What just happened? Apple has opened its bug bounty program to all security researches, having previously been invitation-only and limited to iOS vulnerabilities. The iPhone-maker first announced the planned expansion to its program at the Black Hat conference in Las Vegas back in August.
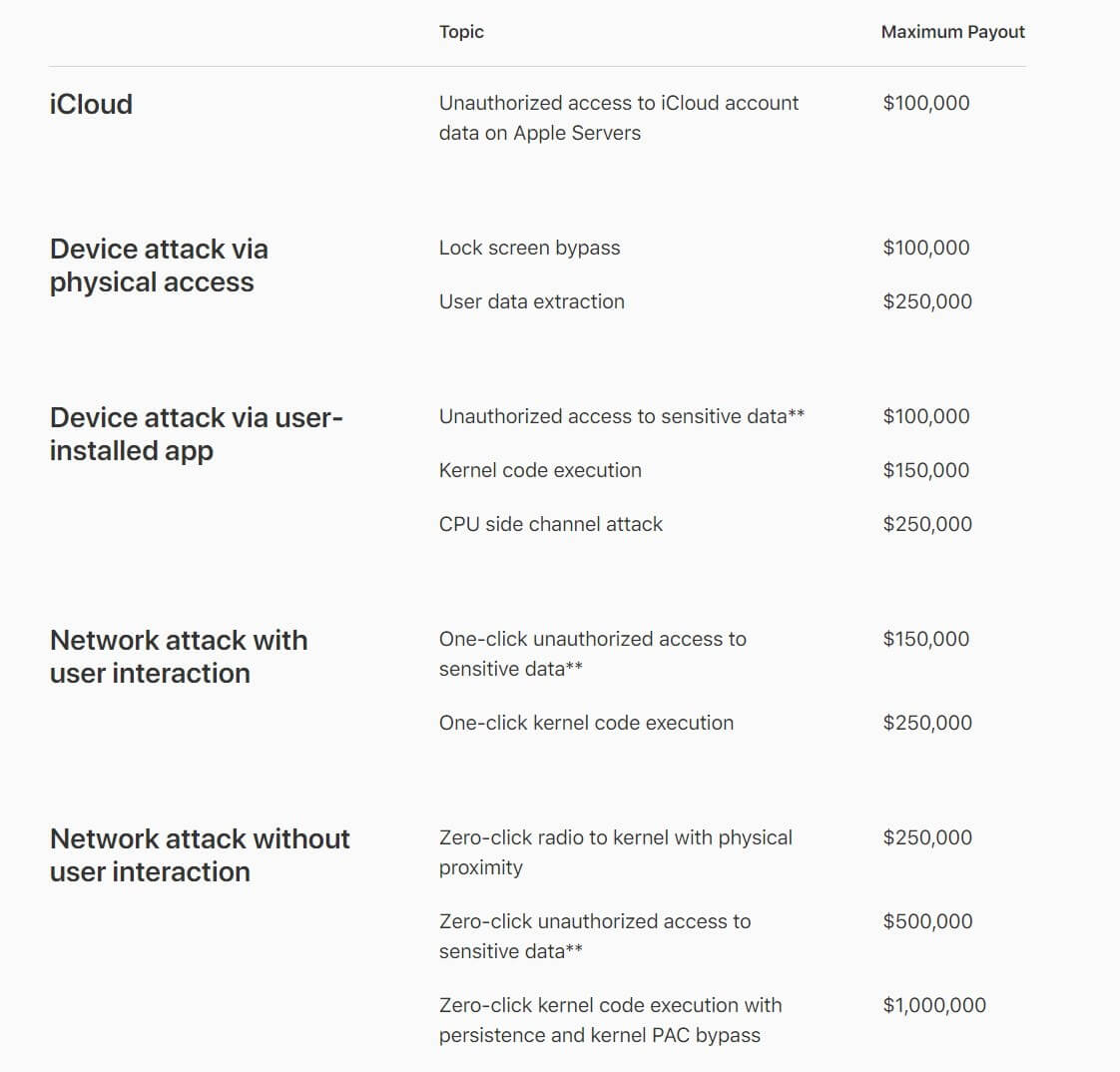
As noted by ZDNet, any security researchers who discover working exploits in iOS, macOS, tvOS, watchOS, or iCloud will now be able to collect a cash reward for Apple, providing they meet the eligibility rules. Additionally, the maximum reward has been increased from $200,000 up to $1 million, which is paid for a zero-click kernel code execution with persistence.
Any researcher who discloses a vulnerability must submit a report that includes:
- A detailed description of the issues being reported.
- Any prerequisites and steps to get the system to an impacted state.
- A reasonably reliable exploit for the issue being reported.
- Enough information for Apple to be able to reasonably reproduce the issue.
Reports that include a basic proof of concept instead of a working exploit are eligible to receive no more than 50% of the maximum payout amount.
For those looking to maximize their payout, Apple said it is particularly interested in bugs that affect multiple platforms, impact the latest publicly available hardware and software, impact sensitive components, and are novel.
Any bugs found in beta releases come with an extra 50 percent bonus on top of the standard payout. These are highly valued as discovering bugs in beta allows Apple to address them before the public rollout. The 50 percent extra bonus is also offered for "regression bugs," which are vulnerabilities that Apple patched in previous versions of its software but have been accidentally reintroduced in a later version.
In other bug bounty news, OnePlus has just launched a program of its own, though its rewards for disclosure start at $50 and reach a maximum of $7,000 for "Special cases."
