In brief: The majority of serious security bugs in Chrome are due to memory safety issues. Google engineers came to that conclusion after analyzing 912 high or critical severity bugs affecting stable channel releases since 2015.

Google notes in this memory safety report that Chromium’s security architecture was designed to assume that such bugs exist, using sandboxes to help stop them from taking over host machines. It’s an effort that has allowed the team to stay ahead of attackers, but just barely. Worse yet, they’re reaching the limits of what is possible with sandboxing and site isolation.
It’s an issue that isn’t limited to Google, either. Most vulnerabilities found in iOS and macOS are also caused by memory unsafety. Microsoft said last summer that 70 percent of the security vulnerabilities it fixes and assigns a CVE (Common Vulnerabilities and Exposures) number are due to memory safety issues. And according to this analysis, more than 80 percent of zero-day vulnerabilities are due to memory problems.
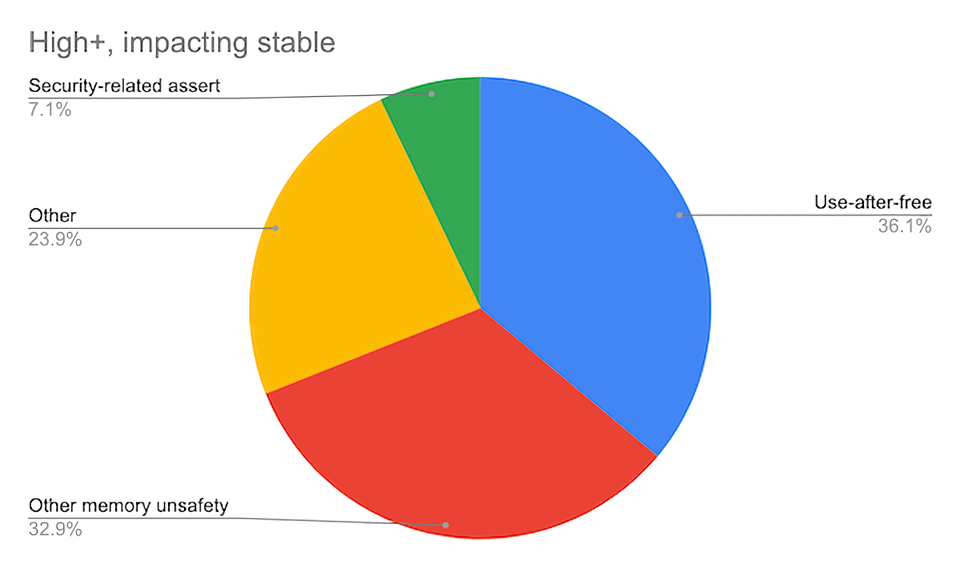
With stronger sandboxing no longer advantageous and deploying additional processes off the table, Google said it must attack memory unsafety problems by “any and all means necessary.” This includes exploring custom C++ libraries and utilizing safer languages like JavaScript, Rush and Swift when applicable.
https://www.techspot.com/news/85368-google-70-percent-serious-security-bugs-memory-safety.html