Facepalm: Apple's iOS 15 (and iPadOS 15 by nature) has been an extremely buggy release. In addition to several flaws that crippled iPhone 13s, the operating system has had at least two actively exploited zero-day vulnerabilities that Apple engineers had to patch quickly.

On Monday, Apple issued an urgent security fix for a zero-day flaw in iOS 15 and iPadOS 15 that hackers are actively exploiting. The patch came the same day it released iOS 15.0.1.
The bug (CVE-2021-30883) causes a memory-corruption error in the IOMobileFrameBuffer, a kernel function that allows developers to allocate how their apps use system memory to control the display.
"An application may be able to execute arbitrary code with kernel privileges," read Apple's patch notes. "Apple is aware of a report that this issue may have been actively exploited."
The patch notes did not go into great detail about the bug. However, shortly after Apple released iOS and iPadOS 15.0.2, security researcher Saar Amar published a blog post explaining the exploit and created a proof-of-concept (POC) to show that it works "100 percent of the time." Amar said the flaw is "great for jailbreaks" because it is accessible from the app sandbox.
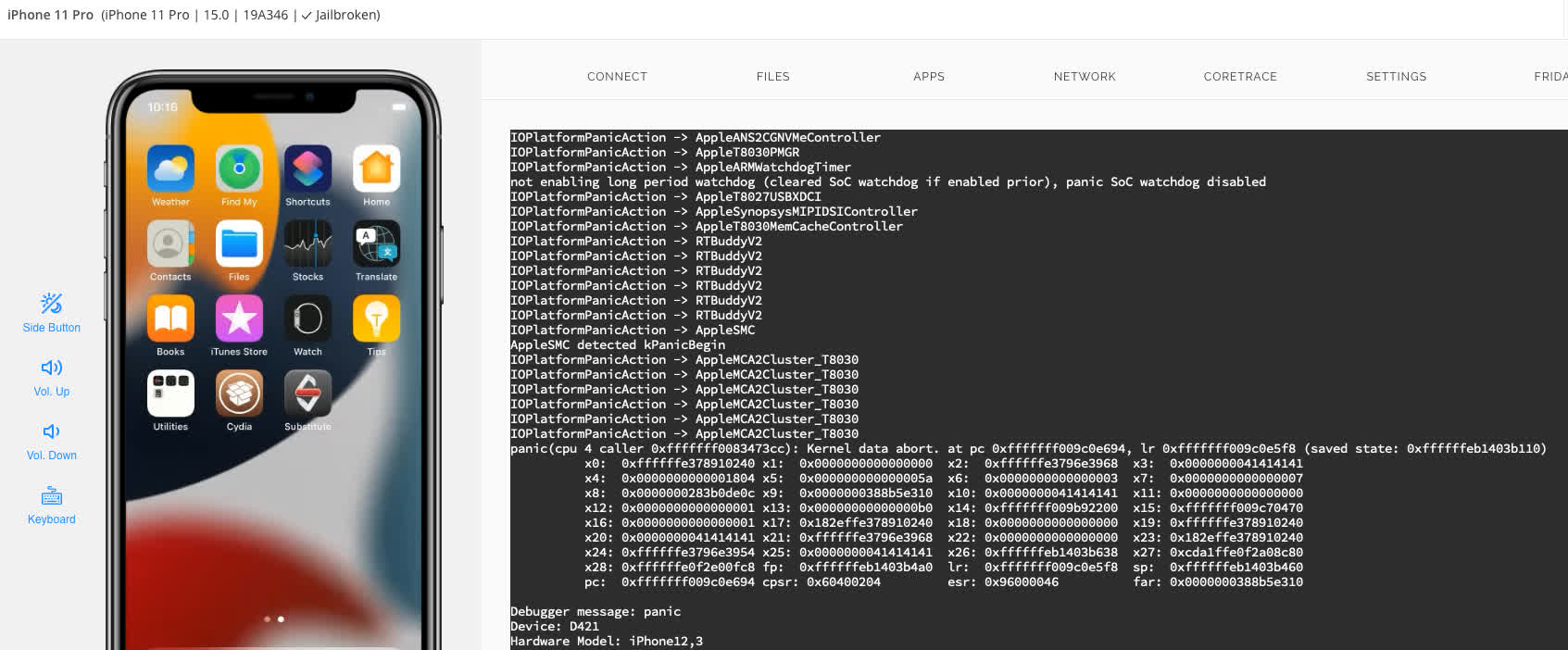
Example of panic triggered by Amar's POC (Click image to enlarge).
After examining the BinDiff (a tool that shows differences in disassembled binaries), Amar concluded that the flaw was not just good for granting kernel privileges but could also be used for LPE (local privilege escalation) exploits.
He tested his very simple (one page of code) POC on iOS versions 14.7.1 (physical iPhone X) and 15.0 (virtual iPhone 11 Pro) but said the bug is likely much older than that. He ran the code five times on each device, and the POC triggered a panic in every instance. Amar's code caused integer overflows in areas other than the IOMobileFrameBuffer, but the patch also seems to have corrected those.
"An interesting important note is that other implementations of these functions in other classes also had this integer overflow," Amar wrote. "As far as I can see, the patch fixed these as well."
Aside from the jailbreaking potential, this security flaw is similar to the nasty one (CVE-2021-30807) that Apple patched in July. Malicious attackers could use the bug to hijack the device completely (and apparently are). So it's best to install the patch as soon as possible.
https://www.techspot.com/news/91743-apple-rushes-out-ios-1502-hours-after-1501.html