In context: Carrying personal or otherwise sensitive data in our phones is commonplace, so the thought of all of that data being easily accessible through a Russian spyware tool hidden inside fake apps is no doubt worrying. What might offer you some peace of mind is that it appears to be built for targeting certain regions in the Middle East, but the fact that it can take control of your device so easily means it could always find a place in the wrong hands.
If Pegasus wasn't scary enough, researchers at a security firm Lookout have uncovered Monokle, yet another spyware tool for mobile phones that appears to be just as advanced. As it turns out, it is the work of a Russian military contractor that was sanctioned in 2016 as a result of being involved with Russia's Main Intelligence Directorate in gaming the U.S. presidential election.
Known as the Special Technology Center (STC), the group has been active since 2000 and employs almost 1,500 people that work mostly on unmanned aerial vehicles (UAVs) and radar systems. Now we know that some of them also develop and maintain a spyware tool that can change security certificates on a phone and steal data from it.
Monokle isn't just a simple piece of surveillance software, as evidenced in the Lookout analysis, where researchers explain its capabilities in more detail. What is worrisome about it is that the creators were particularly creative with how STC implemented the "surveillanceware" tool, which mostly targets Android devices and doesn't need root access or an internet connection to be effective.
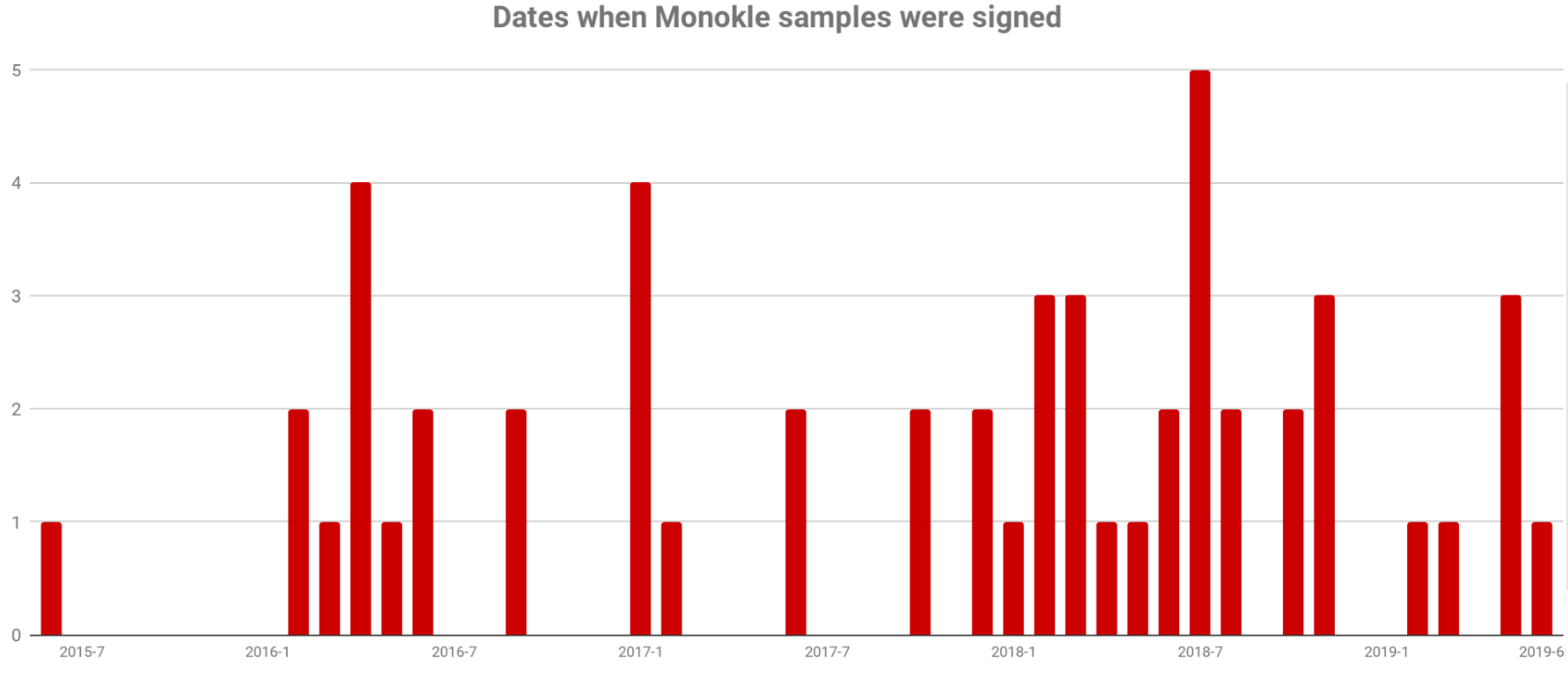
It's also interesting that just like Pegasus, Monokle appears to be more useful in targeted attacks, and is built to closely imitate popular apps such as Pornhub, Evernote, Google Play, and Skype. One of the many ways it works is by exploiting accessibility services and modifying them to be used for data theft. It's worth noting that Monokle has been out in the wild for as many as four years already, with regular spikes of activity over time.
The researchers say there are no less than 80 points of attack that Monokle can use to compromise a phone, and a long list of things it can do – from stealing a user pin code to retrieving every piece of information residing on your device, and messages from apps like WhatsApp and Skype. If need be, it can wipe all traces of its existence.
Lookout researchers found that STC developed a security app that shares the same private internet infrastructure as Monokle, and there are references to iCloud and Apple Keychain in the code that hint at an iOS version being developed.
There's no indication that Monokle has been used for mass surveillance, but it definitely is sophisticated enough for that, and apparently it's still in development. There are nonetheless fewer reasons to worry about it than Pegasus, which requires no interaction with the end user to get installed.
