily to deliver payloads to infected machines. Those payloads are what cause the problems and with ZeroAccess, it boils down to two types that are both aimed at generating revenue: click fraud and Bitcoin mining.
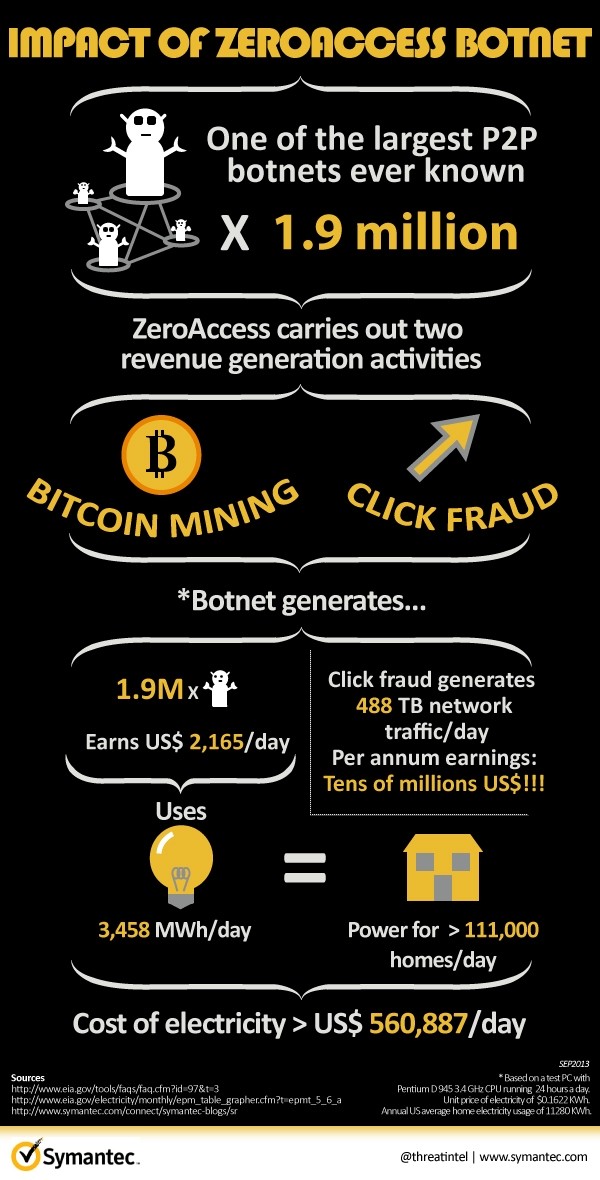
In laboratory testing, Symantec found that each bot generated roughly 42 false ad clicks per hour which could potentially earn the botmaster tens of millions of dollars in revenue per year. A single computer mining Bitcoin is likely to earn less than $1 per year but if you have 1.9 million machines at your disposal, the equation changes completely.
The job isn't finished, Symantec warned, but they've put a pretty heavy dent in the botnet. They are now working with ISPs and CERTs across the globe to share information and help clean infected machines.