Why it matters: A botnet of over 100,000 devices can cause a great deal of harm with ease. In this case, mass generation of spam appears to be the goal. Router manufacturers have known about the flaw being used to exploit their products for years, but consumers either cannot or simply are not updating their firmware.

A collection of more than 100,000 routers have two things in common. First, they are utilizing a Broadcom chipset, but more more importantly, they all have a UPnP vulnerability that allows devices outside of a local network to elicit a response from inside. The end result is control over the routers to form a sizable botnet.
Discovered by Netlab 360 researchers, the BCMUPnP_Hunter botnet is believed to be used for sending spam emails. A built-in proxy network connects to Hotmail, Yahoo Mail, and Outlook services. Unlike other botnets, this one does not appear to be used for performing DDoS attacks.
In total, there have been 116 different routers that have been successfully infected. Manufacturers including Cisco, TP-Link, D-Link, Netgear, Asus, ZTE, and several more lesser known brands are affected. Even though the UPnP vulnerability in question was first discovered nearly five years ago, it is evident that patches have not been applied if they were even offered.
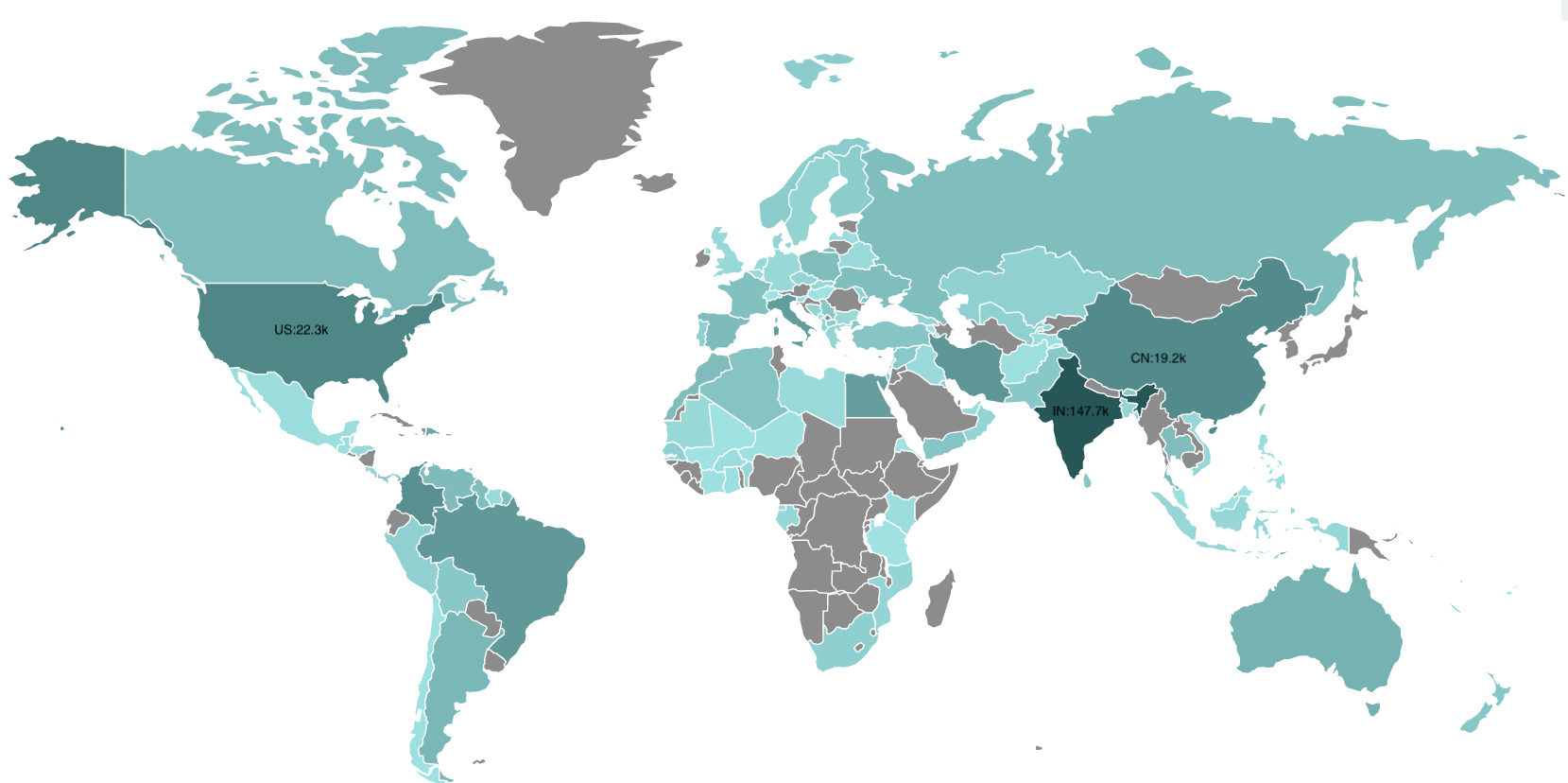
When scanning for IP addresses affiliated with the botnet, single scans have shown around 100,000 infected routers. Over time, 3.37 million IP addresses have been tagged as related. However, dynamic IP addresses are likely the reason for such a high number. Using Shodan, there is an estimated 400,000 devices that remain vulnerable to attack via the UPnP flaw. Below is a heat map of infections over the past week.
Consisting of a shell code acting as a downloader for the main code, researchers have stated that this is not the work of an amateur. Multiple system calls are made in the main code with inversion operations applied to avoid invalid characters from being passed through. The runtime stack structure has also been optimized using different means of multiplexing the stack variables. The main loop has been repeatedly called from carefully selected sections to almost guarantee that the program remains active.
Activity on TCP port 5431 followed by UDP port 1900 are the first steps the malware takes before opening a malicious URL that then triggers the main payload. To get rid of the BCMUPnP_Hunter botnet, updating or flashing firmware on affected routers is recommended.
https://www.techspot.com/news/77395-broadcom-chips-old-upnp-flaw-have-allowed-thousands.html