In brief: Tech companies have invested significant time and energy in detecting and blocking suspicious emails based on their text content. However, scammers are finding new ways to evade these security measures, as illustrated by a recent campaign that seeks to steal accounts by sending emails without any text, targeting employees across various industries.
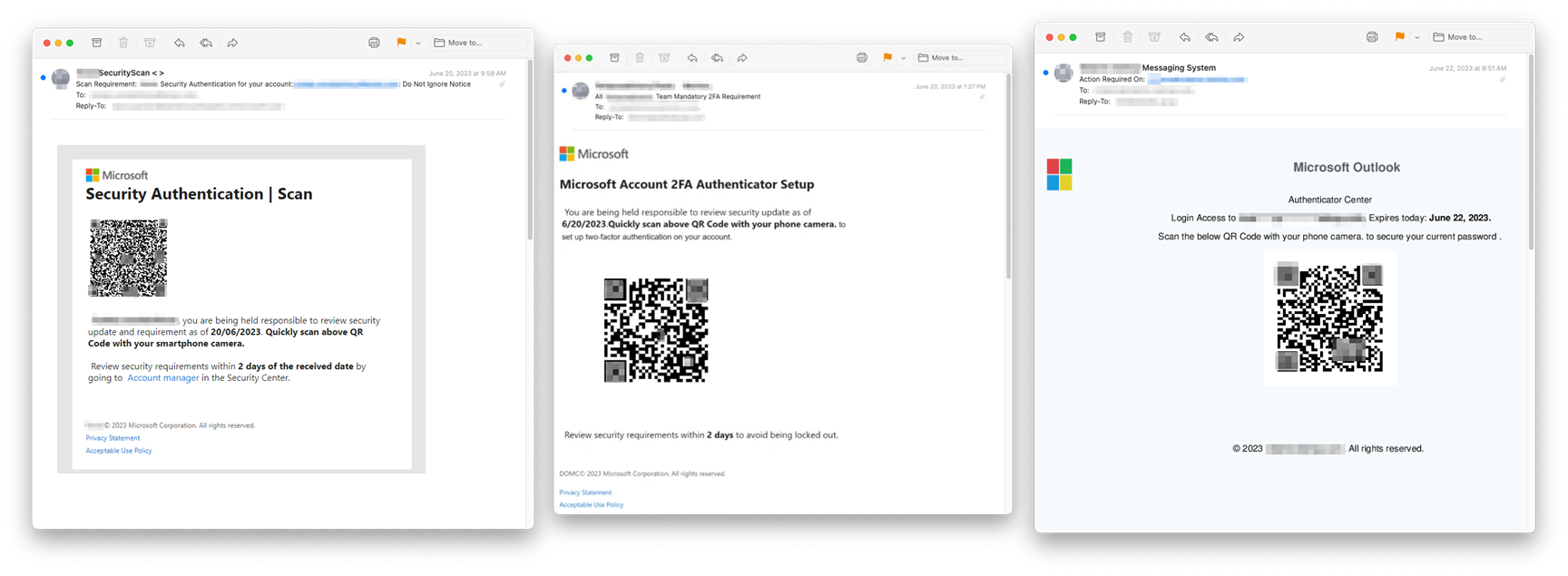
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't appear to have a specific target but all attempt to steal employee credentials.
These malicious emails typically masquerade as either Microsoft support or the victim's employer, often sent from genuine professional accounts that were previously compromised. The emails usually ask the recipient to help with password recovery or two-factor authentication activation, often applying a strong sense of urgency – a common tactic in phishing scams.
Numerous email security systems are configured to detect phishing emails by scanning their text for terms frequently associated with scams. The emails Inky has discovered evade these security measures due to the absence of HTML text.
Instead, the attackers craft the email body within an image attachment. Email platforms automatically display this in the primary field, deceiving recipients into believing that the image is the actual email. Inky counteracted this tactic using OCR (optical character recognition), which scans and extracts text from images and PDFs, thereby making them identifiable by other spam filters.
The messages also include embedded QR codes, which direct victims to phishing websites mimicking Microsoft account login screens. The attackers then proceed to steal login credentials. These counterfeit pages are convincingly designed, and the URLs contain the recipients' email addresses to create a false sense of legitimacy.
Inky has encountered over 500 such emails aiming at a diverse range of organizations in both the US and Australia. Victims include a land surveyor, a flooring company, non-profits, wealth management companies, consultancies, and more. The broad target base suggests the attackers are casting a wide net to increase their chances of success.
When an email asks for account information, users should meticulously inspect the sender's email address and the URLs of any pages that resemble login screens. If feasible, reaching out to the sender through alternative communication channels is an effective way to validate the email's origin. it goes without saying that you shouldn't scan QR codes from unknown sources.