There are many reasons why you'd want to check if an unauthorized party is using your wireless network. It may be that you're experiencing a slower than normal Internet connection or you simply don't want anyone getting a free ride while you pay the bill. Of course, there are also security implications if this person can somehow access files on your network, and even legal implications if he uses your connection for piracy or other illicit activities.
Whatever the case it's better to stay on the safe side. Many of you may have already taken some basic precautions when setting up your wireless network and know your way around troubleshooting these issues. This brief guide is aimed mostly at novice users in need a hand to find out if, indeed, their Wi-Fi is being stolen.
Check the devices associated with your router
The first thing you need to do is login to your router's administrative console by typing its IP address directly into the browser address bar – typically 192.168.0.1 or 192.168.1.1 depending on which router you have. If you don't know your router's default address check out this guide or simply go to the command prompt (Start > Run/Search for cmd) and enter ipconfig. The address you need should be next to Default Gateway under your Local Area Connection.
Alternatively, if you are on a Mac, you can find the default address by going to Network under System Preferences. It should be listed right next to "Router:" if you are using Ethernet, or by clicking on "Advanced..." and heading to the "TCP/IP" tab if you are using Wi-Fi. Next, point your browser to that address and enter your login details – if you haven't changed the default settings it should be a combination of "admin" and "password" or blank fields. Here's a default username and password list (PDF) you might find useful, but we recommend you change this afterwards.
Once inside your router's administrative console look for a section related to connected devices or wireless status. In my old DIR-655 from D-Link it's available under Status > Wireless but you'll find it as "Attached Devices" in Netgear routers, under DHCP Clients Table on Linksys routers, "Device List" if you are using the Tomato firmware, and so on.
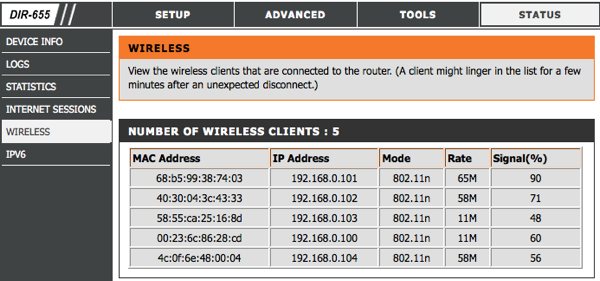

DHCP client list examples on D-Link and Linksys routers.
This should provide a table with the IP, MAC address and other details of every device currently connected to the router. Check that list against your gear to find any intruders. You can find out the MAC/IP address of your computers by going to the Command Prompt again and entering 'ipconfig /all'. The MAC address will be shown as the physical address. I'll let you figure it out for mobile devices like smartphones and media players since I can't possibly list all options.
Taking action
The best and simplest solution is to set up a strong password using WPA2 or WPA – WEP is very easy to crack so avoid that if possible. There are some other methods you can use to beef up security, like switching off the SSID broadcast (which prevents it from advertising the name of your network to nearby Wi-Fi devices) or setup a filter for allowed or blocked devices by MAC address. It won't stop the most determined intruder but it will slow him down.
That should be more than enough for most users but if you need to actually track down who's been breaking into your network it's possible to pinpoint his physical location using a tool called MoocherHunter. You'll need to burn a Live CD to boot your laptop with and walk around to track down unauthorized wireless clients. According to the program's description, it detects traffic sent across the network and can find the source within 2 meters accuracy.
Needless to say, we're not suggesting you take matters into your own hands, but it might come in handy if someone is getting you in trouble with authorities using your network for illegal purposes – or simply to have a cool story to tell.
Bonus: Profit by setting up a paid Wi-Fi hotspot
If it doesn't bother you to have someone piggybacking on your connection you might as well get something in return, right? Chillifire is a good third-party firmware alternative if you want to run a public hotspot, as it allows you to offer for-pay or free Internet access points from your consumer router. Alternatively, you can get a Fonera router, which gives you free roaming at Fon Spots worldwide in return for sharing a little bit of your WiFi at home.
Must see: The best routers reviewed and rated.
