What just happened? Researchers with Guardio Security uncovered a "vast campaign" of malicious data-collecting browser extensions. The analysts dubbed it "Dormant Colors" because of the malware's focus on color and style themes — Action Colors, Power Colors, Super Colors, and so on. Dormant Colors consists of 30 different extensions that millions of users have downloaded.

The seemingly harmless "helpers" advertise themselves as webpage modifiers, allowing users to change things like background colors and font styles on webpages they visit. However, under the hood, they have several malicious endeavors, including hijacking your search/browsing histories, inserting advertisements within visited pages, and side-loading malicious code without being detected.
The result is a network of infected computers that hackers can use for other nefarious activities.
"It starts with the trickery malvertising campaign, continues with a crafty novel way to side-load the real malicious code without anyone noticing (until now!), and finally with stealing not only your searches and browsing data, but also affiliation to 10,000 targeted sites — a capability that is easily leveraged for targeted spear phishing, account takeover and credential extraction — all using this powerful network of millions of infected computers worldwide!"
All 30 of the identified extensions work in Chrome and Edge. They could be found in Google's and Microsoft's repositories, but both companies removed most entries they confirmed malicious. However, that does nothing for those who still have them installed. Also, since the extensions' code only serves as a ruse, the apps can easily be rebranded and uploaded with another account.
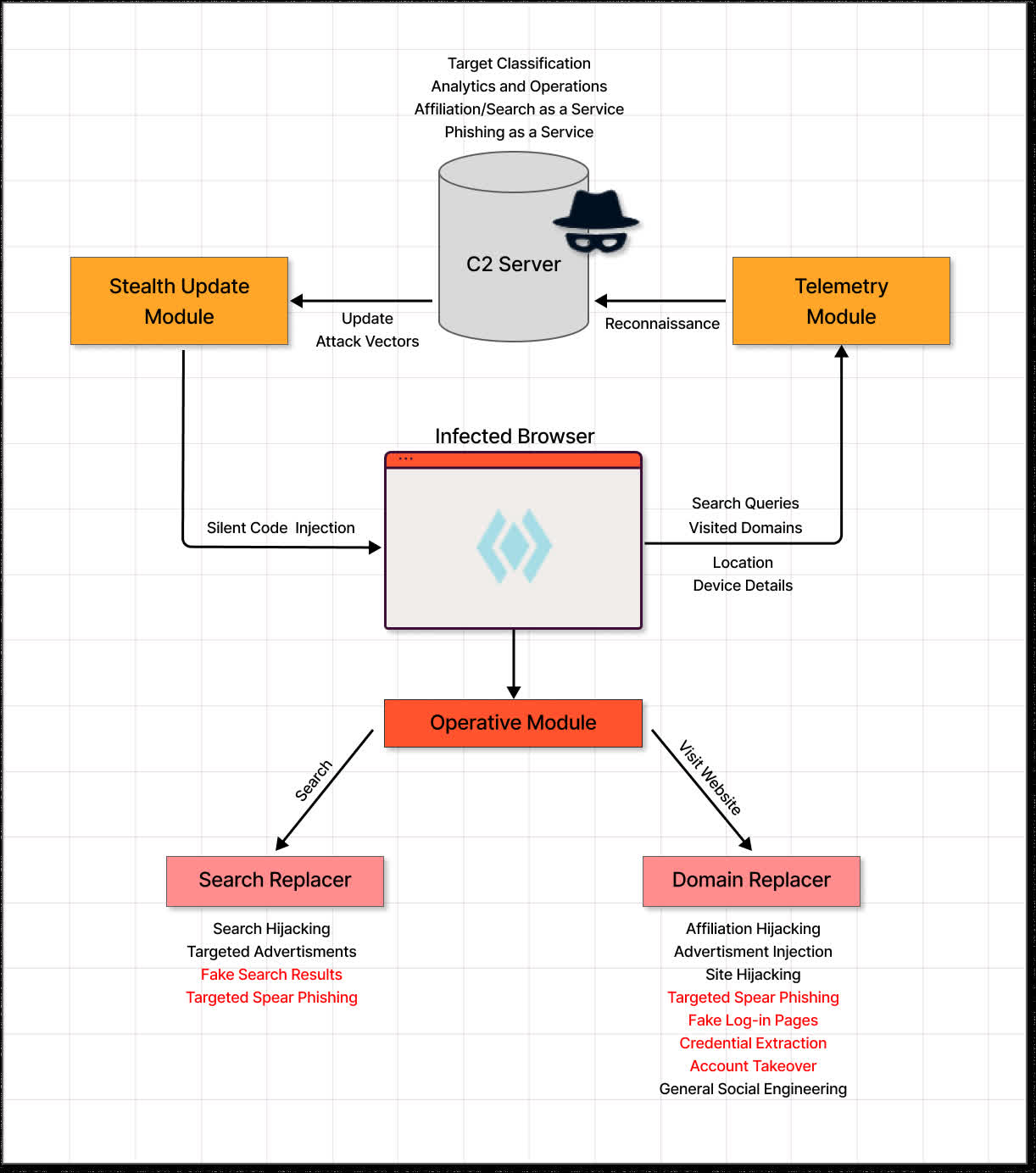
Guardio said the software's nature allows attackers to target individual users or entire domains using fake search results, site hijacking, and targeted spear phishing. It does this by stealing a user's browser data and sending it to a command-and-control server. The hackers can use that data to update the extension with new attack vectors using "silent code injection."
Normally, Google and Microsoft moderators can spot obviously malicious code and reject it before it gets approved. However, the researchers found that the malware operators design the extensions in a fashion that allows it through inspection.
"In its initial state, the extension is harmless. Looking through the code will reveal tons of color and style-related functions with names likecssbgcolors()and setlightmodes()," Guardio says.
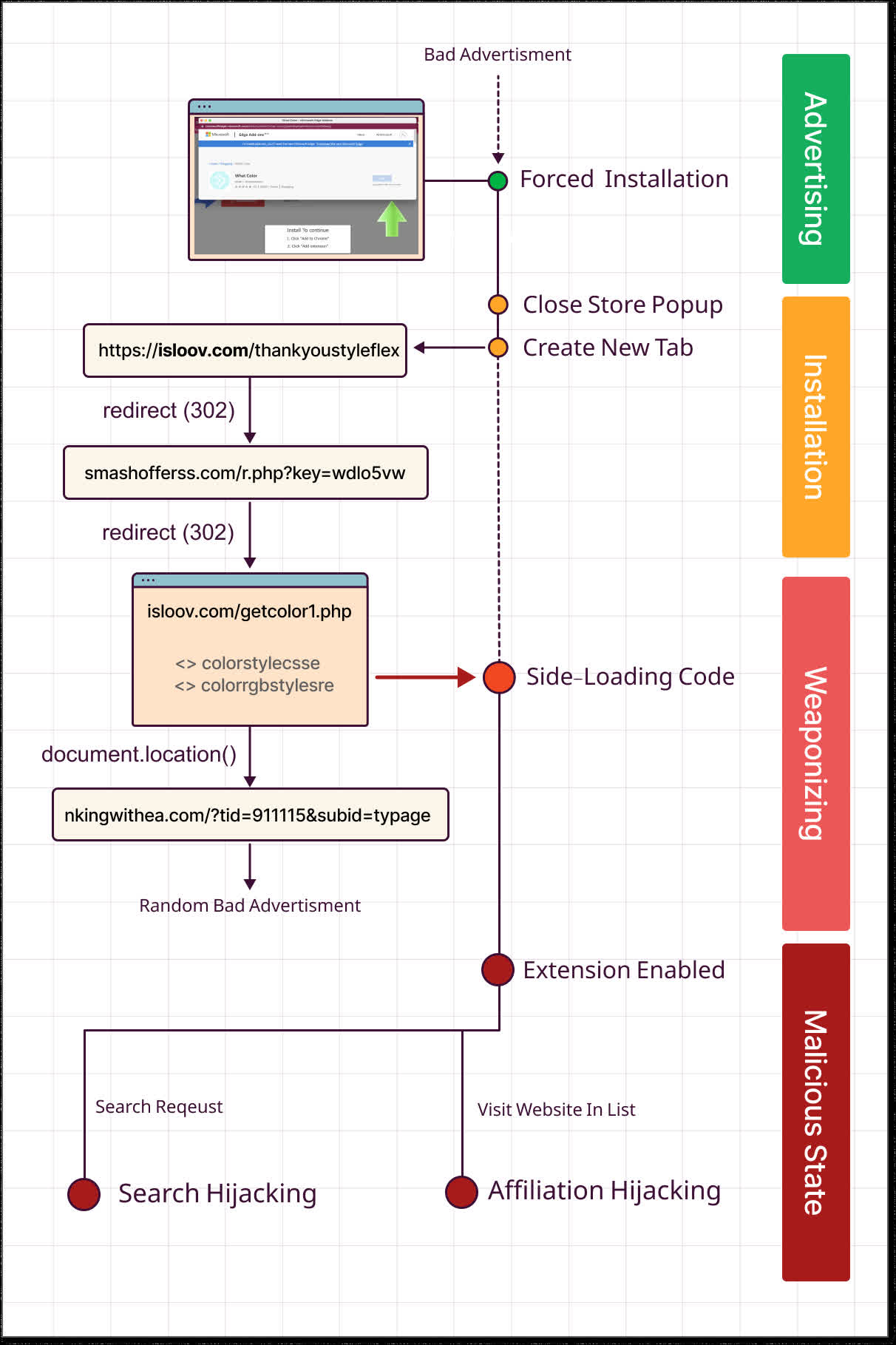
No apparent malicious code is present in what is submitted to the store. The trouble comes from fake web pages that prompt users to install the seemingly harmless extension from the legitimate storefront. The user is then redirected to a "thank you" page and a series of other redirects side load the malware.
The lesson here is to carefully consider what extensions you choose to install in your browsers. Even if they come from a trusted source, they may not be what you expect. And especially remain skeptical anytime a webpage tells you you need to download anything to view its content. That is a clear indication something is wrong and it is astonishing that people still fall for this trick in 2022.
If you have any webpage styling extensions installed on Chrome or Edge, you might want to check out Guardio's fully detailed writeup.
https://www.techspot.com/news/96442-dormant-color-malware-infects-millions-pcs-malicious-chrome.html