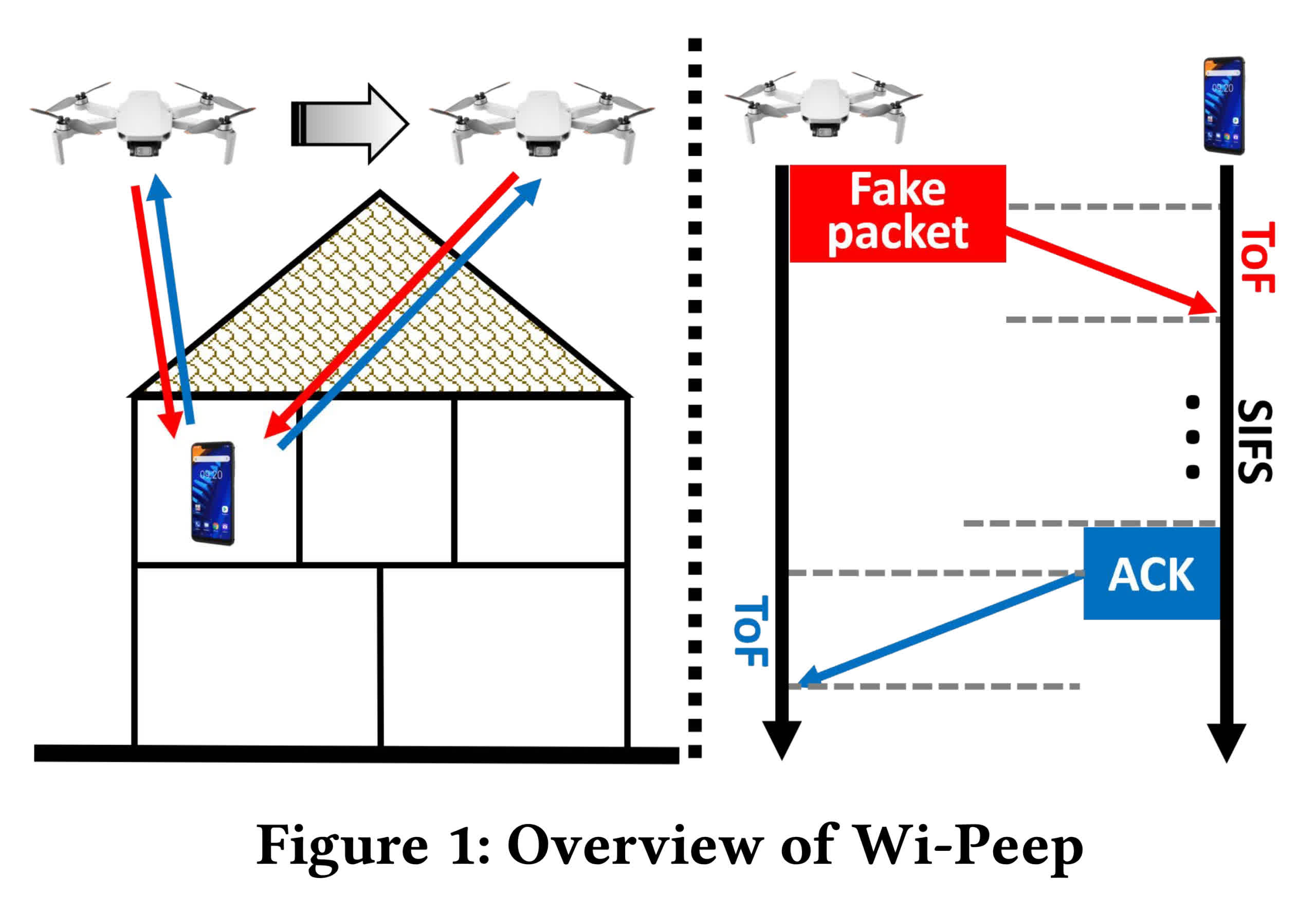
In brief: Researchers have found a WiFi security flaw that can allow hackers to locate and track devices through walls with an accuracy of 3.3 feet. The attack uses a loophole in smart devices that the researchers call "polite WiFi."
The University of Waterloo research team explains that smart devices automatically respond to contact attempts, even on a password-protected network. So they developed a drone they call "Wi-Peep" that sends out several signals as it flies and then measures the response times. This technique allows it to triangulate network devices to within a meter of their position and can also be used to track moving devices like cell phones.
"The Wi-Peep devices are like lights in the visible spectrum, and the walls are like glass," explains Dr. Ali Abedi, an adjunct professor of computer science at Waterloo. "Using similar technology, one could track the movements of security guards inside a bank by following the location of their phones or smartwatches. Likewise, a thief could identify the location and type of smart devices in a home, including security cameras, laptops, and smart TVs, to find a good candidate for a break-in."
Even more unsettling is that attackers can remain virtually invisible to their target since they can operate a camera-equipped drone from a hidden location. An adjacent building or a van parked down the street are suitable covert surveillance opportunities. Even if the victim spots the drone (which is not likely), there would be no way of pinpointing the operator.
Whatsmore, the Wi-Peep was effortless and cheap to build. The researchers only had to fit an off-the-shelf drone with about $20 worth of "easily purchased hardware."
Unfortunately, there is no mitigation for this type of attack yet. The polite WiFi loophole exists to make communication between devices seamless. It allows your phone to transfer files to your computer or another phone or your WiFi-only smartwatch to receive calls made to your phone. So without entirely revamping the whole system, there is not much that users or admins can do other than turn off WiFi.
That said, the Waterloo team is encouraging WiFi chip manufacturers to at least incorporate random variations in response times. If the signals return randomly, the method cannot accurately calculate a device's position.
Camera-equipped drones outfitted with WiFi-enabled spying components are becoming more popular. Last month a financial firm discovered attackers had used two modified drones to infiltrate its network from outside the building. Security analysts say using drones to crack networks has become more common in recent years.
The team published their study with the Association for Computing Machinery. It is available for free on the ACM website.
