The big picture: Security researchers with Malwarebytes recently unmasked a clever tactic being used by hackers to steal credit card data from an online store created with WordPress, a popular content management system. Using images for nefarious purposes is not new although Malwarebytes said this is the first time they've seen a credit card skimmer used in this sort of attack.
At the onset of its investigation, Malwarebytes' threat analysis team thought it might be another case of a credit card skimmer masquerading as a favicon but further digging uncovered something entirely different.
Rather than hiding malicious code used to steal credit card information in a website's favicon, the hackers had embedded it within the metadata of an image file which then gets covertly loaded by a compromised online store.
EXIF, short for Exchangeable Image File Format, is metadata that is often associated with a digital image. It is used to convey useful information about a photo, such as the camera settings and hardware that was used to create it.
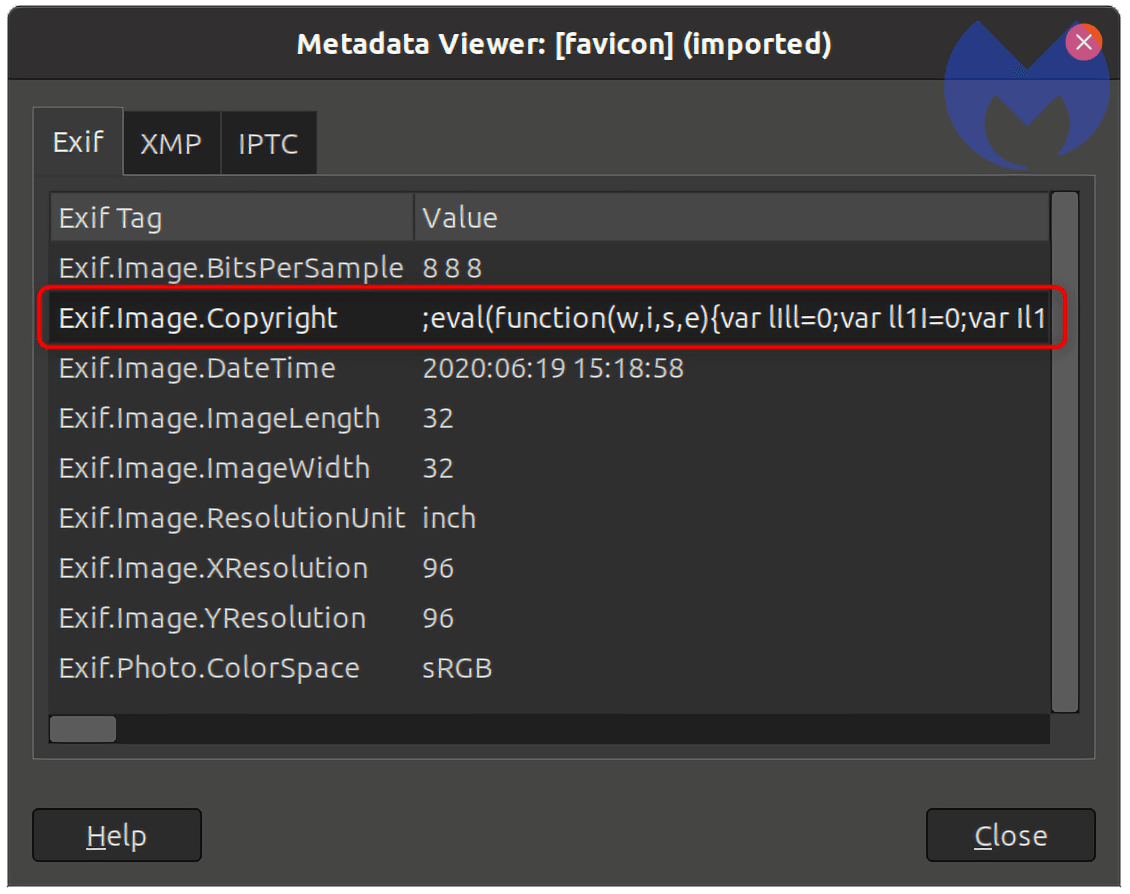
In this instance, researchers found that hackers were using the copyright metadata field to load JavaScript. Once activated, the skimmer grabs data from the input fields of an online store where shoppers key in their name, billing address and payment card details.
In an interesting twist, the collected data is then loaded back into an image file for the hacker to collect. This and other steps are likely performed to reduce the chances of the attack raising suspicion.
