Security researcher Sean Cassidy recently discovered a phishing attack against popular password manager LastPass. The incident drew the attention of LastPass which has implemented additional steps to help mitigate the risk.
Cassidy's attack, dubbed LostPass, is based on the fact that LastPass displays messages in the browser which are easy for attackers to fake. The end-user can't tell the difference between a legitimate prompt and a fake LostPass message because there is no difference - they're literally pixel-for-pixel identical.
To pull off the phishing attempt, an attacker would need to lure a victim to a malicious website. If the user has LastPass installed, a fake login expiration notification will be displayed and the user will be logged out of the service. From there, it's just a matter of waiting for them to enter their credentials.
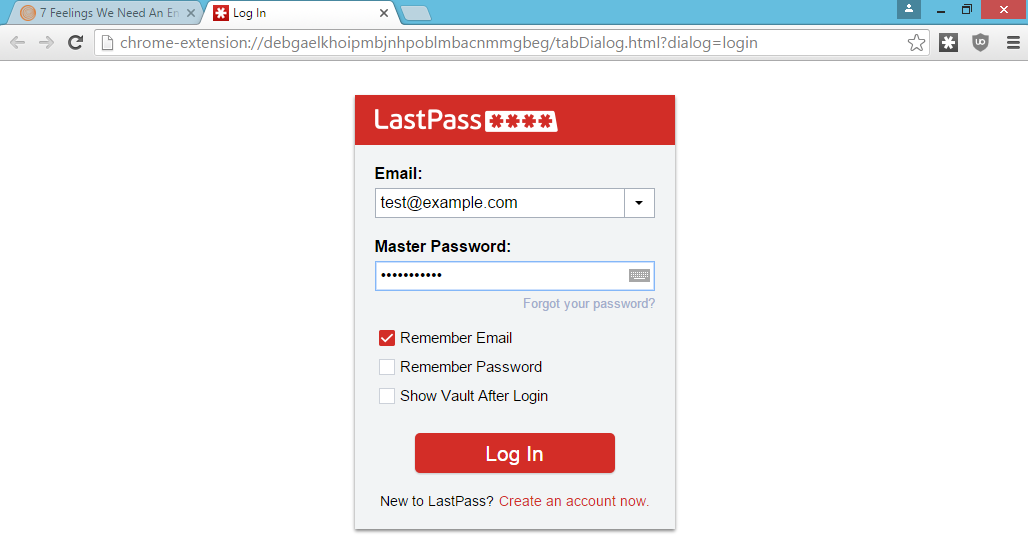
LostPass can even snag a two-factor token if the extra layer of security is indeed in use.
With the login credentials, the attacker can steal all of a user's other login credentials, install a backdoor in their account using the emergency contact feature, disable two-factor authentication and more.
In a subsequent post, LastPass said it now prevents malicious pages from logging users out of the password manager. The malicious page will still say the user has been logged out although a quick check of the LastPass extension in the browser toolbar will show it as still logged in.
Should the user miss this nugget of information, LastPass will pop up a warning whenever the master password is entered on a non-LastPass page. If this is somehow suppressed, the attacker still likely won't get far as LastPass has an e-mail verification system in place requiring a user to authorize a login from an unknown device or location.
LastPass said it is working to release additional notification options.
