Why it matters: Although browser extensions can be useful, downloading them always comes with some amount of risk because they are common vectors for malware. McAfee's recent investigation into a group of Chrome extensions shows that even popular ones could be fronts for scams.
This week, a report from McAfee's security researchers highlighted five Google Chrome extensions that tracked users and manipulated the websites they visited. Collectively, almost a million and a half users installed the extensions.
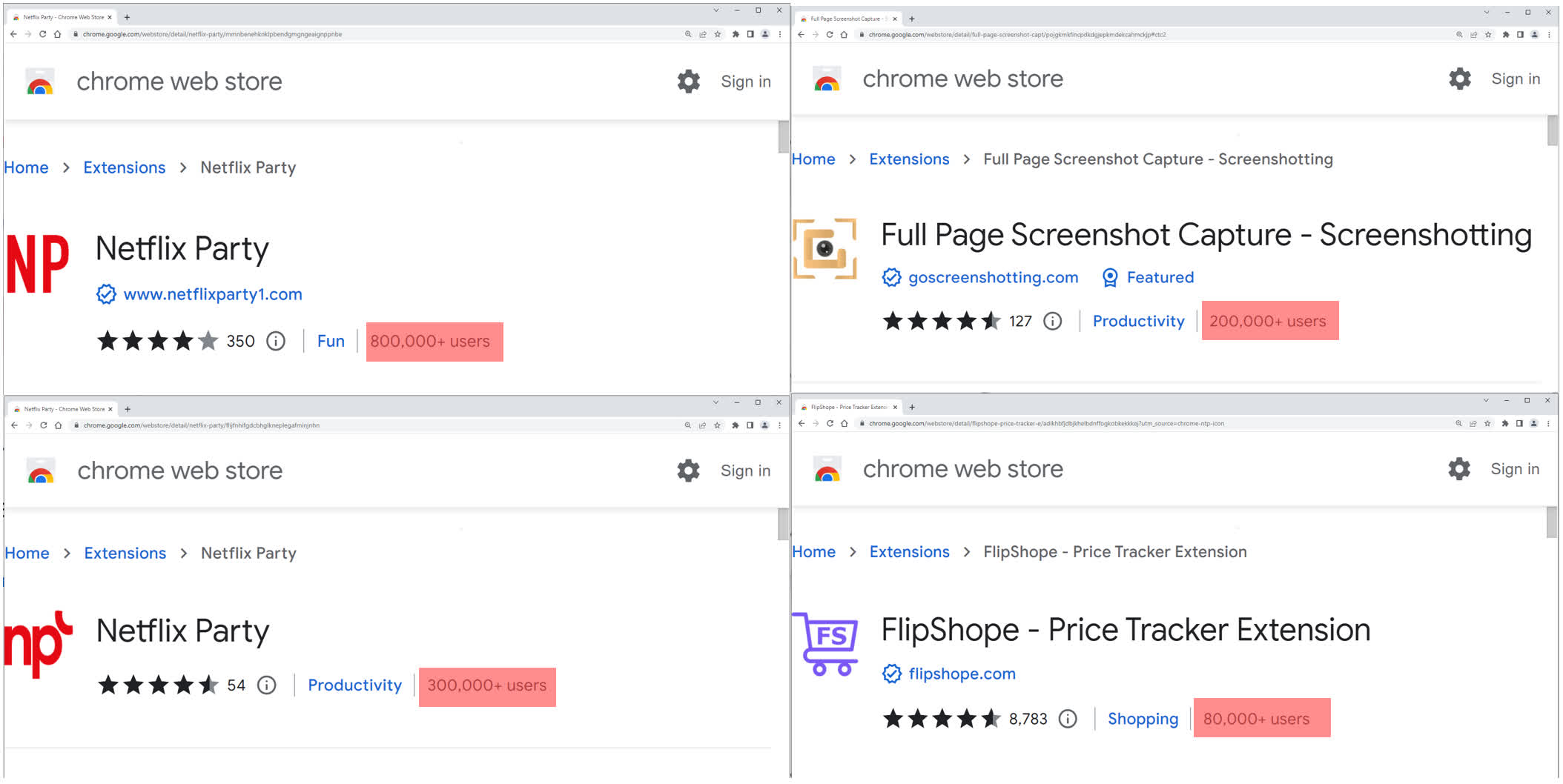
Two of the extensions masqueraded as functions letting users hold Netflix watch parties, while another impersonated a screenshot capture extension. Most pertinent to the scammers' goals were extensions for price tracking and automatically detecting flash sales.
Ultimately, the malware sought to steal affiliate sales commissions from websites where their victims shopped, such as bestbuy.com (shown in the video above). After installation, the extensions would track users' browsing activity and send it to the scammers' servers.
Then, the scammers would add code manipulating the users' cookies and redirecting them to fraudulent URLs. When a target purchased something on an affected website, the extension developers got a cut of the sale by fooling the website into thinking they directed the victim there. Some of the extensions tried to avoid security programs by delaying their malicious activity until 15 days after installation.
Google has already removed the fraudulent extensions from Chrome's web store, but users should check if they've installed the following and uninstall them immediately:
- Netflix Party
- Netflix Party 2
- FileShope - Price Tracker Extension
- Full Page Screenshot Capture - Screenshotting
- AutoBuy Flash Sales
McAfee's recent findings are only the latest examples of extensions that track users to hijack their shopping activity. In March, the company reported on another group of extensions that redirected users to phishing websites to steal gift card codes.
Like the fraudulent extensions from this month, the scams from March masqueraded as watch party apps. The extensions would monitor users' browsing habits and redirect them when they navigated to the gift card pages for stores like Target, Macy's, Nike, and others. The developers also created fake review websites to inflate the extensions' review scores on Chrome's web store, faking an air of authenticity.
When downloading extensions, even popular ones with high review scores, users should always check what permissions they grant. It's also a good idea to search lists of known fraudulent extensions.