Ransomware threats: The threat of ransomware continues to grow across the globe. Malicious actors have used these data-encrypting hacks to extort money from hospitals, businesses, and even major natural gas pipelines. The effects can be devastating. Though ordinary consumers are not usually considered juicy targets for hackers (with some exceptions), it's still helpful to insulate yourself from these attacks as best you can. But how?
There are the obvious methods, of course: backup your data to offline, local drives regularly, keep important files in more than one secure location and avoid downloading suspicious media or opening fishy emails (and somehow avoid sharing a network with people that do, I suppose). The usual data security 101 steps.
If those steps are impractical, impossible, or simply not helpful for you (perhaps you've already done them), you might have another option. As noted by Forbes, Windows 10 has a built-in "Ransomware protection feature," available to any users with a reasonably up-to-date version of the OS.
This feature has existed for a while, but it seems to have mostly flown under everyone's radar. I've spotted the option in the past whilst digging through my Windows 10 settings menus (mostly to disable telemetry), but I never thought much of it until now.
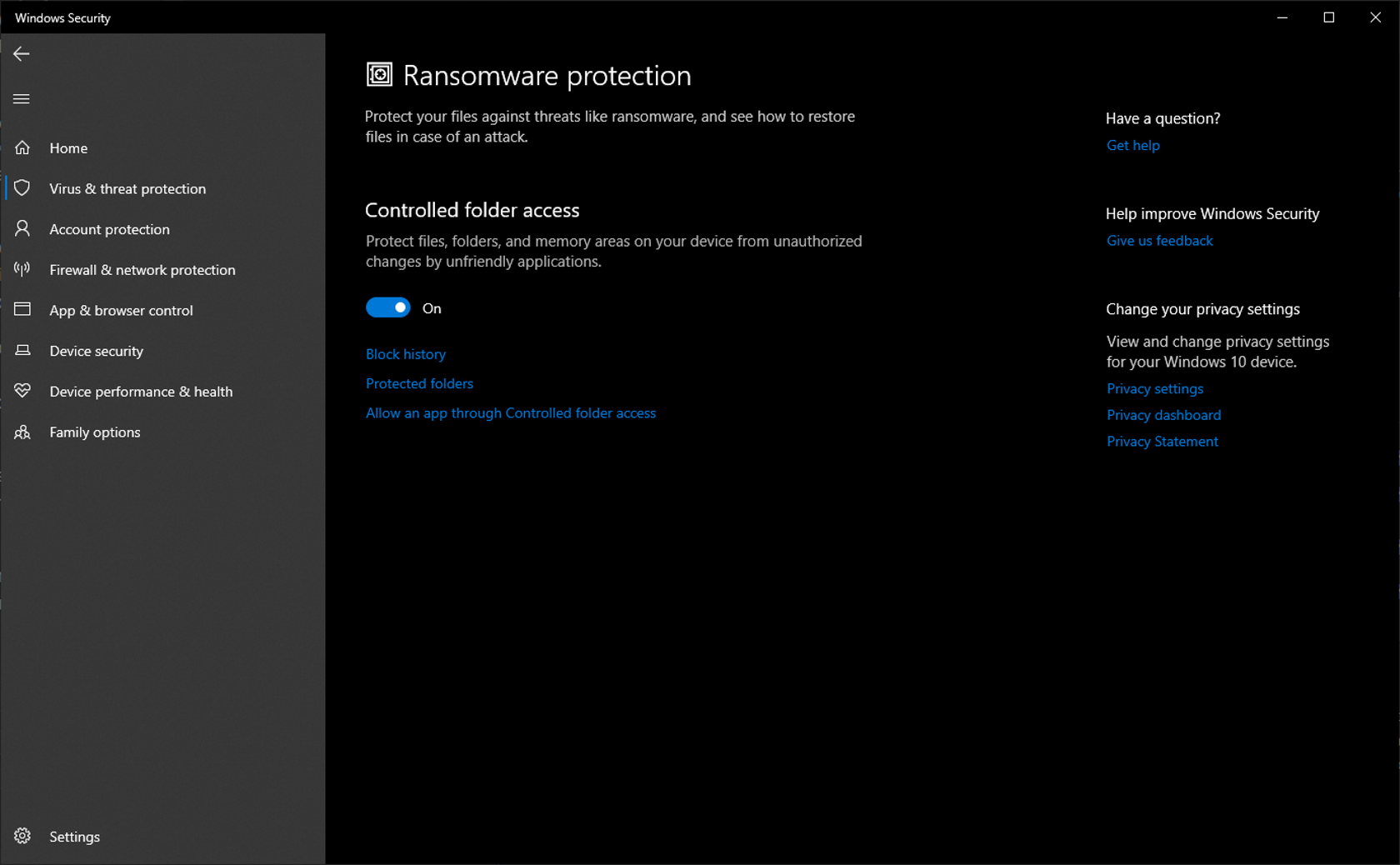
So, what is Ransomware protection, and how does it work? To answer the former, we just need to look at the name: it's a Windows Security feature that seeks to help users protect themselves against ransomware attacks (and, in some cases, recover their data post-attack).
As for how it works, Microsoft offers something called "Controlled folder access," which lets you designate specific folders that only "trusted apps" may access. The tech giant says this prevents the contents of the folders from being changed or, more notably, encrypted by any malware, ransomware included.
If you want an easy set-it-and-forget-it option, just flip the controlled folder access toggle and leave it be. By default, only "key folders" (such as Pictures and Documents) will be protected, but you can add additional ones or alter the defaults at will.
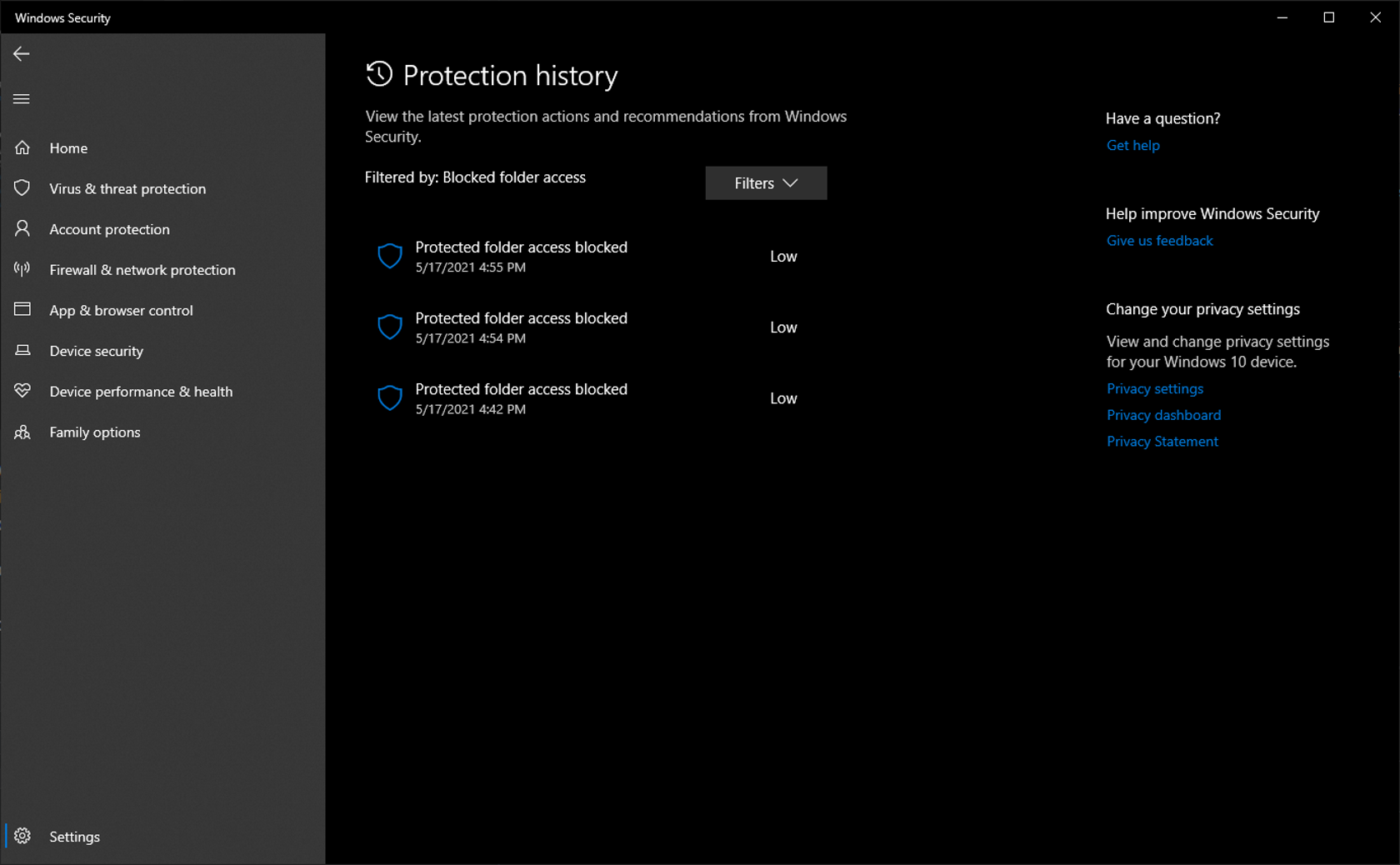
If you want to test that the feature is working as intended, try using a few third-party apps to, say, edit some images from your Pictures folder. Ideally, you'll get an error message and a security event notification from Windows.
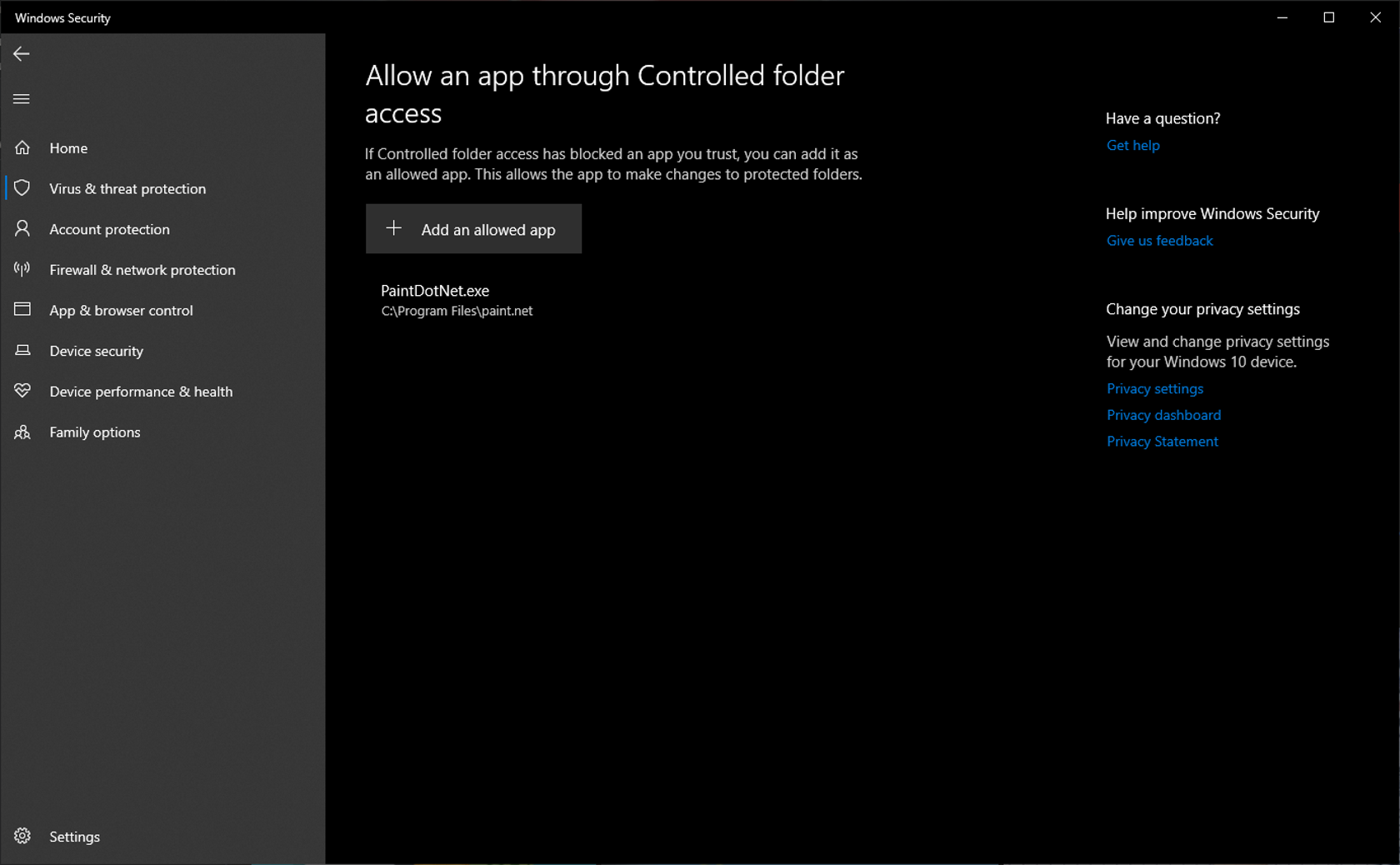
If you fully trust the security of a specific app, you can allow it to bypass this protection by making it an "allowed app." This can be done through either the security notifications mentioned before or through the Ransomware protection page. In either case, your allowed apps will be able to access all of your files normally. As Microsoft warns, only grant this permission to apps you've personally vetted since you never know when a piece of software could get compromised (and thus compromise all your downstream data).
What about the poor souls that have already been hit by ransomware? Does Microsoft offer any relief for them? Well, sort of. If you're a OneDrive user who regularly backs up your data, then the answer is yes. OneDrive, Microsoft says, features "built-in ransomware detection and recovery tools" (assuming you've linked it to your Windows machine). You can learn more about that tech and how to use it right here.
For everyone else: good luck.
Hopefully, this little PSA has been helpful for at least a few of you. If you decide to use Controlled folder access, be sure to drop a comment below and let us know how you get on. Also, feel free to chime in if you can think of any other methods to protect your data from this sort of attack.
Masthead credit: vchal
