Lack of privacy: Privacy feels like a rarity these days, but with enough care and effort, it's possible to mostly obscure your digital footprint from giant tech companies and world governments alike. At least, that's been the case so far. Researchers from France, Israel, and Australia have teamed up to prove that even the most strict privacy safeguards might not be enough to close all tracking loopholes. As it turns out, your own computer hardware might end up working against you.
The researchers in question have developed a method of device identification that they call "DrawnApart." This strategy takes traditional browser fingerprinting tech, which tends to become obsolete the longer a fingerprint is in use and kicks things up a notch by identifying a user's device based on the "unique properties" of its GPU stack.
Ordinarily, browser fingerprints tend to get confused over time as users with similar devices with similar hardware enter a given website. GPU fingerprinting seeks to find the "slight differences" induced by each video card's manufacturing process; the differences that can't be easily masked or obfuscated.
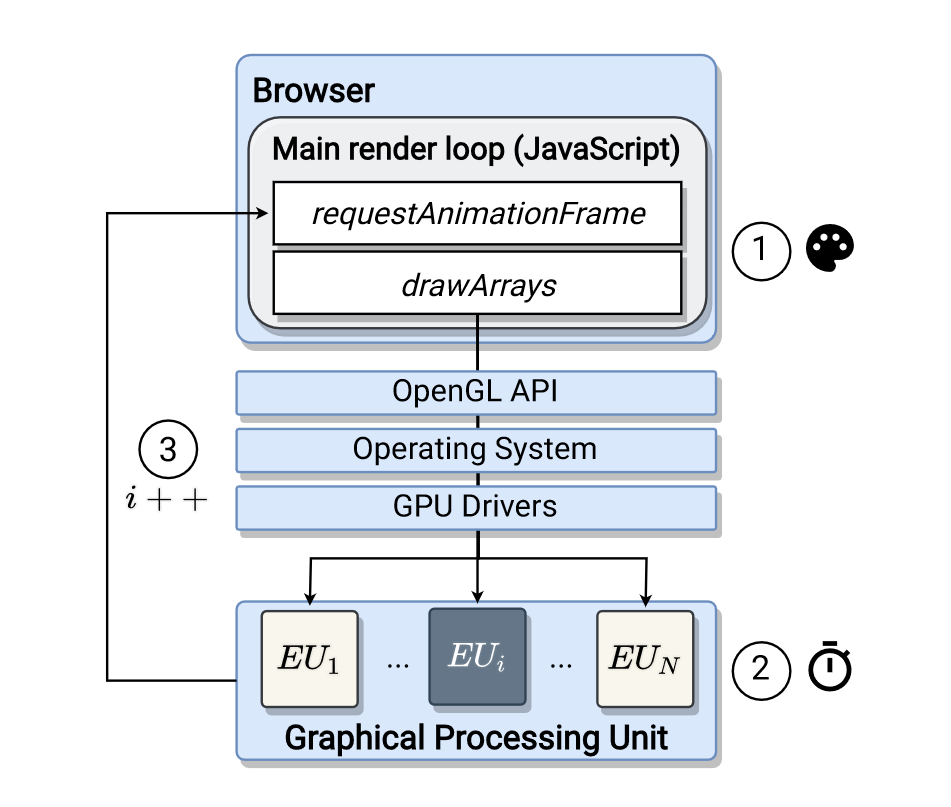
So, how does DrawnApart work on a slightly more technical level? According to researchers, it first generates a "sequence of rendering tasks," each of with target different "Execution Units" on a user's GPU. The results of these tasks – a fingerprint trace – are then fed to a machine learning network, which transforms said trace into an "embedding vector." This vector describes the fingerprint and can point an adversary (the person or entity using this technique) toward the specific device that generated it.
DrawnApart's workloads are generated using WebGL, the graphics library responsible for rendering across countless websites. The workloads in question are designed to pick out the most minute differences in power consumption and processing power across GPUs. Even if their make and model are identical, every card will process the rendering of WebGL points (single-vertex objects) and handle stall functions a little differently. You can see an example of these small differences in the trace image below, which compares to seemingly identical GPUs.
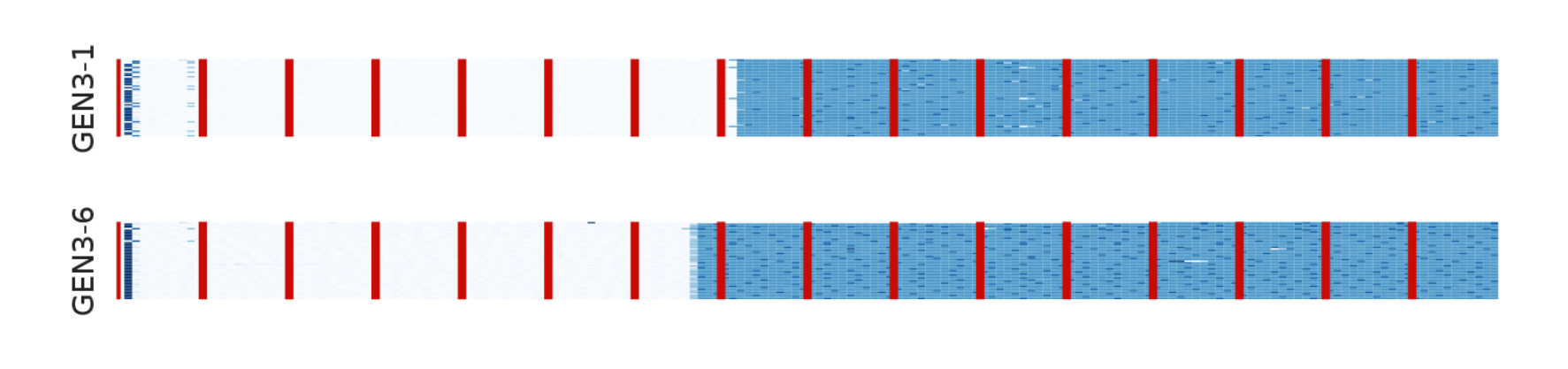
Researchers used DrawnApart to collect 50 traces from both devices, with each individual trace consisting of "176 measurements of 16 points." Those measurements are then organized into 16 groups of 11, and each group "stalls" a different point. The time it takes the GPU to render each point is displayed using a color gradient ranging from pure white to a deep blue, with the former representing a faster render (almost 0ms) and the latter representing a slower one (up top 90ms). The red bars you see in the image above are only used to separate the groups, which is why they remain consistent across both traces.
As you can see, there are distinct differences between these two traces. Researchers note that some of these variations are to be expected since even the same device won't always perform identically. However, despite that, the team feels these traces show patterns that are distinct enough to allow them to distinguish between two identical cards. Naturally, this level of granular measurement allows for highly-accurate fingerprinting that can track users over a much greater length of time than traditional methods. When combined with a "state-of-the-art" tracking algorithm, Bleeping Computer reports, Drawn Apart increases the length of time a target can be followed by up to 67 percent (28 days versus the normal average of 17.5 days).
So... Why perform this research at all? If these researchers are so concerned with user privacy – which they claim to be – why give advertisers and other bad actors the keys to the kingdom, so to speak? The team hopes that by exposing these potential privacy loopholes, the folks behind graphics libraries like WebGL or the upcoming WebGPU API will consider the implications their tech could have on user privacy, and build in safeguards sooner rather than later.
Either way, this research is interesting and poses some serious concerns for the future of web privacy. We look forward to seeing what comes of it in the future, for better or worse.
