Auto correct Human beings make terrible drivers. They talk on the phone and run red lights, signal to the left and turn to the right. They drink too much beer and plow into trees or veer into traffic as they swat at their kids. They have blind spots, leg cramps, seizures, and heart attacks. They rubberneck, hotdog, and take pity on turtles, cause fender benders, pileups, and head-on collisions. They nod off at the wheel, wrestle with maps, fiddle with knobs, have marital spats, take the curve too late, take the curve too hard, spill coffee in their laps, and flip over their cars. Of the ten million accidents that Americans are in every year, nine and a half million are their own damn fault. The New Yorker
Fall 2013 supercomputer rankings released; achieving max efficiency with oil Turning our eyes back towards SC13 and supercomputers one more time this week, we have the biannual supercomputer rankings, which are released every spring and every fall. These rankings are composed of the Top500 and Green500, which rank supercomputers based on total performance and power efficiency respectively. These lists are admittedly mostly for bragging rights, but they do give us an interesting look at what the top computers in the world currently look like. AnandTech
Study shines light on what makes digital activism effective Digital activism is usually nonviolent and tends to work best when social media tools are combined with street-level organization, according to new research from the University of Washington. The findings come from a report released today (Nov. 20) by the Digital Activism Research Project run by Philip Howard, UW professor of communication, information and international studies. Founded by Howard in 2012, the project applies rigorous empirical social science methods to the study of global digital activism. UW
Using TrueCrypt on Linux and Windows After numerous revelations this year of the National Security Agency's (NSA) frightening capabilities of mass spying on phone calls and Internet traffic (see, for example, PRISM), there has been a renewed interest in online privacy and the securing of our electronic data communications, such as Web and email activity. More and more Internet users are looking for solutions to keep their files, emails, and Web searches private. Help is not far off: one of the most effective ways to foil surveillance is by using encryption to make your data unreadable by other parties. Doug Vitale
A month with the Surface 2 The second generation Surface is a well-built, highly functional machine but it has yet to catch-on in the market to the same degree of the iPad. For Microsoft, the Surface is a must-win device as the company shifts from a software focused company, to a device and services model where the Surface plays a key part. Without the Surface, Microsoft's consumer branded ecosystem is incomplete as they have mobile with the Nokia mobile acquisition, the living-room with the Xbox One and the personal computer with the Surface 2 and Surface Pro 2. Neowin
NSA infected 50,000 computer networks with malicious software The American intelligence service - NSA - infected more than 50,000 computer networks worldwide with malicious software designed to steal sensitive information. Documents provided by former NSA-employee Edward Snowden and seen by this newspaper, prove this. A management presentation dating from 2012 explains how the NSA collects information worldwide. In addition, the presentation shows that the intelligence service uses 'Computer Network Exploitation' (CNE) in more than 50,000 locations. NRC
Software is reorganizing the world For the first time in memory, adults in the United States under age forty are now expected to be poorer than their parents. This is the kind of grim reality that in other times and places spurred young people to look abroad for opportunity. Indeed, it is similar to the factors that once pushed millions of people to emigrate from their home countries to make their home in America. Our nation of immigrants is, tautologically, a nation of emigrants. These emigrants, our ancestors, didn't bear enmity towards the countries they left – quite the contrary. Wired
The state of smartphones in 2013: part i of the new Ars Ultimate guide It's been just under a year since the last time we examined the state of the smartphone. The intervening months have brought us the expected annual hardware refreshes and software updates, but it's striking just how similar things are at a high level. Apple and Samsung are still standing at the top of the field, and at the moment there's not a strong third-place contender in sales or in reach. HTC continues to be down on its luck despite the critical darling that is the HTC One. Ars Technica
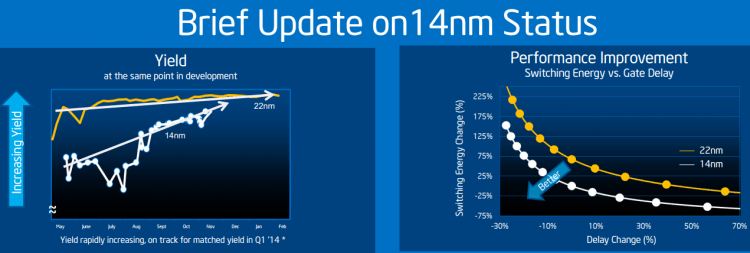
Intel's 14nm milkshake: It's better than yours At yesterday's Analyst Day, Intel broke out some details on its upcoming 14nm process, the state of that technology, and just how far along the ramp-up it is. Having recently announced that Broadwell's 14nm deployment would be somewhat delayed by yield issues, it's possible that the manufacturer felt the need to address rumors of serious problems in the fab line – or maybe it just wanted to gloat. To hear Intel tell it, 14nm yields aren't the only thing ramping well. The process node is on target to deliver the kind of marked improvements in cost, performance, and density... ExtremeTech
The surprising second life of the PS Vita The PlayStation 4 arrives next week, but it's not the only anniversary Sony's marking before the end of the year. Next month, the PS Vita gaming handheld celebrates its second birthday. You might have forgotten about Sony's attempt to put the power of a PS3 in your pocket, but it's still alive and kicking - in September, a second-generation model was released with a thinner shell and lower price tag, the PS Vita 2000. Redbull
The anonymous Tor network now comes in a box I have the Tor browser running on my computer, and it took me about two minutes to download. Once you're surfing through the network there are plenty of daunting technical options to dig into, but accessing the onion network for basic, everyday web use was as easy as clicking download, opening the program, and then struggling to remember all my no-longer-stored passwords. Vice
Study suggests link between Dread Pirate Roberts and Satoshi Nakamoto Two Israeli computer scientists say they may have uncovered a puzzling financial link between Ross William Ulbricht, the recently arrested operator of the Internet black market known as the Silk Road, and the secretive inventor of bitcoin, the anonymous online currency, used to make Silk Road purchases. The NY Times
