The big picture: Microsoft's requirement that PCs support TPM to install Windows 11 made the operating system's 2021 launch controversial. Since then, security flaws, requirement workarounds, and other problems with TPM have called its necessity for Windows 11 into question. A newly discovered vulnerability threatens to completely compromise the protection layer in some AMD processors.
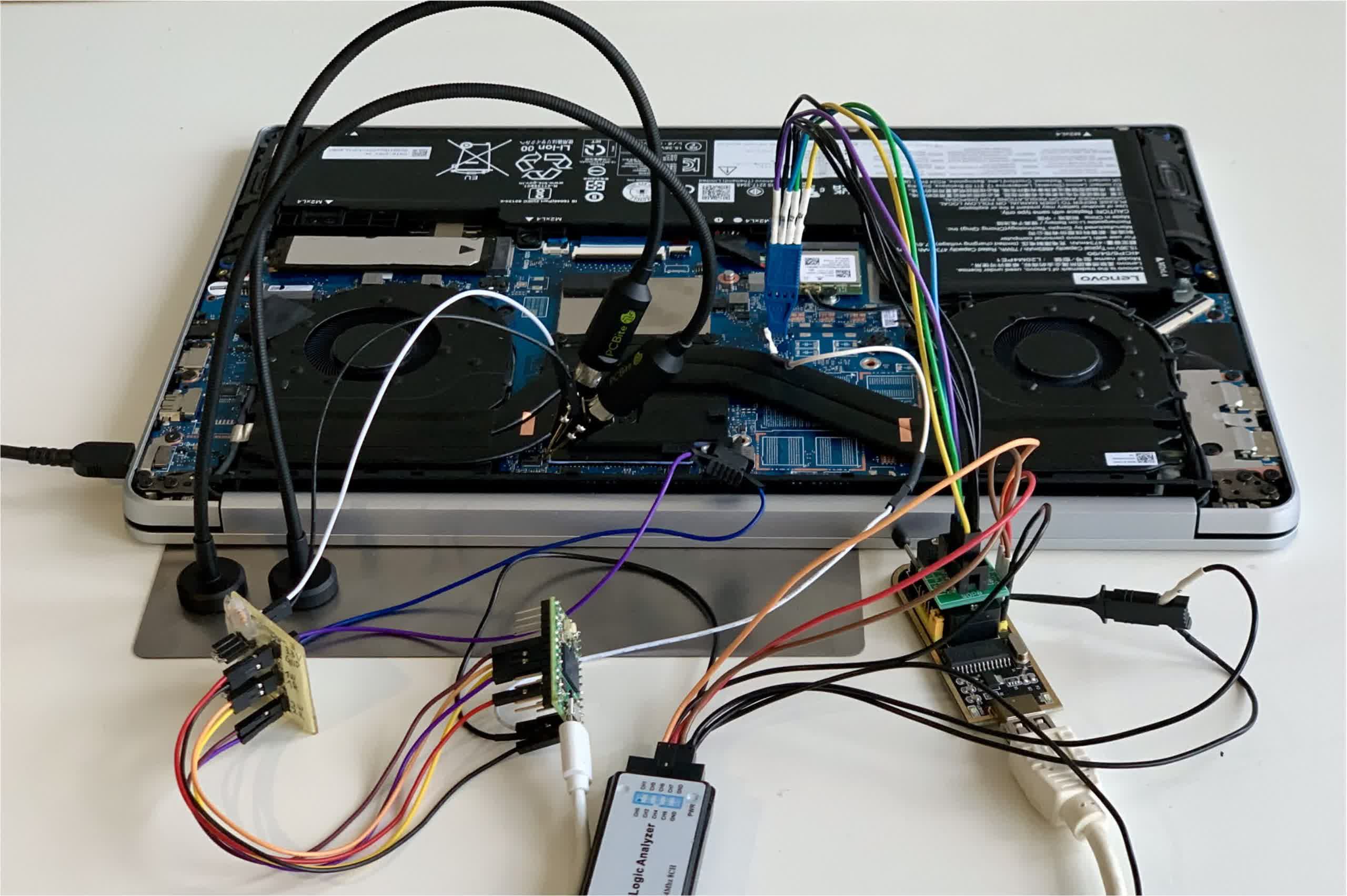
A new research paper explains vulnerabilities in AMD SoCs that could let attackers neutralize any security from their TPM implementations. The attacks can expose any cryptographic information or other credentials TPM guards.
Trusted Platform Module (TPM) adds a layer of security to CPUs that cordons off sensitive information like encryption keys and credentials, making it harder for hackers to access them. In systems using the feature, it's the mechanism behind PINs used to log in to Windows. Traditionally, TPM incorporates a physical chip on the motherboard, but many processors also incorporate a software-based version called firmware TPM (fTPM) that users can easily activate through the BIOS.
The security feature sparked controversy when Microsoft made it mandatory for installing and receiving official updates for Windows 11. Many older CPUs, which could otherwise handle Windows 11 without issue, lack TPM, forcing owners to either undergo expensive upgrades or resort to somewhat complicated methods for circumventing the requirement.
Earlier issues with TPM made Microsoft's insistence appear even worse, but researchers at Technische Universität Berlin – SecT and Fraunhofer SIT recently discovered an exploit that could completely neutralize fTPM. Successful attacks could enable arbitrary code execution and extraction of cryptographic information.
One attack method involves a voltage fault injection attack in which manipulating the power supply can force a Zen 2 or Zen 3 CPU to accept false information, allowing attackers to manipulate the firmware. Another is a simpler ROM attack leveraging an unpatchable flaw in Zen 1 and Zen+ processors.
The vulnerabilities seriously threaten security methods that rely entirely on TPM, like BitLocker. The researchers believe that a strong passphrase is more secure than TPM and a PIN.
Fortunately for users, the attacks require hours of physical access to a target system, meaning they don't involve remote infection through malware. The vulnerability is primarily a problem for lost or stolen devices. The voltage glitch involves about $200 of specialty hardware to manipulate a motherboard, but the ROM attack only needs an SPI flash programmer.