ok...I really need some help
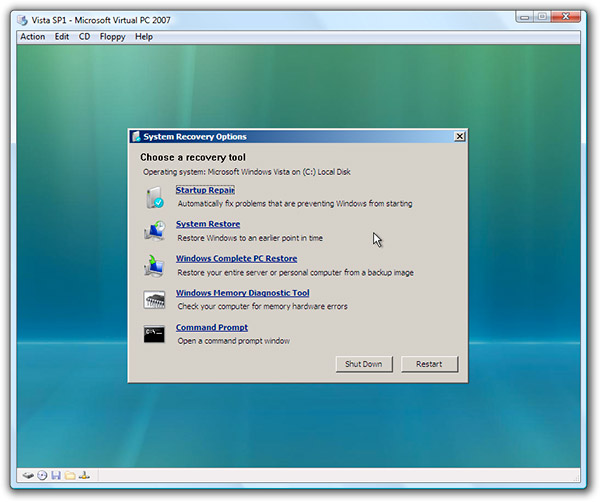
first off...oops... I know it's mentioned not to do any other scans, but I noticed that when I tried to do the scans listed in the "8 step" that Norton Online Security was still on & I couldn't get it to turn off so I used the norton removal tool which took off the online security & my symantec antivirus ... my isp provides a "complete protection" package so I decided to install that instead of the symantec... anyway, now I can't access anything with my wireless on my laptop... it shows that it is connected both local & internet , but nothing works. I have to connect via wire to get the internet to work...
I re-did the scans mentioned & here are the results...
Malwarebytes' Anti-Malware 1.46
www.malwarebytes.org
Database version: 4331
Windows 6.0.6002 Service Pack 2
Internet Explorer 8.0.6001.18928
7/21/2010 8:58:02 AM
mbam-log-2010-07-21 (08-58-02).txt
Scan type: Quick scan
Objects scanned: 143611
Time elapsed: 7 minute(s), 37 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 11
Registry Values Infected: 0
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 3
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
HKEY_CLASSES_ROOT\AppID\{84c3c236-f588-4c93-84f4-147b2abbe67b} (Adware.Adrotator) -> No action taken.
HKEY_CLASSES_ROOT\AppID\{38061edc-40bb-4618-a8da-e56353347e6d} (Adware.EZlife) -> No action taken.
HKEY_CLASSES_ROOT\AppID\{7b6a2552-e65b-4a9e-add4-c45577ffd8fd} (Adware.EZLife) -> No action taken.
HKEY_USERS\.DEFAULT\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\{3446af26-b8d7-199b-4cfc-6fd764ca5c9f} (Backdoor.Bot) -> No action taken.
HKEY_USERS\.DEFAULT\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\{494e6cec-7483-a4ee-0938-895519a84bc7} (Backdoor.Bot) -> No action taken.
HKEY_USERS\S-1-5-18\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\{3446af26-b8d7-199b-4cfc-6fd764ca5c9f} (Backdoor.Bot) -> No action taken.
HKEY_USERS\S-1-5-18\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\{494e6cec-7483-a4ee-0938-895519a84bc7} (Backdoor.Bot) -> No action taken.
HKEY_CLASSES_ROOT\adshothlpr.adshothlpr (Adware.Adrotator) -> No action taken.
HKEY_CLASSES_ROOT\adshothlpr.adshothlpr.1.0 (Adware.Adrotator) -> No action taken.
HKEY_CURRENT_USER\SOFTWARE\Sky-Banners (Adware.Adrotator) -> No action taken.
HKEY_LOCAL_MACHINE\SOFTWARE\Sky-Banners (Adware.Adrotator) -> No action taken.
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
C:\Windows\system32\Drivers\pmlbn.sys (Rootkit.Bubnix) -> No action taken.
C:\Users\William\AppData\Roaming\dhxiuw.dat (Malware.Trace) -> No action taken.
C:\Users\William\AppData\Local\Temp\services.exe (Password.Stealer) -> No action taken.
GMER 1.0.15.15281 -
http://www.gmer.net
Rootkit quick scan 2010-07-21 09:00:10
Windows 6.0.6002 Service Pack 2
Running: 96z8iiv2.exe; Driver: C:\Users\William\AppData\Local\Temp\pwtdipow.sys
---- Devices - GMER 1.0.15 ----
Device \FileSystem\Ntfs \Ntfs 8659D160
Device \FileSystem\Ntfs \Ntfs 84C17758
Device \FileSystem\Ntfs \Ntfs 847E5C40
Device \FileSystem\Ntfs \Ntfs 977E9430
Device \FileSystem\Ntfs \Ntfs 859675C8
AttachedDevice \FileSystem\Ntfs \Ntfs AVGIDSFilter.sys
AttachedDevice \FileSystem\Ntfs \Ntfs dwprot.sys
AttachedDevice \FileSystem\Ntfs \Ntfs trufos.sys
AttachedDevice \Driver\tdx \Device\Ip rp_skt32.sys (Radialpoint Filter/Radialpoint Inc.)
AttachedDevice \Driver\tdx \Device\Ip dwprot.sys
AttachedDevice \Driver\tdx \Device\Tcp rp_skt32.sys (Radialpoint Filter/Radialpoint Inc.)
AttachedDevice \Driver\tdx \Device\Tcp dwprot.sys
AttachedDevice \Driver\tdx \Device\Udp rp_skt32.sys (Radialpoint Filter/Radialpoint Inc.)
AttachedDevice \Driver\tdx \Device\Udp dwprot.sys
AttachedDevice \Driver\tdx \Device\RawIp rp_skt32.sys (Radialpoint Filter/Radialpoint Inc.)
AttachedDevice \Driver\tdx \Device\RawIp dwprot.sys
---- Services - GMER 1.0.15 ----
Service (*** hidden *** ) [BOOT] pmlbn <-- ROOTKIT !!!
---- EOF - GMER 1.0.15 ----